Report: GitHub becomes a hotbed for malware
GitHub, a platform for programmers, is a popular and favorite tool for hackers, used to store and distribute malware. According to a recent report by Recorded Future, a cybersecurity company based in the United States, the threat of cybersecurity originating from legitimate platforms is increasing globally, including platforms dedicated to programmers such as GitHub.
Recorded Future stressed that GitHub is providing hackers with the ability to disguise their activities with legitimate network traffic, making it difficult for law enforcement to track and identify the perpetrators of attacks.
Experts call this tactic ‘Living Off Trusted Sites’ (LOTS), a variant of the Living off the Land (LotL) technique, which is often used by attackers to conceal their attack behaviors.

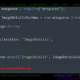
The most common trend for exploiting GitHub is to distribute malware. In December 2023, security firm ReversingLabs reported detecting several fake packages, using the high-level programming language Python for a variety of programming purposes, that were receiving secret attack commands from GitHub.
The use of the GitHub platform as a “dead drop” to obtain the URLs of command-and-control servers is very common. In addition, GitHub is often used by attackers in a variety of other ways, including using the GitHub homepage as a phishing server or traffic redirector, as well as a backup control channel.
In addition to GitHub, Recorded Future has noted an increase in the trend of hackers exploiting legitimate internet platforms, such as Google Drive, Microsoft OneDrive, Dropbox, Notion, Firebase, Trello, Discord, and various code-management platforms, including GitLab, BitBucket, and Codeberg.
Currently, security experts have not found an effective general solution to detect signs of hackers exploiting popular platforms to carry out cyberattacks and distribute malware.
To do this, it depends on the specific environment, the availability of logs, the organizational structure, the service usage model, and the risk level, as well as a combination of search and detection strategies.