CVE-2023-37924: Critical SQL Injection Vulnerability in Apache Submarine
In the realm of machine learning, Apache Submarine has emerged as a prominent End-to-End Machine Learning Platform, empowering data scientists to seamlessly create and manage machine learning workflows. This versatile platform caters to the entire ML model lifecycle, encompassing data exploration, data pipeline construction, model training, deployment, and monitoring. However, a recent vulnerability, designated as CVE-2023-37924, has been identified in Apache Submarine, potentially exposing systems to unauthorized access.

The Vulnerability in Detail
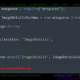
The vulnerability, classified as an SQL injection vulnerability, arises during the user login process. This flaw can be exploited by malicious actors to bypass authentication measures and gain unauthorized access to the Apache Submarine platform. The ramifications of this breach could be severe, potentially compromising sensitive data and disrupting critical machine-learning operations.
Remediation Measures: Upgrade and Enhance Security
Apache has promptly addressed the CVE-2023-37924 vulnerability in the latest release, Apache Submarine 0.8.0. Upgrading to this version effectively resolves the SQL injection vulnerability and bolsters security by implementing OpenID Connect (OIDC) authentication. This robust authentication mechanism eliminates the possibility of unauthenticated logins, further safeguarding the platform.
Recommendations for Affected Users
For users currently running Apache Submarine 0.7.0 or lower, upgrading to version 0.8.0 is strongly recommended. This upgrade not only rectifies the SQL injection vulnerability but also introduces OIDC authentication and eliminates the risk of unauthenticated access.
Alternative Approach for Users Hesitant to Upgrade
If upgrading to Apache Submarine 0.8.0 is not immediately feasible, users can opt for an alternative approach. This involves manually applying the relevant patch from the fix PR [1, 2] and rebuilding the submarine-server image. While this method addresses the vulnerability, it falls short of the security enhancements introduced in the latest release.