Ransomware Alert: StopCrypt Upgrade Bypasses Defenses
Security researchers have unveiled a new variant of the ransomware StopCrypt, also known as STOP. This iteration employs a complex, multistage execution process using shell codes to circumvent security tools, rendering the malware particularly menacing due to its detection challenges.
StopCrypt, despite being the most prevalent ransomware, seldom garners mention from security researchers. Unlike other notorious operations such as LockBit, BlackCat, and Clop, STOP targets individual users rather than corporate entities, aiming to extract modest ransoms ranging from 400 to 1000 dollars.
This virus predominantly propagates through malicious advertising and dubious websites offering downloads of free software, game cheats, and cracks, leading to the infection of users’ systems with various malware types, including trojans, info stealers, and StopCrypt itself.
Since its first emergence in 2018, the encryption algorithm of the virus has not undergone significant modifications, except for the release of new versions to correct critical errors. Hence, each new variant of STOP draws attention due to the large number of individuals potentially affected.
The threat research team at SonicWall has identified a new variant of STOP, which now utilizes a multistage execution mechanism. This includes the download of an unrelated DLL file (msim32.dll), likely as a diversion, and the implementation of prolonged time delay loops, assisting in circumventing time-based security measures.
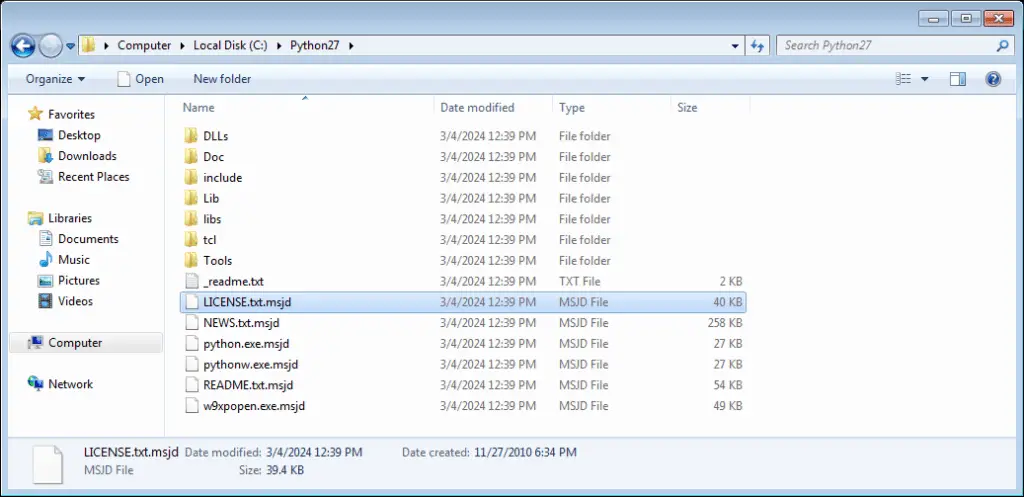
Ransomware encrypted filenames
The subsequent phase employs the “Process Hollowing” method, where StopCrypt hijacks legitimate processes and injects its payload for concealed execution in memory. This is achieved through a series of meticulously orchestrated API calls that manipulate the process’s memory and control flow.
Following the deployment of the final payload, a series of actions are taken to ensure the persistence of the ransomware, including modifying Access Control Lists (ACLs) to prevent users from deleting critical files and directories of the malware, and creating a scheduled task to execute the payload every five minutes.
Ultimately, files are encrypted and appended with the “.msjd” extension, and a text note is created in every affected folder with instructions on how to pay the ransom for data restoration.
The evolution of StopCrypt into a more covert and potent threat underscores a worrying trend in cybercrime. Although the financial demands of StopCrypt are not high and its operators do not engage in data theft and public disclosure, the damage this ransomware can inflict on ordinary individuals can be quite significant.
To avoid falling victim to StopCrypt or similar malicious software, it is crucial to exercise caution when downloading programs from unreliable sources, regularly update software and antivirus programs, create data backups, and enhance awareness of cyber threats.
Adhering to fundamental cybersecurity measures can help prevent infection and minimize damage from this and other ransomware threats.






