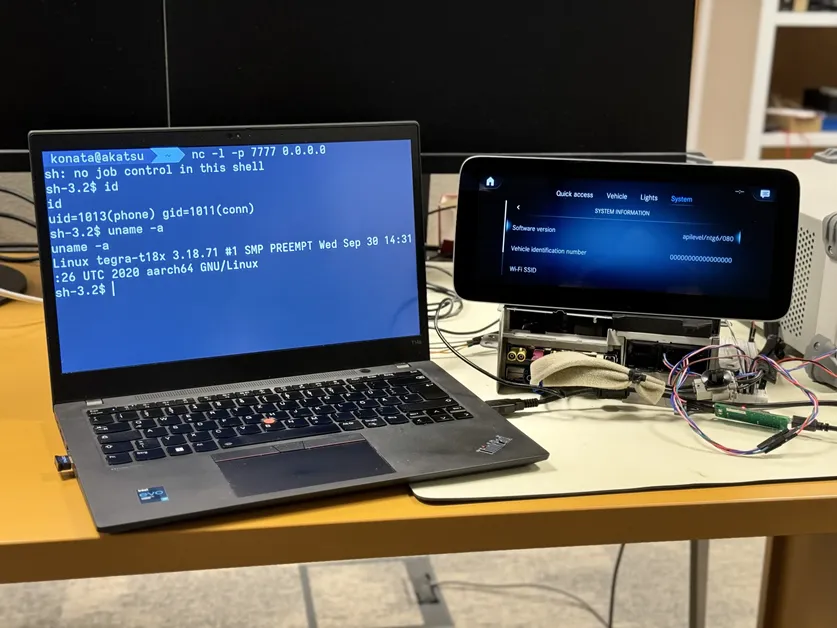
Critical Wing FTP Server Flaw (CVSS 10.0) Under Active Exploitation: Patch Now!
Researchers at Huntress have observed active exploitation of a critical vulnerability in Wing FTP Server—a mere day after its public disclosure. The flaw, tracked as CVE-2025-47812, received the highest possible severity rating (CVSS 10.0),...