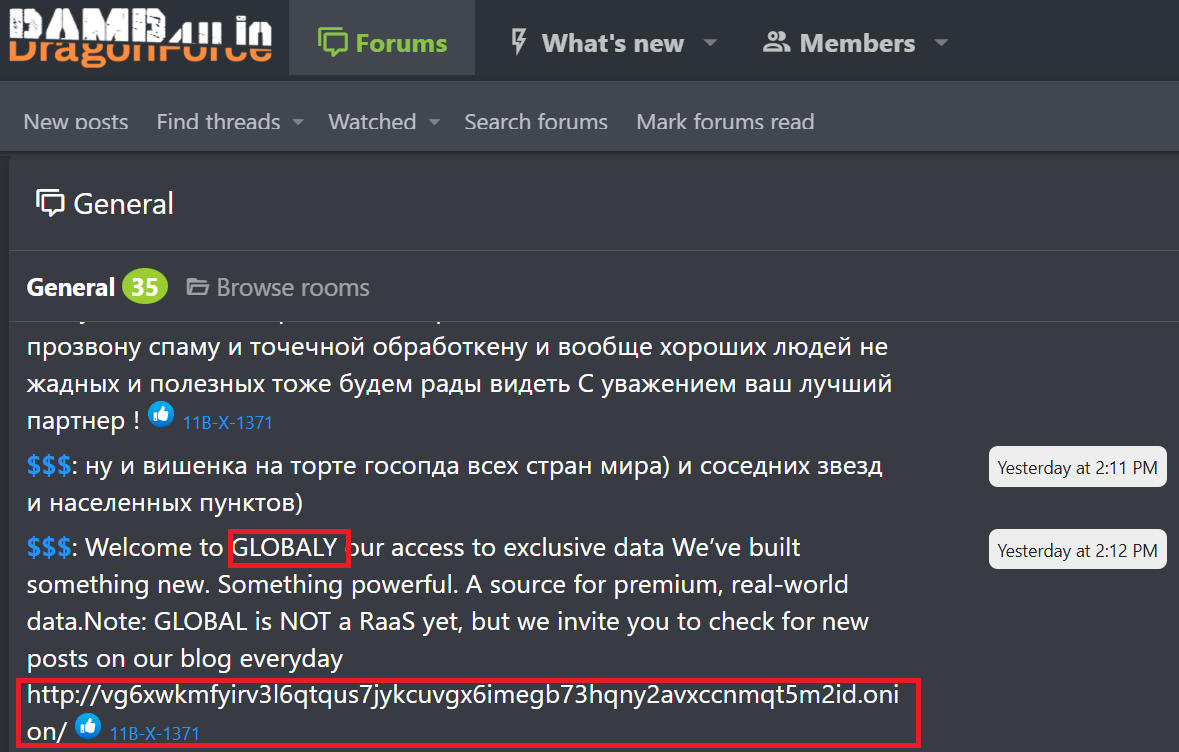
GLOBAL GROUP: AI-Powered Ransomware Threatens Global Critical Infrastructure
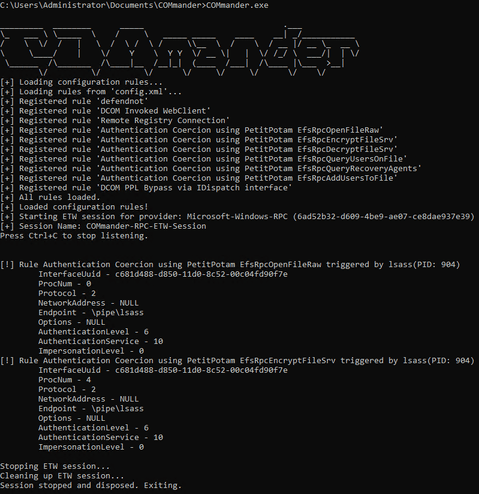
A cybercriminal collective has launched a new Ransomware-as-a-Service (RaaS) platform known as GLOBAL GROUP, actively targeting organizations across Australia, Brazil, Europe, and the United States since early June 2025. According to EclecticIQ, the operation...