NimDoor: North Korean APT Uses Nim-Based Malware for Stealthy Web3 & Crypto Attacks on macOS
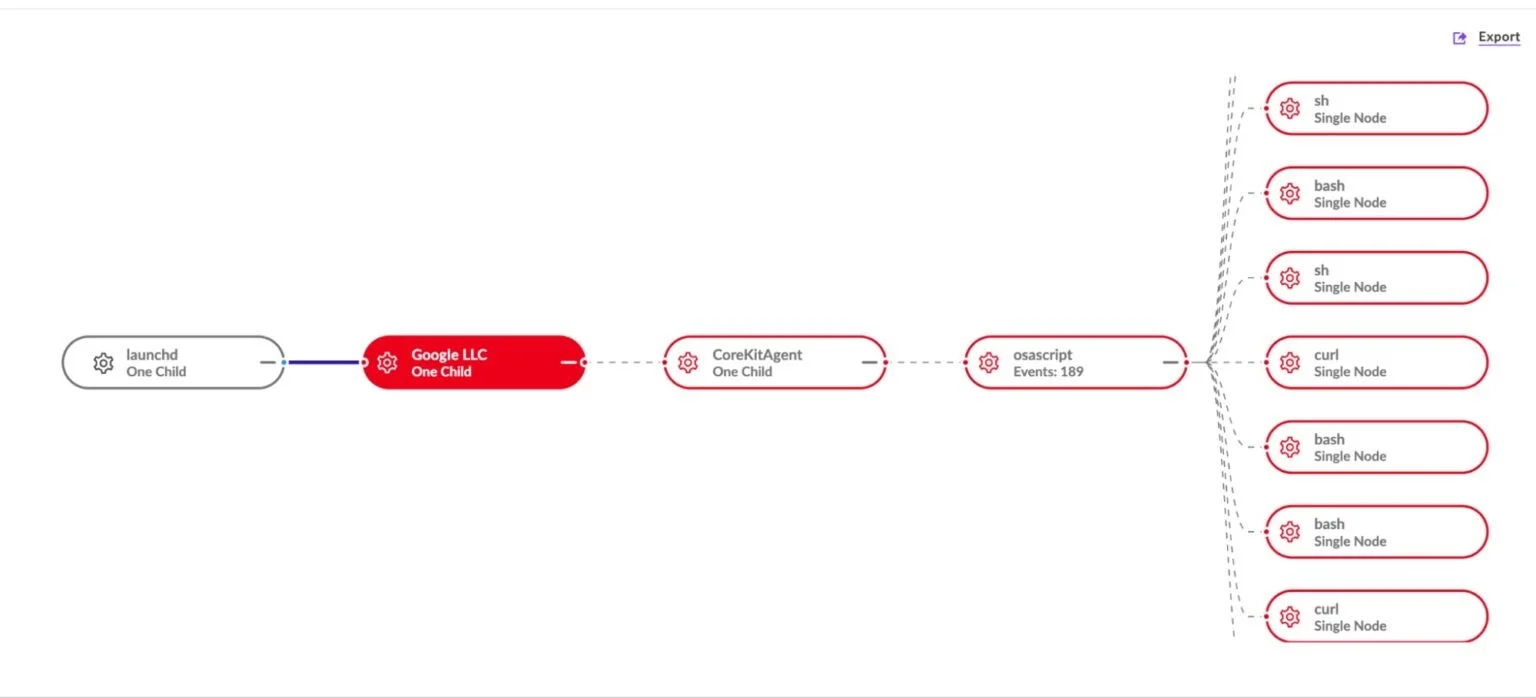
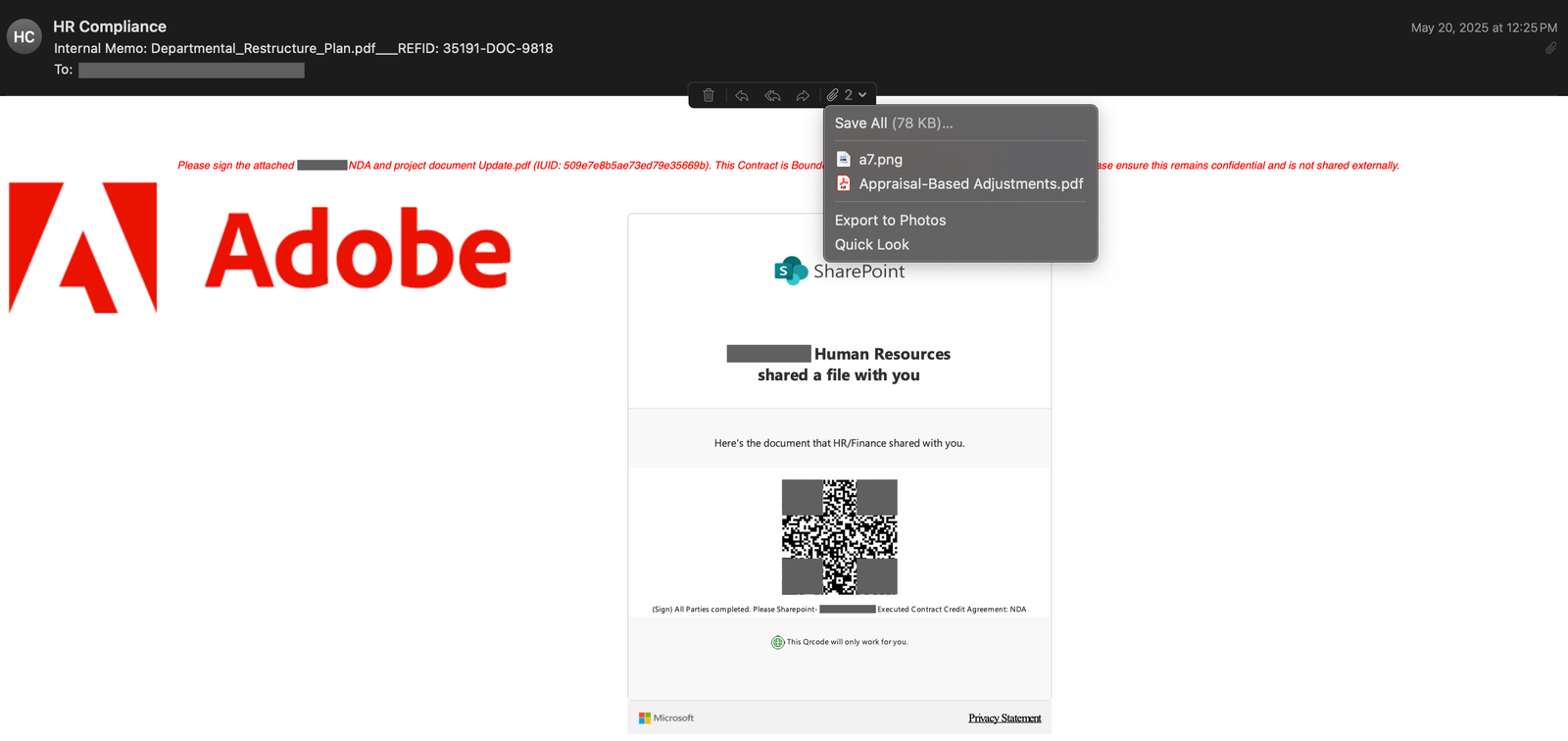
A threat group linked to the Democratic People’s Republic of Korea (DPRK) is intensifying its attacks on companies operating in the Web3 and cryptocurrency sectors, deploying malware crafted in the Nim programming language. These...