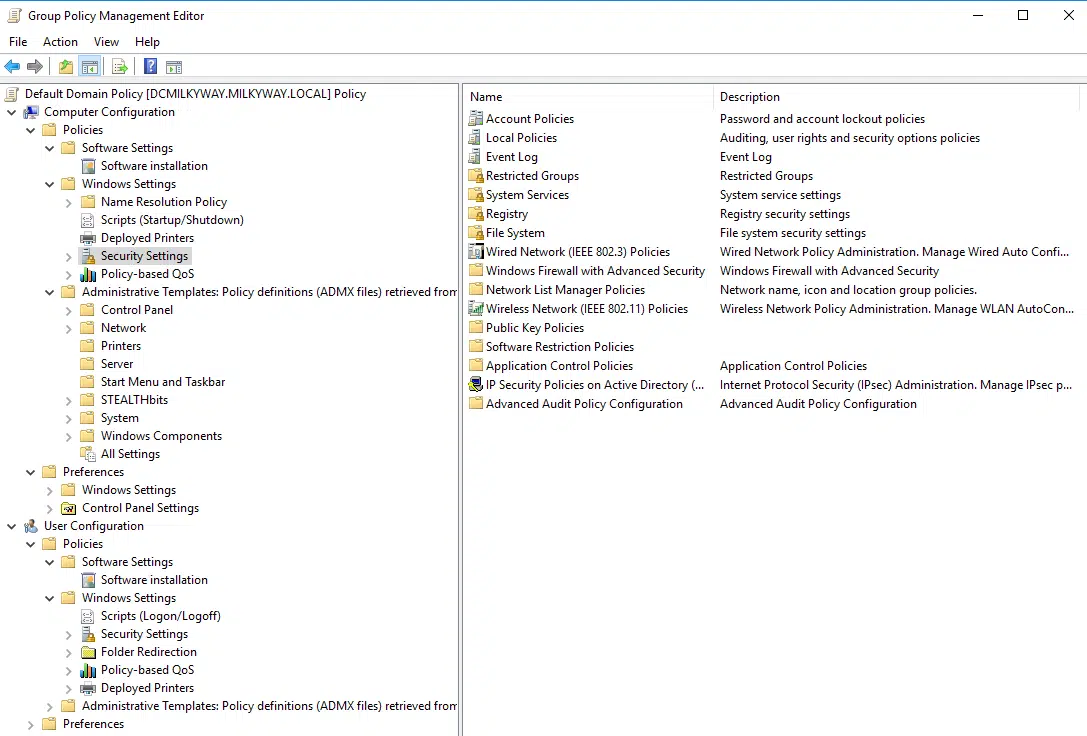
Bypass Domain Requirements with Disconnected GPO Editor
Disconnected GPO Editor Disconnected GPO Editor is a launcher for the official Group Policy Manager to bypass the domain joined requirement that is needed when using the official MMC snap-in. The tool works by...