ITG05 Strikes: Global Phishing Campaign Exposed
IBM X-Force reports a series of phishing campaigns by ITG05, involving the distribution of counterfeit documents purporting to be from governmental and non-governmental organizations across Europe, the Caucasus, Central Asia, and both North and South America.
The IBM report highlights the employment of a diverse array of documents—ranging from internal to publicly accessible, and likely fabricated by the perpetrators themselves—related to finance, critical infrastructure, executive interactions, cybersecurity, maritime security, healthcare, business, and defense industry manufacturing.
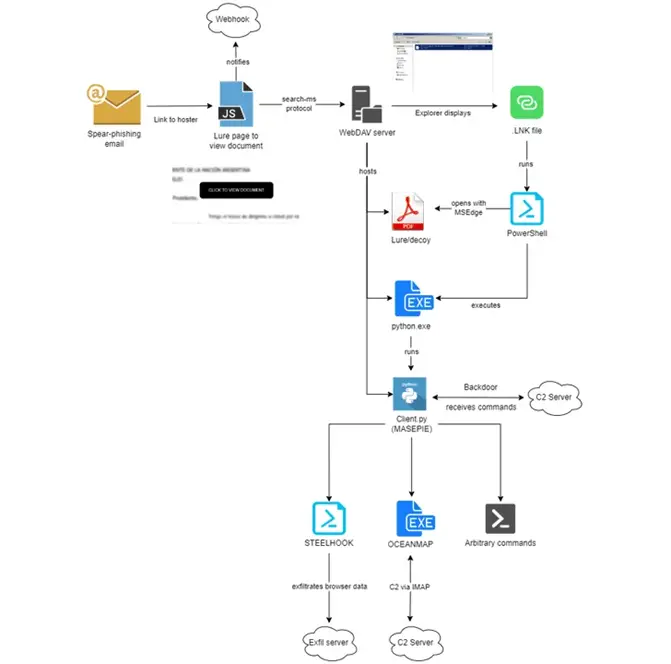
Particular attention is given to the use of a URI protocol handler named search-ms, which allows applications and HTML links to initiate customized searches on a device. Cybercriminals exploit search-ms to deceitfully compel victims to download malicious software from a WebDAV server.
The report also mentions the potential use of compromised Ubiquiti routers as servers for disseminating phishing and malware. It recalls that, at the end of February, federal agencies in the USA and other countries alerted users to the risks associated with using Ubiquiti EdgeRouter routers, which could be exploited for credential harvesting, traffic redirection, and phishing page creation.
In their communications, cybercriminals impersonate organizations from specific countries—Argentina, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the USA. The letters utilize a combination of genuine public governmental and non-governmental documents as lures to trigger the infection chain. Free hosting providers are used for hosting, facilitating the preparation of payloads to support ongoing operations.
The infection chain culminates with the deployment of MASEPIE, OCEANMAP, and STEELHOOK programs, designed for file theft, execution of arbitrary commands, and data exfiltration from browsers.
Researchers conclude that ITG05 demonstrates adaptability to evolving capabilities, introducing new infection methodologies and utilizing commercially available infrastructure while continuously advancing the capabilities of their malicious software.





