Beware PhantomBlu: Phishing Campaign Targets US Businesses
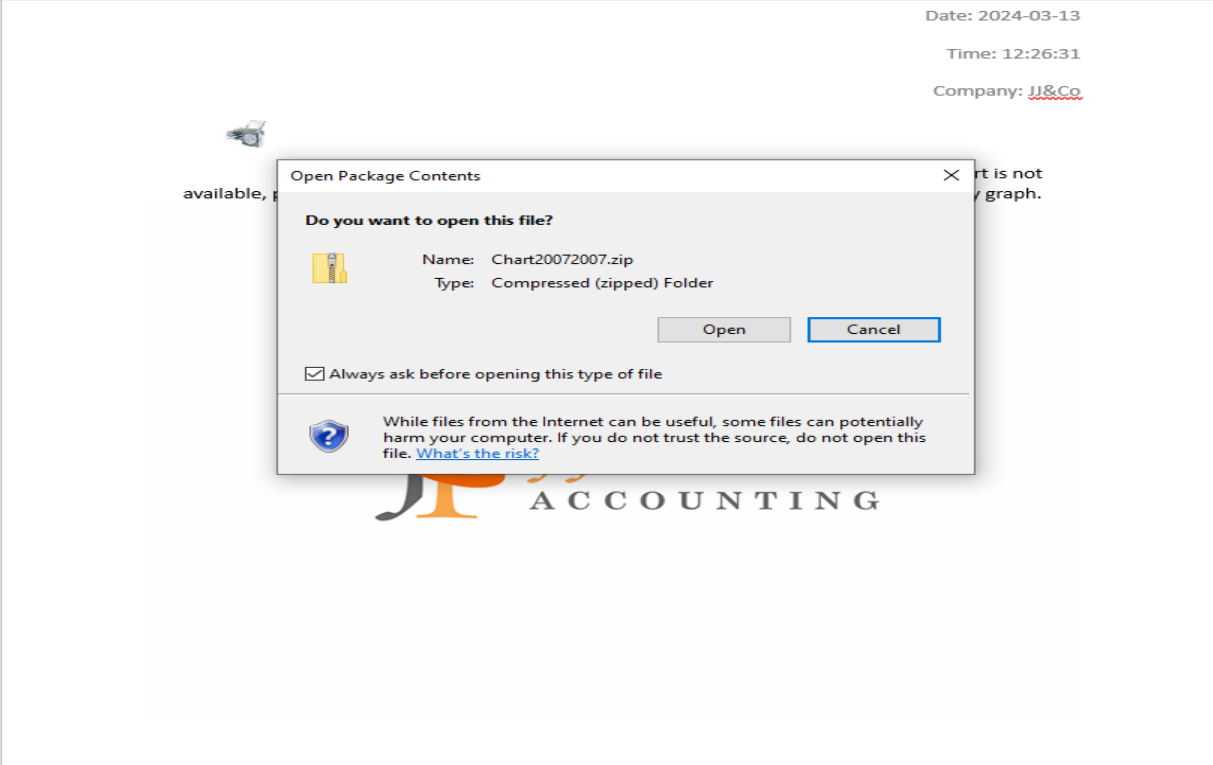
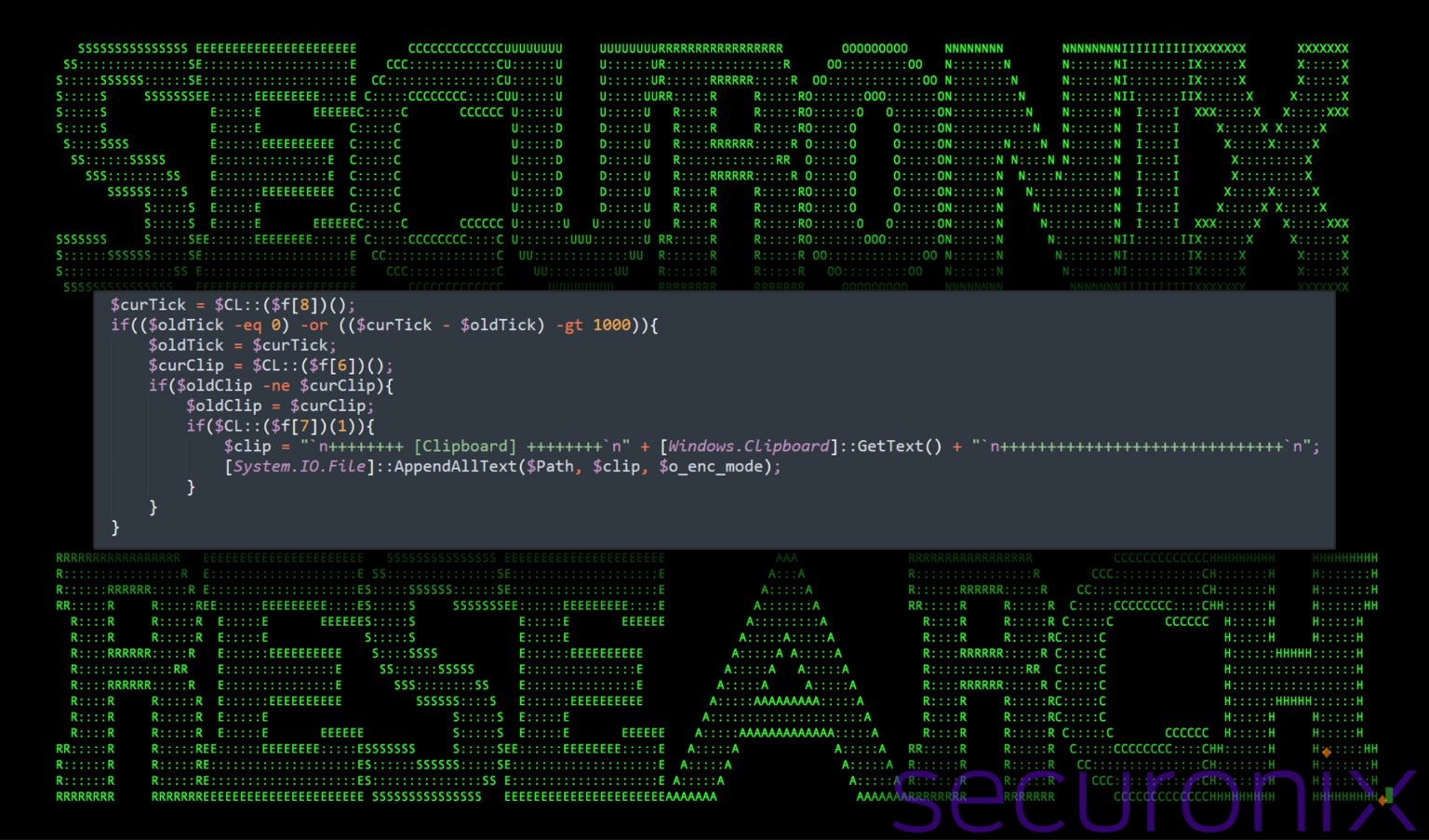
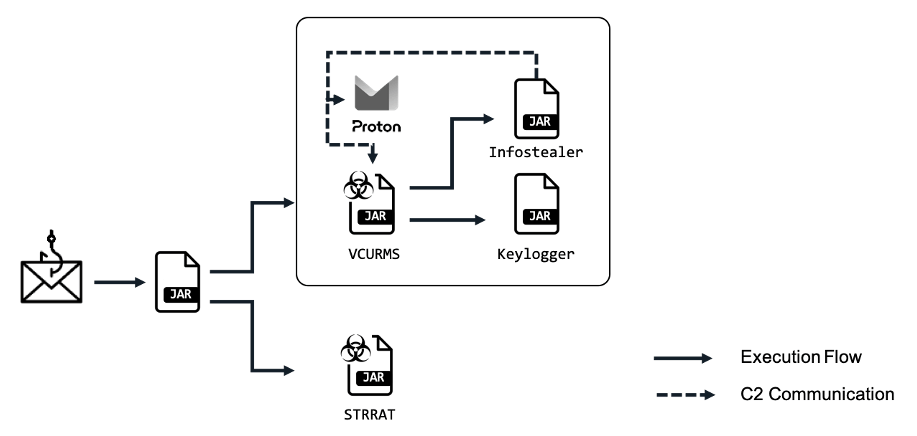
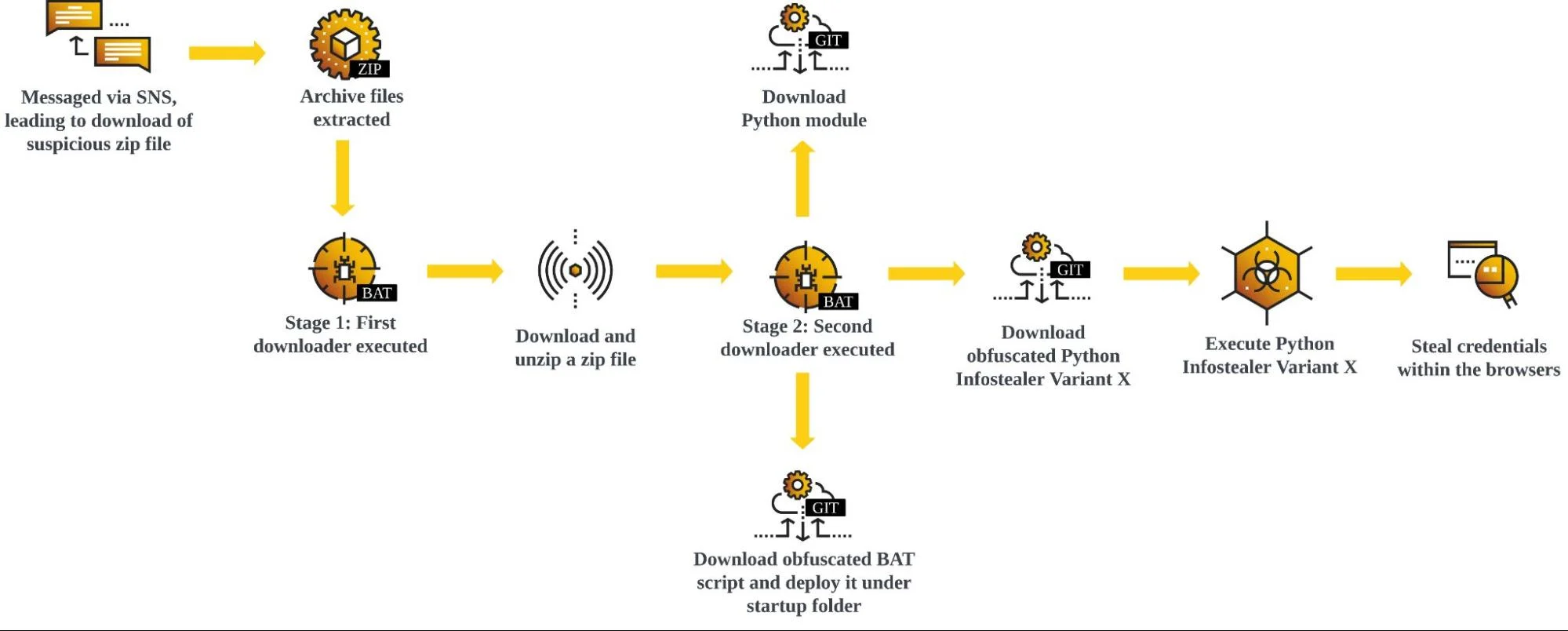
The Israeli cybersecurity firm Perception Point has unveiled details of a new phishing campaign targeting American organizations. The operation, code-named PhantomBlu, aims to infiltrate systems with the NetSupport RAT, a malicious version of the...