Beware PhantomBlu: Phishing Campaign Targets US Businesses
The Israeli cybersecurity firm Perception Point has unveiled details of a new phishing campaign targeting American organizations. The operation, code-named PhantomBlu, aims to infiltrate systems with the NetSupport RAT, a malicious version of the legitimate remote desktop tool NetSupport Manager. This Trojan allows attackers to harvest confidential information from compromised devices.
The hallmark of this operation lies in the hackers’ manipulation of OLE templates, enabling the execution of malicious code through Microsoft Office documents while evading detection.
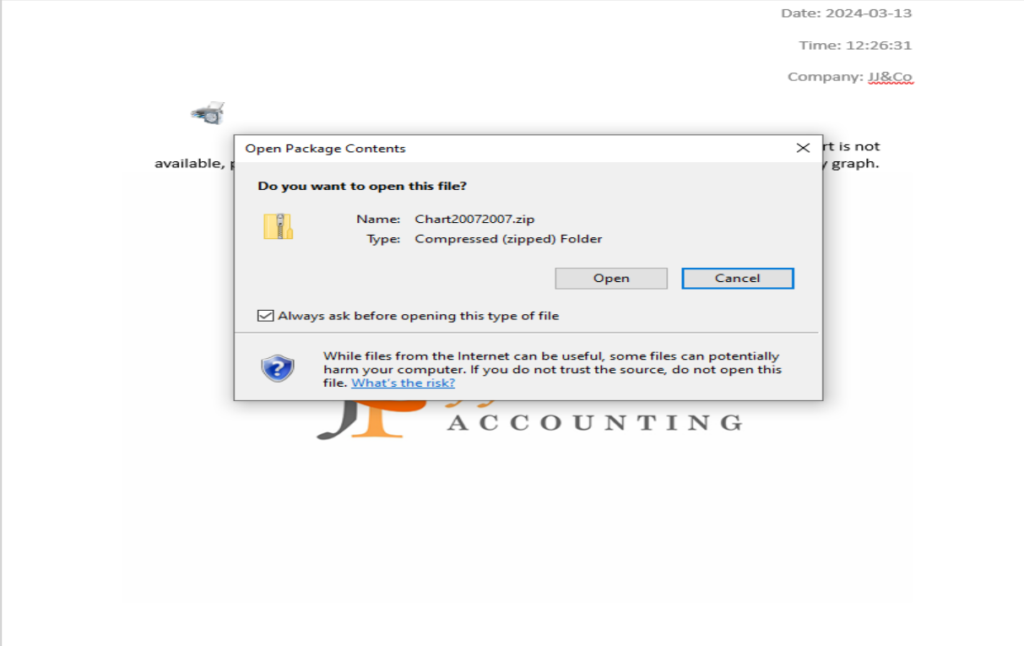
The phishing attack initiates with an email masquerading as a salary-related communication from the accounting department. The message entices recipients to open an attached Word document to view a “monthly salary report.”
The document instructs the reader to enter a password provided in the email body and enable editing mode. It then prompts users to double-click a printer icon to view the salary schedule. This action triggers the launch of a ZIP archive containing a malicious shortcut. Activating this shortcut ultimately leads to the download and execution of NetSupport RAT on the target machine.
Researchers also highlight an increasing exploitation of cloud platforms and popular Content Delivery Networks (CDN) to craft entirely undetectable phishing links. Such links are typically generated using specialized phishing kits available to cybercriminals via subscription services on Telegram for $200 a month. These solutions offer enhanced anonymity and detection evasion through built-in antibot protections.
These innovations in phishing and malware distribution reflect the continuous evolution of attackers’ methods, who adapt their malicious infrastructure daily to circumvent current security systems, thereby increasing the success rate of their malevolent campaigns.