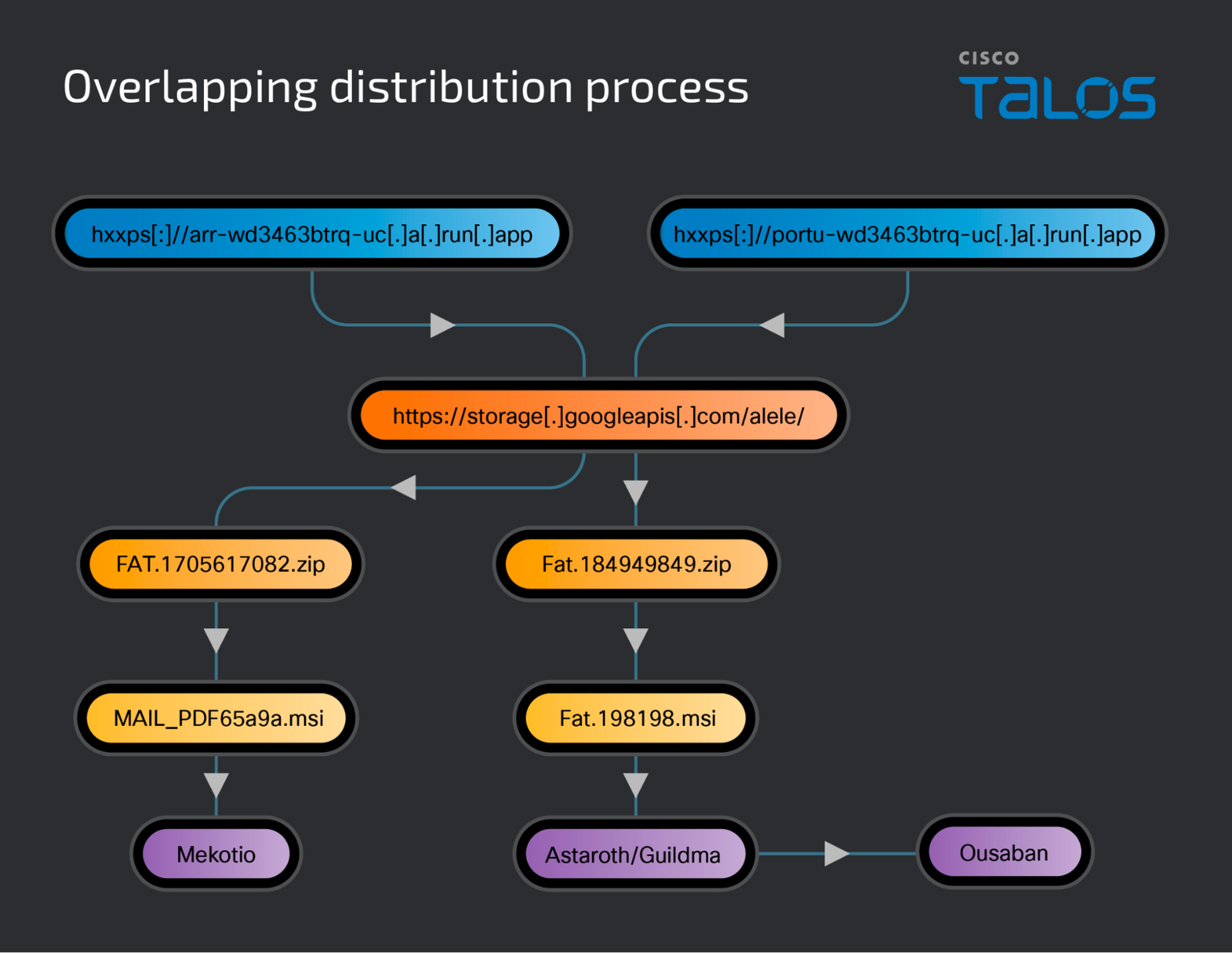
Phishing-as-a-Service Threatens Canada’s Banks
LabHost has emerged as a pivotal tool for cybercriminals in their assaults on North American banks, particularly targeting financial institutions in Canada. This Phishing-as-a-Service (PHaaS) provides malefactors with an array of tools for orchestrating...