Trend Micro Found Fileless Banking Trojan Targeting Brazilian and Taiwan Banks
Trend Micro recently discovered a fileless malware that steals online banking credentials by remotely controlling access to user devices. In addition, it steals the device and email account data. The hackers installed a hacking tool called RADMIN on the device. The malware is targeted at customers in major banks in Brazil and Taiwan.

Image: trendmicro
Fileless malware is malware that hackers use to access user devices without having to write on the device or leave traces of activity. With this method, the executable does not appear on the disk. It uses executable files that already exist in programs such as mshta.exe. In addition, malware typically uses Powershell.
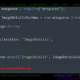
The malware targeting Brazilian and Taiwanese banks used multiply .BAT attachments that “was capable of opening an IP address, downloading a PowerShell with a banking trojan payload, and installing a hack tool and an information stealer.” Then download a PowerShell containing the bank Trojan payload and install RADMIN and a message stealer to extract the user’s data. The information stealer is also capable of scanning strings associated with banks and other related connections to determine if it is targeted at users. Trend Micro did not find stolen data during the analysis. These data are often used for fraudulent activities or resold on the dark so that hackers can commit further crimes.
Once the malware enters the device, it downloads the PowerShell code, executes and connects to other URLs, extracts and renames the file. The renamed file still appears as a real file, labeled as an executable file and an image file. Then, when the .LNK file enters the startup folder, “it drops .LNK files in the Startup folder, forcing the system to restart after three minutes. It also creates a lock screen that forces the user to enter their user name and password. Using the system’s security logon feature, it detects wrong credentials being entered and notifies the user to repeat the process. The malware also logs the user’s correct credentials, which it sends to the command and control (C&C) server, and immediately hides its malicious routine by deleting all dropped and created files and folders in the Startup folder.”
This fileless malware also installs hacking tools on the user’s device and then executes another Trojan horse TrojanSpy.Win32.BANRAP. It opens Outlook and extracts the data, then sends the data back to the server. The RDP Wrapper folder installed by RADMIN helps hackers gain administrator access to the system and hide user activity.
On reboot, it deletes the newly installed files to remove their traces again and replaces them with malicious .LNK before loading the Trojan for the web application. When the user logs in to the online bank and feeds it back to the command and control server, it will get the credentials here.