Banking Trojans Surge on Google Cloud Run
Analysts warn that hackers have increasingly exploited the Google Cloud Run service for the widespread distribution of banking trojans such as Astaroth, Mekotio, and Ousaban.
Google Cloud Run enables users to deploy front-end and back-end services, websites, or applications, and handle workloads without the need to manage infrastructure or scaling.
Researchers from Cisco Talos have observed a sharp increase in the misuse of Google’s service by malefactors for disseminating malicious software since September 2023. Brazilian hackers initiated campaigns distributing MSI installers to deliver malicious payloads.
Experts suggest that Google Cloud Run has become an appealing platform for cybercriminals due to its cost efficiency and the ability to circumvent standard security measures.
The attacks commence with the distribution of phishing emails to potential victims. These emails are meticulously crafted to be indistinguishable from official banking checks, financial reports, and notifications from government bodies.
Most of the emails are in Spanish, targeting Latin America, though some are in Italian. They contain links redirecting victims to malicious web services hosted on Google Cloud Run.
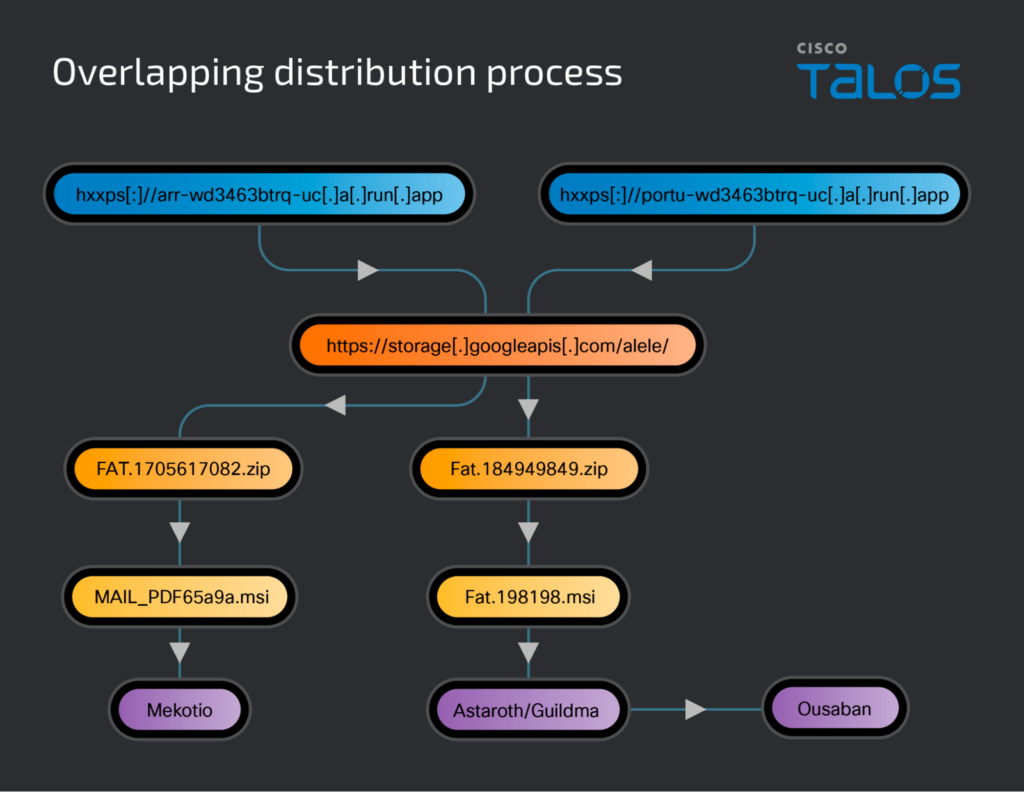
In some instances, the delivery of malware occurs through MSI files. In others, the service issues a 302 redirect to Google Cloud Storage, where a malicious MSI-containing ZIP archive is located.
Upon executing the MSI files, new components of the trojan are downloaded and installed. The delivery of the second stage is facilitated using the legitimate Windows tool BITSAdmin.
Finally, the software establishes a persistent presence in the victim’s system by adding LNK files to the startup folder. These are configured to execute a PowerShell command that runs a malicious script.
The campaigns feature three banking trojans: Astaroth/Guildma, Mekotio, and Ousaban, each designed to covertly breach systems, establish a persistent presence, and steal confidential information to access victims’ bank accounts.
Astaroth employs advanced detection evasion techniques. Initially targeting Brazil, it now attacks over 300 financial organizations in 15 Latin American countries. Recently, the trojan began gathering data for accessing cryptocurrency exchange services.
By intercepting keystrokes, capturing screens, and clipboard data, Astaroth not only steals confidential information but also monitors internet traffic to pilfer login credentials for banking accounts.
Mekotio, active for several years and targeting Latin America, hacks into bank accounts and conducts illegal transactions. This malware frequently uses phishing links to deceive users.
The Ousaban trojan also employs phishing and hacks accounts through fake banking portals. Cisco Talos notes that Ousaban is delivered in a later stage of the Astaroth attack, indicating that the operators of these programs may be connected or even the same individual.
Google representatives thanked the researchers for their work and promised to strengthen security measures: “We have removed suspicious links and are exploring options to enhance protection to prevent such malicious activity in the future.”





