Fake Chrome Update Hides Android Brokewell Spyware
ThreatFabric has identified a new malicious application named Brokewell, capable of recording every action on a device, from keystrokes to text input and application launches. The Trojan is distributed through a counterfeit Google Chrome update in the browser and targets Android users.
Brokewell is in the active development stage and possesses extensive capabilities for device capture and remote control. Fraudsters have already used the Trojan to masquerade as financial services that operate on a “buy now, pay later” model (such as Klarna), as well as the Austrian digital authentication application ID Austria.
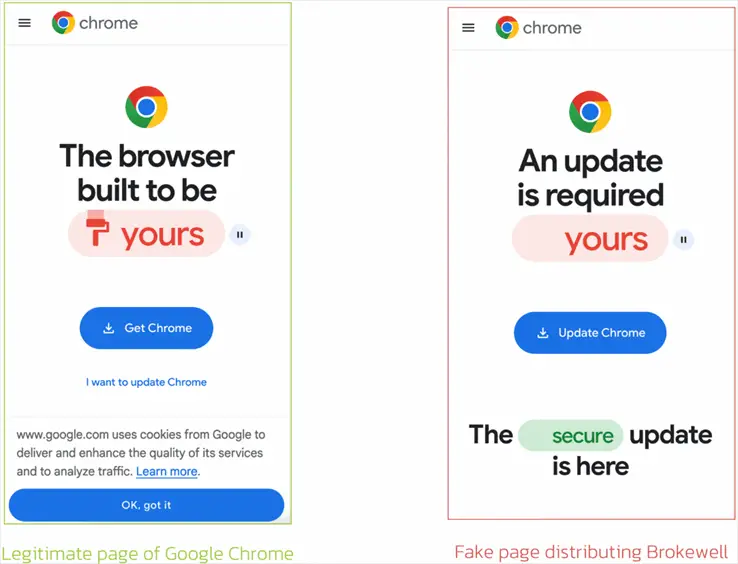
Real Google Chrome download page (left) and fake Chrome update download page (right)
Brokewell’s main functionalities include data theft and granting remote access to perpetrators:
- Simulating login screens to steal credentials;
- Intercepting and extracting cookies through its own WebView interface after a user logs into a legitimate site;
- Capturing user interactions with the device, including taps, swipes, and text inputs, to steal the entered data;
- Collecting information about the hardware and software characteristics of the device;
- Accessing the device’s call log and geolocation;
- Recording audio through the device’s microphone.
Device capture capabilities:
- Displaying the device screen in real-time;
- Executing touch gestures and swipes on the infected device;
- Remotely clicking on screen elements;
- Inputting text in specified fields and simulating the pressing of system buttons.
Additionally, researchers have discovered a new tool called Brokewell Android Loader, developed by an individual known as Baron Samedit. The loader is used to circumvent restrictions introduced in Android 13, which were intended to prevent the misuse of the accessibility service by apps installed from unofficial sources.
Experts warn that the ability to capture devices is highly sought after by cybercriminals, as it enables them to carry out fraudulent operations directly from the victim’s device, complicating detection. To protect against such threats, it is recommended to only download apps and updates from the official Google Play store and to activate the Play Protect feature.






