BIPClip Malware: A New Threat to Crypto Developers
Recently, the Python Package Index (PyPI) repository uncovered seven packages engineered for the theft of BIP39 mnemonic phrases, which are utilized for the restoration of private keys in cryptocurrency wallets.
This operation, dubbed BIPClip and identified by specialists from ReversingLabs, specifically targets developers engaged in the creation and protection of cryptocurrency wallets.
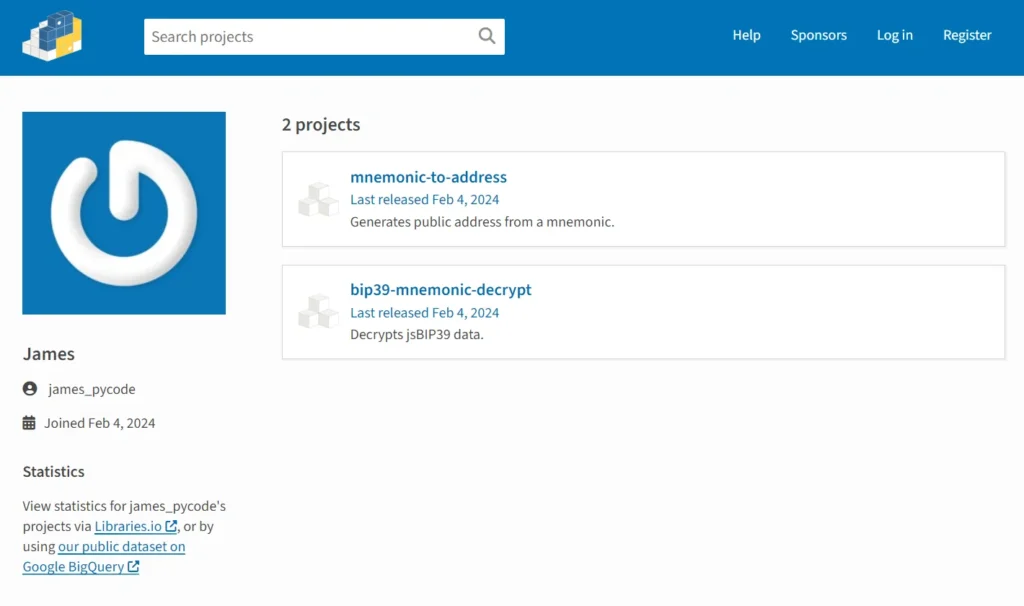
Throwaway account used to publish the malicious packages
These packages, collectively downloaded 7,451 times before their removal from PyPI, are listed as follows:
- jsBIP39-decrypt (126 downloads);
- bip39-mnemonic-decrypt (689 downloads);
- mnemonic_to_address (771 downloads);
- erc20-scanner (343 downloads);
- public-address-generator (1005 downloads);
- hashdecrypt (4292 downloads);
- hashdecrypts (225 downloads).
It’s noteworthy that the malicious BIPClip campaign commenced quite some time ago, on December 4, 2022, with the first publication of the penultimate package in the list above, “hashdecrypt.”
One of the packages, “mnemonic_to_address,” was devoid of malicious code, except for listing “bip39-mnemonic-decrypt” as a dependency, wherein the malicious component was concealed. Two other packages, “public-address-generator” and “erc20-scanner,” operated similarly by transmitting mnemonic phrases to the culprits’ control server. Concurrently, “hashdecrypts” contained nearly identical code for data extraction.
Moreover, within these packages, links were found to a GitHub profile named “HashSnake,” which promotes the hCrypto repository for extracting mnemonic phrases from cryptocurrency wallets using the “hashdecrypts” package. The repository’s commit history reveals that the campaign has been ongoing for over a year.
The HashSnake account is also present on Telegram and YouTube, where corresponding software products are advertised. For instance, a video was published on September 7, 2022, showcasing the xMultiChecker 2.0 tool for verifying cryptocurrency logs.
The discovery of these packages highlights the security threats associated with open-source repositories, especially when legitimate services like GitHub are utilized for distributing malicious software.
Furthermore, projects that are no longer updated become attractive targets for attackers who can seize control over developer accounts and publish trojanized versions of products, paving the way for widespread attacks on the supply chain.
Hackers are capable not only of compromising the supply chain once but also of remaining undetected over extended periods, thereby exacerbating the risks for both developers and end-users.