fuzzuf: Fuzzing Unification Framework
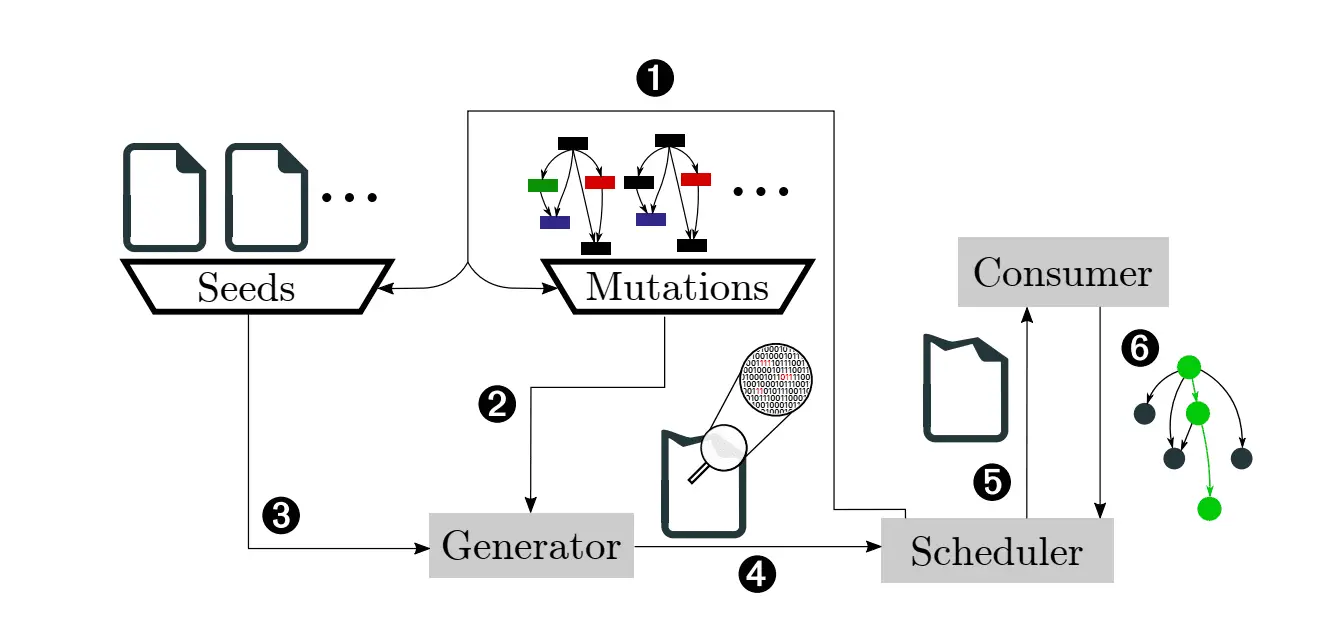
fuzzuf fuzzuf (fuzzing unification framework) is a fuzzing framework with its own DSL to describe a fuzzing loop by constructing building blocks of fuzzing primitives. Why use fuzzuf? fuzzuf enables a flexible definition of a fuzzing loop...