Cuttlefish Malware Infects Routers, Steals Data
A new type of malware named “Cuttlefish” has been discovered in routers within major enterprises and small offices, monitoring all information passing through the infected devices and stealing credentials.
Black Lotus Labs reports that Cuttlefish creates a proxy or VPN tunnel on the router to covertly transmit data, circumventing detection systems that monitor suspicious system access.
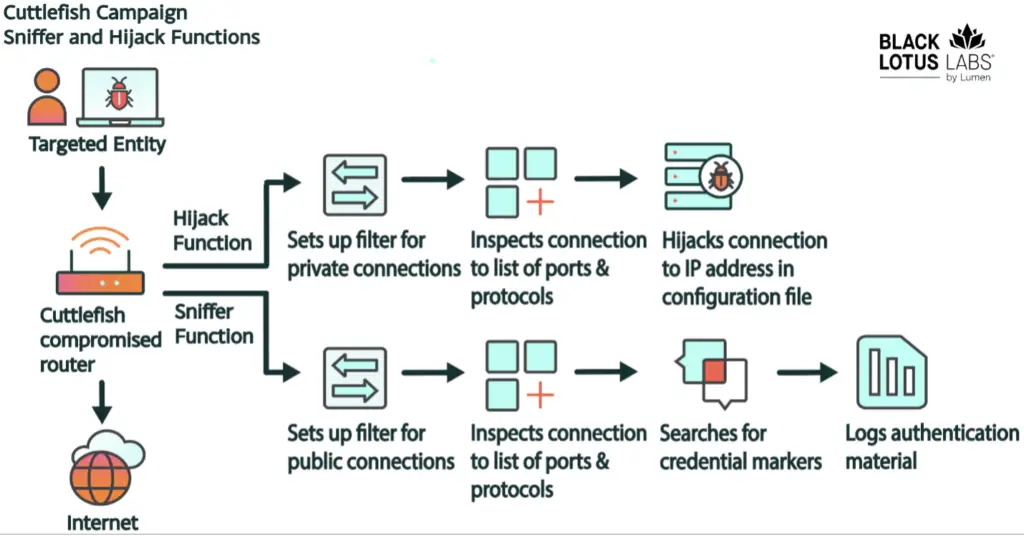
Flow diagram for packet filter and hijacking parameters
The malware intercepts DNS and HTTP requests within private networks, disrupting internal communications and downloading additional malicious modules.
Although part of Cuttlefish’s code resembles HiatusRat, which has been used in campaigns aligned with Chinese interests, no direct connection between these programs has been established.
Cuttlefish has been active since July 2023 and is leading an aggressive campaign in Turkey, also impacting satellite communication services and data centers in other regions.
The initial method of infecting routers has yet to be determined, but it likely exploits known vulnerabilities or brute-force credentials. Once access to a router is gained, a bash script is initiated that begins collecting data from the host, including directory listings, active processes, and connections.
The loaded script executes Cuttlefish’s main payload, which loads into memory to avoid detection, and the file is immediately deleted from the file system.
According to Black Lotus Labs, there are various versions of Cuttlefish for ARM, i386, and other architectures, covering a wide range of router types.
The malware uses packet filters to monitor all connections and, upon detecting certain data, executes actions according to pre-set rules, regularly updated from a control server.
Cuttlefish actively searches traffic for credential markers, such as usernames, passwords, and tokens, particularly those associated with cloud services. Captured data is stored locally and sent to the attackers once it reaches a certain volume.
To protect against Cuttlefish, network administrators are advised to eliminate weak passwords, monitor unusual system logins, use secure TLS/SSL protocols, check for suspicious files, and periodically reboot devices.
Additionally, particularly for budget routers, regularly checking for firmware updates, blocking remote access to the management interface, and promptly replacing devices after the support period ends are prudent measures.





