Anatsa Trojan Evades Google Play, Targets New Countries
In November of last year, researchers discovered the expansion of malicious activity by an Android trojan named Anatsa into Slovakia, Slovenia, and the Czech Republic. This expansion is part of a new campaign which, despite enhanced detection and protection mechanisms implemented in Google Play, saw some malicious loaders successfully exploit Android’s accessibility service.
ThreatFabric reports that all loaders used in this malicious campaign effortlessly accomplish their task, circumventing the systemic restrictions of Android 13. The campaign involves five loaders with a total download count exceeding 100,000.
Anatsa, also known as TeaBot and Toddler, is distributed through seemingly harmless applications in the Play Store. Once installed and launched, the Anatsa trojan can fully control infected devices and perform various actions on behalf of the victim, including stealing credentials for fraudulent transactions.
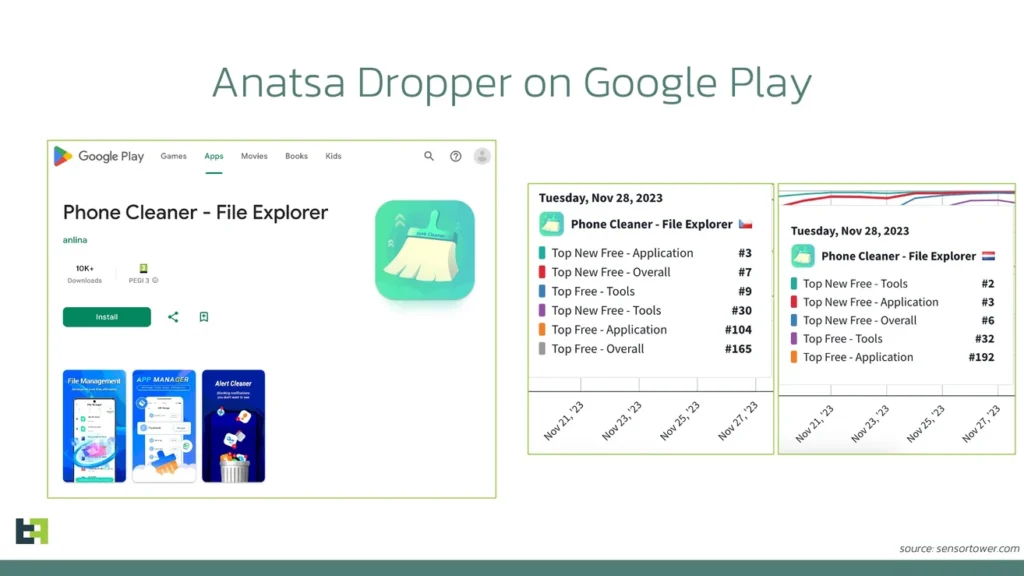
One version of the loader, disguised as a “Phone Cleaner — File Explorer” system cleaning application, used version management techniques to embed malicious code. Initially, the application uploaded to Google Play did not contain any malicious code. The malevolent functionality was added through subsequent updates when Google’s rigorous code moderation was essentially bypassed.
To avoid detection after embedding the malicious functionality, the perpetrators used a multi-stage infection process. The loader dynamically downloaded configuration and payload from a C2 server, allowing hackers to change malicious components at will.
Although the “Phone Cleaner — File Explorer” app is no longer available in the official Play Store, it can still be downloaded through third-party sources. According to AppBrain, the app was downloaded about 12,000 times between November 13 and 27, before it was removed.
ThreatFabric notes the criminals’ preference to concentrate their attacks on specific geographic regions, leading to a significant number of fraud cases in a short period.
Following ThreatFabric’s report, Google representatives announced that all applications identified by the researchers, namely:
- Phone Cleaner – File Explorer (com.volabs.androidcleaner)
- PDF Viewer – File Explorer (com.xolab.fileexplorer)
- PDF Reader – Viewer & Editor (com.jumbodub.fileexplorerpdfviewer)
- Phone Cleaner: File Explorer (com.appiclouds.phonecleaner)
- PDF Reader: File Manager (com.tragisoap.fileandpdfmanager)
One of the applications had reached 100,000 installations by the time of its removal on February 19th. It is hoped that users noticed something amiss in time and removed the disguised dropper from their device.
Google points out that Android users are now automatically protected against known versions of the Anatsa malware thanks to the Play Protect feature, which is enabled by default on all devices with Google services.
Play Protect can warn users and block applications known for malicious behavior, even if they are not from the official Play Store.
However, despite the threat passing and Google’s protective measures continuously improving, complacency is not an option. To avoid becoming a victim of similar malware, never install questionable applications from unknown publishers, and pay close attention to the permissions requested.





