Microsoft released a security bulletin on the Flawed SSD Encryption
Earlier, researchers at the University of Nijmegen in the Netherlands found that some mainstream SSDs have severe vulnerabilities in their hardware-based full-disk encryption.
This vulnerability allows an attacker to easily bypass high-intensity password authentication and set up any password for decryption. This hardware-level encryption is virtually useless.
At the same time, this security vulnerability will also affect Windows BitLocker hard disk encryption, even if you use Microsoft’s encryption tools cannot avoid the impact of the vulnerability.

Microsoft has just released a security bulletin to alert high-security users to the impact of the vulnerability and to provide a temporary solution for users to check encryption and resolve issues.
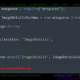
To check the type of drive encryption being used (hardware or software):
- Run ‘manage-bde.exe -status’ from elevated command prompt.
- If none of the drives listed report “Hardware Encryption” for the Encryption Method field, then this device is using software encryption and is not affected by vulnerabilities associated with self-encrypting drive encryption.
For drives that are encrypted using a vulnerable form of hardware encryption, you can mitigate the vulnerability by switching to software encryption using Bitlocker with a Group Policy.
To mitigate vulnerabilities associated with self-encrypting drives on Windows systems:
- Configure and deploy a Group Policy to enable forced software encryption.
- Fully turn off BitLocker to decrypt the drive.
- Enable BitLocker again.
This temporary method is also called Group Policy to force the hardware encryption to be disabled. The complete solution has to wait for the hard disk manufacturer to update the firmware to fix it.