Alert: Godzilla Web Shell Deploys Through Apache ActiveMQ Flaw
Trustwave has issued a warning regarding the notable surge in the exploitation of a patched vulnerability within Apache ActiveMQ, aimed at deploying the Godzilla web shell onto compromised hosts.
The web shells, concealed in an obscure binary format, are crafted to circumvent security systems and signature-based scanners. Intriguingly, despite the binary file’s unknown format, the JSP mechanism of ActiveMQ continues to compile and execute the web shell.
The flaw, CVE-2023-46604 (with a CVSS score of 9.8), in Apache ActiveMQ, facilitates remote code execution (RCE). Since its public disclosure in late October 2023, the vulnerability has been actively exploited by numerous adversaries to deploy ransomware, rootkits, cryptocurrency miners, and DDoS botnets.
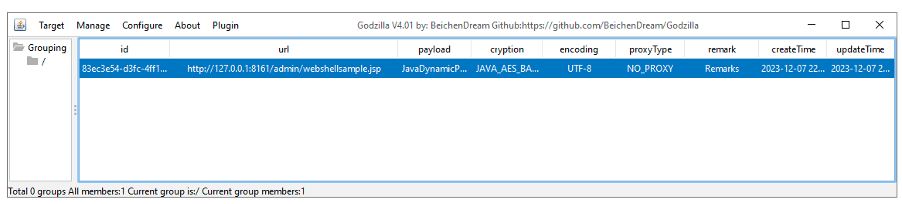
Godzilla’s management user interface available to the threat actor
In the latest series of intrusions detected by Trustwave, vulnerable instances were targeted with JSP (Java Server Pages) based web shells, which were placed in the “admin” folder of the ActiveMQ installation directory. The web shell, named Godzilla, acts as a multifaceted backdoor capable of parsing incoming HTTP POST requests, executing the content, and returning the results via an HTTP response.
The malicious files are particularly notable for the fact that the JSP code is hidden inside a binary file of an unknown type. This method aids in circumventing security measures and evading detection during scanning. A more thorough examination of the attack chain reveals that the web shell code is transformed into Java code before its execution by the Jetty servlet engine (software components that extend the functionality of a web server).
Ultimately, the JSP payload enables the cybercriminal to connect to the web shell through the Godzilla management interface and gain complete control over the target host, facilitating the execution of arbitrary shell commands, viewing network information, and performing file management operations. Apache ActiveMQ users are strongly advised to update to the latest version as soon as possible to mitigate potential threats.





