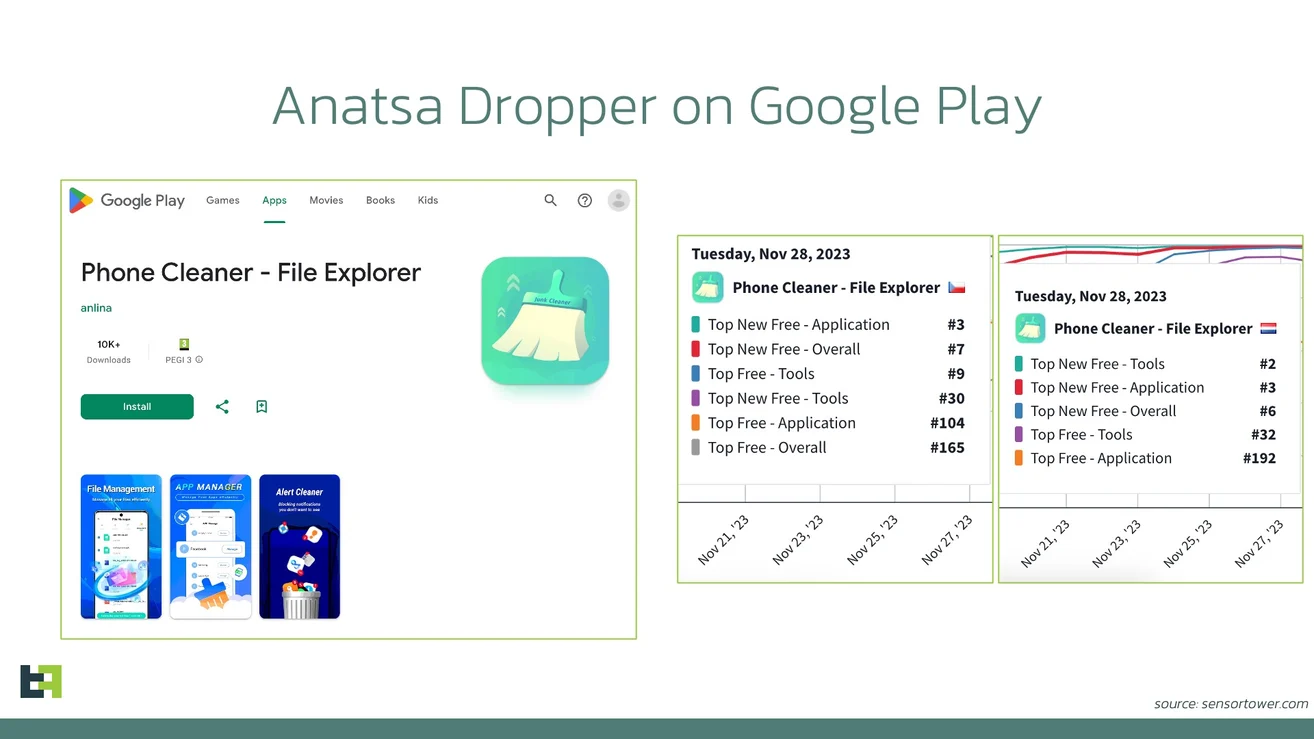
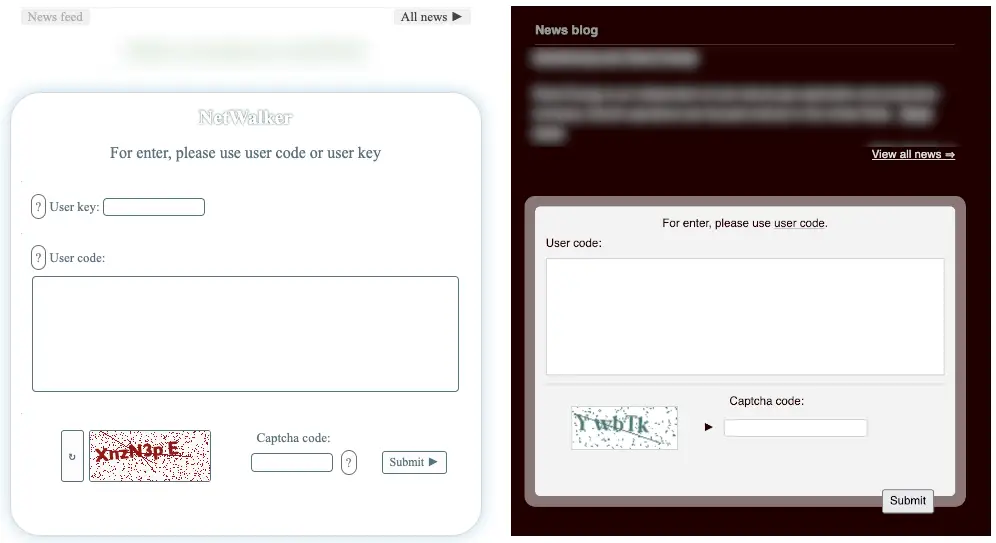
93% of Top Apps Vulnerable to Repackaging Attacks
In alignment with new EU regulations, Apple is introducing the capability for the installation of applications from third-party sources, a move that has raised concerns among experts following the publication of a report on...