Black Basta & Bl00dy Exploit ScreenConnect Flaw
Cybercriminal groups Black Basta and Bl00dy have joined the mass attacks on vulnerable ScreenConnect servers, targeting all users who have not yet updated their systems.
A fix for the critical authentication bypass vulnerability (CVE-2024-1709) is already available. This bug allows attackers to create administrative accounts on open servers, delete all other users, and gain full control over any system.
Hackers began exploiting CVE-2024-1709 just a day after ConnectWise released updates and several companies published POC exploits.
Last week, ConnectWise also patched a critical directory traversal vulnerability (CVE-2024-1708), which could only be exploited by attackers with high privileges.
The company has removed all licensing restrictions so that clients with expired licenses can protect themselves from current attacks, as these two issues affect all versions of ScreenConnect.
On Thursday, CISA also added CVE-2024-1709 to its catalog of known exploited vulnerabilities, ordering U.S. federal agencies to take protective measures by February 29.
According to Shadowserver, the vulnerability is already being actively exploited in practice, with dozens of IP addresses targeting open online ScreenConnect servers. The Shodan service tracks more than 10,000 such servers, of which only 1,559 are running the patched version 23.9.8.
In analyzing incidents, Trend Micro discovered that the Black Basta and Bl00dy groups have also begun exploiting defects in ScreenConnect for initial access and backdoor installation.
Analysts report that after gaining access to victims’ networks, attackers conduct reconnaissance and elevate their privileges within the system. The Black Basta group used the Cobalt Strike tool to entrench compromised systems. Bl00dy employed malicious programs created using builders for Conti and LockBit that leaked online.
Additionally, attackers installed the multifunctional XWorm malware, which has the capabilities of a RAT and ransomware.
Some attackers used access to ScreenConnect servers to install remote management tools, such as Atera, Syncro, or additional instances of ConnectWise.
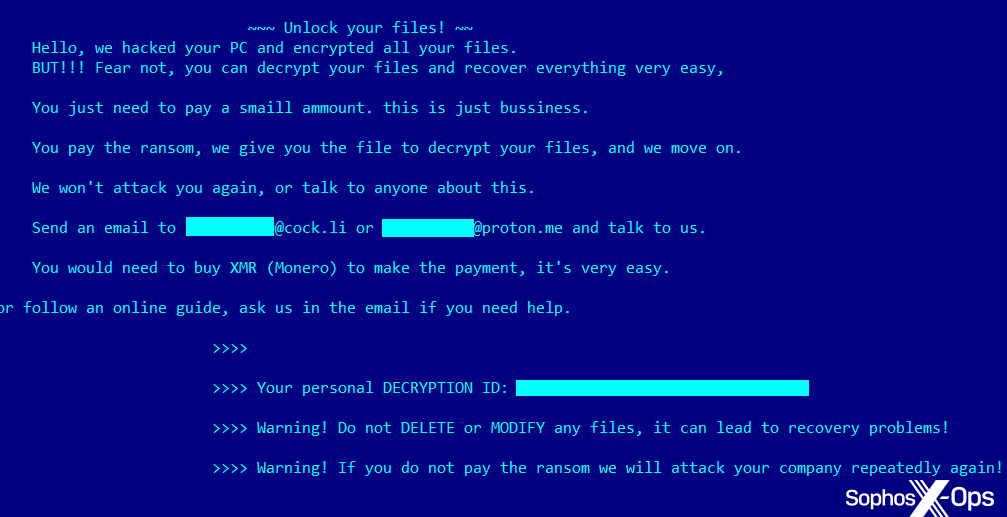
Sophos experts discovered several ransomware payloads created using the leaked LockBit builder, including buhtiRansom, found in 30 different networks.
Huntress also confirmed that CVE-2024-1709 has been involved in numerous incidents. In particular, it was used to attack local government bodies, including systems linked to the 911 service, and a large medical clinic.
As stated by Trend Micro after a detailed analysis of cyberattacks using ConnectWise ScreenConnect vulnerabilities, urgent updating to the latest software version is not just a recommendation but a critically important measure.





