Chinese Users Targeted: Notepad++ Search Results Poisoned
In recent research, it was revealed that Chinese users seeking official versions of software like Notepad++ and VNote through search engines such as Baidu are increasingly falling victim to cunning cybercriminals.
The attacks are conducted through fraudulent advertising in search engines and fake links that distribute trojanized versions of these programs. The ultimate goal is to install Geacon, a Cobalt Strike implementation in Golang.
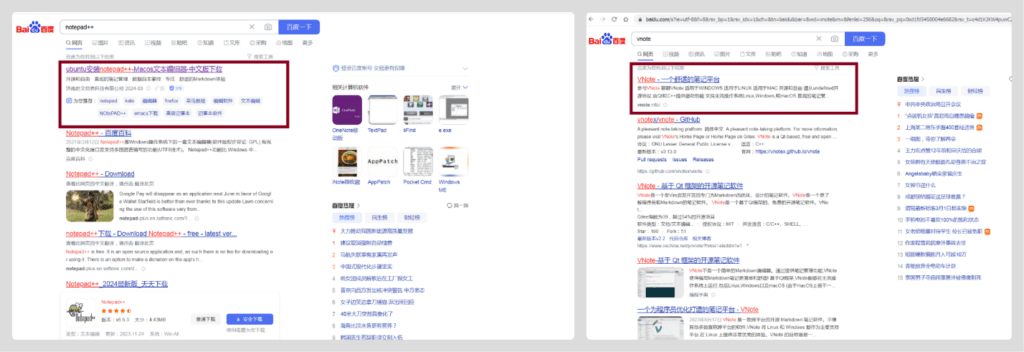
Malicious link in the advertisement section for the search notepad++ (left) and search results for vnote (right)
Kaspersky Lab specialists discovered a fraudulent site appearing in Notepad++ search results. Notably, the site’s address mentions VNote, and the program offered for download on the site uses the Notepad++ logo.
However, the intrigue deepens: the downloaded packages contain “Notepad–,” which is not a fabrication of cybercriminals, as it is a legitimate text editor that serves as an almost complete replica of Notepad++ for the Chinese market, developed by local specialists.
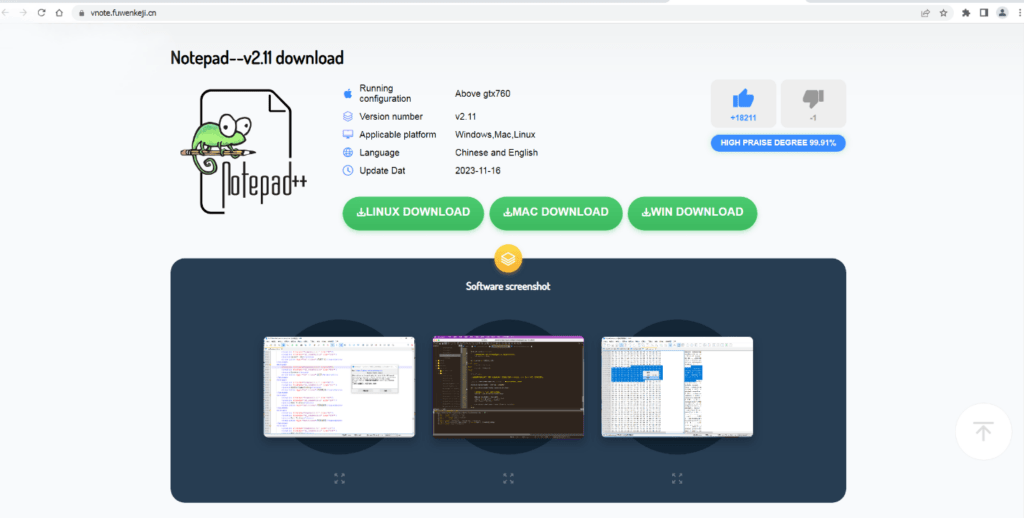
Page with fake NotePad++
Despite the malicious site offering three versions of the program (for Windows, Linux, and macOS), the link for Windows oddly leads to the official Gitee repository with a legitimate installer for Notepad–. Meanwhile, the versions for Linux and macOS direct to malicious installation packages on an external resource.
Another fake page, found by searching for “vnote” on Baidu, attempts to mimic the official website of the VNote program, completely copying its style. Naturally, malicious software is present on this page as well.
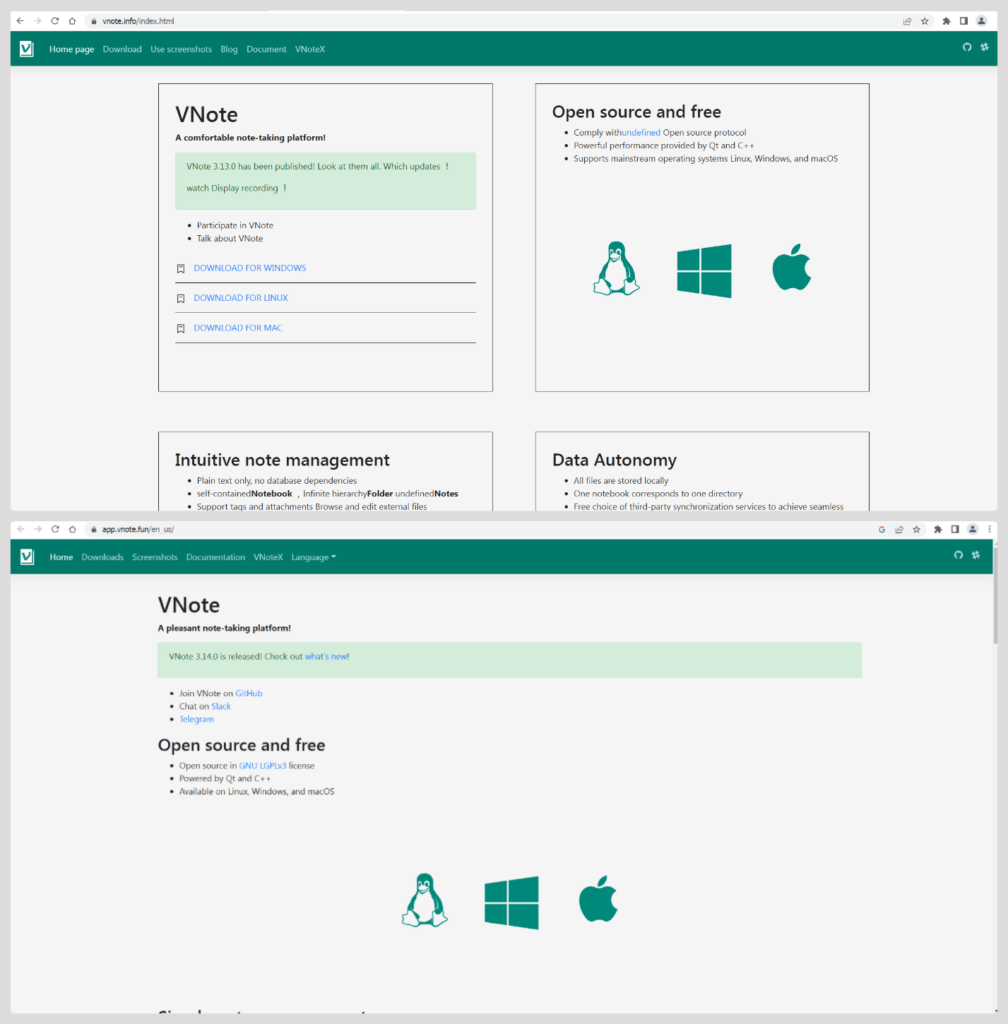
Fake (above) and the original (below) VNote site
The investigation of the trojanized installers showed that they are designed to download additional malicious code from a remote server. This code is capable of creating SSH connections, performing file operations, listing processes, accessing clipboard contents, launching programs, uploading and downloading files, taking screenshots, and even entering sleep mode. Control is exercised via the HTTPS protocol.
These examples are just a part of a broader operation to distribute malware through advertising campaigns, which have previously been used to promote viruses such as FakeBat (also known as EugenLoader), using MSIX installer files masquerading as applications like Microsoft OneNote, Notion, and Trello.
Kaspersky Lab specialists intend to continue investigating this malicious campaign to identify additional stages of the attack and prevent the spread of malware among users.
Users are advised to exercise particular caution when downloading software from the Internet and to pay attention to any suspicious details (from mismatched addresses to dubious designs or obvious errors) on websites offering popular software.





