Threat Actor Evades Detection with IDAT Loader, Deploys Remcos
According to a report by Morphisec, Ukrainian organizations based in Finland have been targeted by a malicious campaign distributing the Remcos Remote Access Trojan (RAT). The attack has been attributed to the group UAC-0184.
The Remcos RAT is delivered via the IDAT Loader. This phishing campaign employs military-themed lures as a starting point for initiating an infection chain, leading to the deployment of the IDAT Loader. This loader then utilizes a built-in steganography algorithm within PNG images to locate and extract the Remcos RAT, enabling the perpetrator to control the infected computer, steal personal information, and monitor the victim’s actions.
The attack leveraged phishing emails disguised as communications from the Israeli Defense Forces and employed sophisticated malware delivery methods, including dynamic loading of Windows API functions, internet connectivity checks, and bypassing process blocklists.
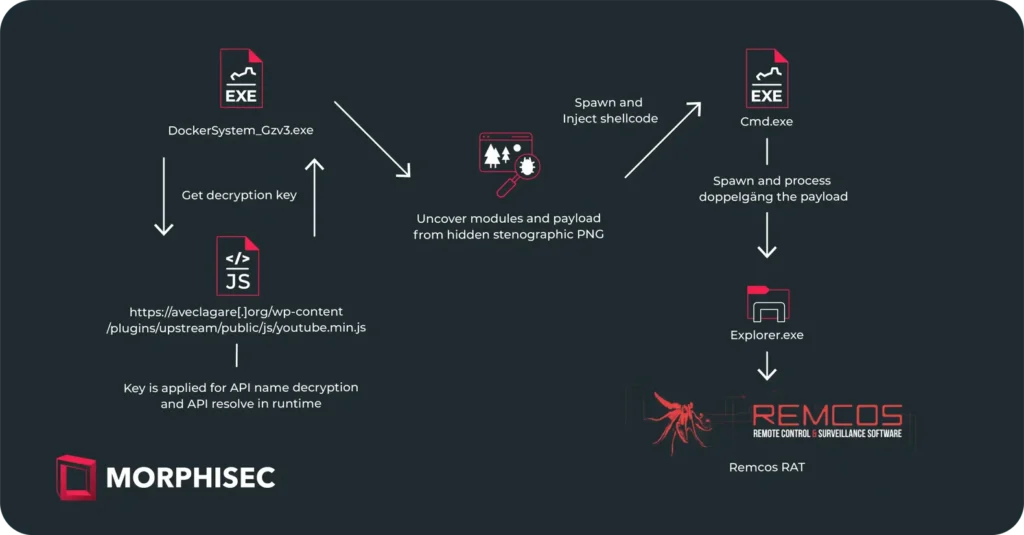
IDAT Loader, known for its modular architecture and features distinct from other loaders, including a code injection function, had previously been used to distribute malware families such as DanaBot, SystemBC, and RedLine Stealer. In the identified campaign, IDAT modules were embedded directly into the executable file, marking a departure from the common practice of downloading from a remote server.
The study also examines detection evasion techniques utilizing steganography and Module Stomping—a technique that allows malicious code to evade detection by antivirus solutions through injection into legitimate libraries.
IDAT Loader shares characteristics with another loader family named HijackLoader, first identified in July 2023, which facilitates the delivery of payloads like DanaBot, SystemBC, and RedLine Stealer. Despite lacking advanced features, the loader employs a modular architecture for code injection and execution, a rarity among most loaders.





