Google researchers announced that Apple iMessage exists multiple critical vulnerability
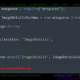
Google Project Zero has announced that Apple iMessage has multiple security vulnerabilities and reminds users that it needs to be fixed immediately. These vulnerabilities are very dangerous because of the high level of damage, so Google only announced some of the vulnerabilities which were fix, and some of the vulnerabilities have not been completely repaired have been kept private. For the normal user, it is most important to upgrade iMessage to the latest version immediately. The four bugs are CVE-2019-8641 (details kept private), CVE-2019-8647, CVE-2019-8660, and CVE-2019-8662.

“How to use iMessage on windows PC/Laptop/Windows 10” by Ross Taylor is licensed under CC BY-NC-ND 4.0
Google security engineers say that an attacker only needs to send a malformed message to the user to trigger a security vulnerability in iMessage and steal files. In other words, as long as the user does not close iMessage and the mobile phone number or email is leaked, the attacker can launch an attack on the user remotely without user interaction.
The main reason for the high vulnerability is that the exploiter can remotely steal files, that is, the sent information will connect to the attacker server. An attacker can load local files into memory and cause out-of-bounds reads or even out-of-bounds writes, which can cause very serious problems. It is also the case that an attacker can read locally stored files if necessary, and even upload specific confidential files to the attacker’s server. This vulnerability affects all iDevices running iOS below 12.4, iPad Air, so the scope of influence is quite extensive.
In addition to the above vulnerabilities, Google researchers have discovered additional vulnerabilities in iMessage that could allow an attacker to remotely execute arbitrary code. At the same time, the attacker can kill other applications if necessary, so the above vulnerability can destroy the security protection function for the iOS system.
In addition, Google has two other vulnerabilities that are not mentioned in input authentication. With this vulnerability, an attacker can brick the device. However, the details of the vulnerability have not been announced because there are still bugs in Apple that have not been completely fixed. Apple said it will also take measures to filter the information to prevent malicious content.
Via: ZDNet