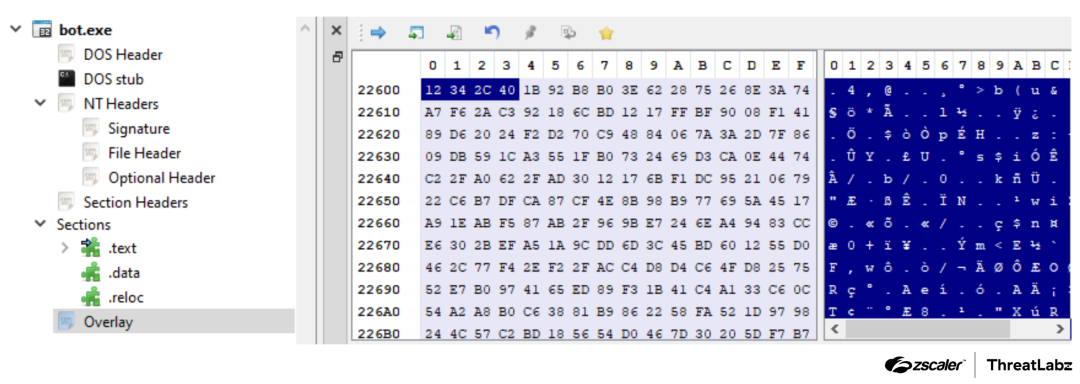
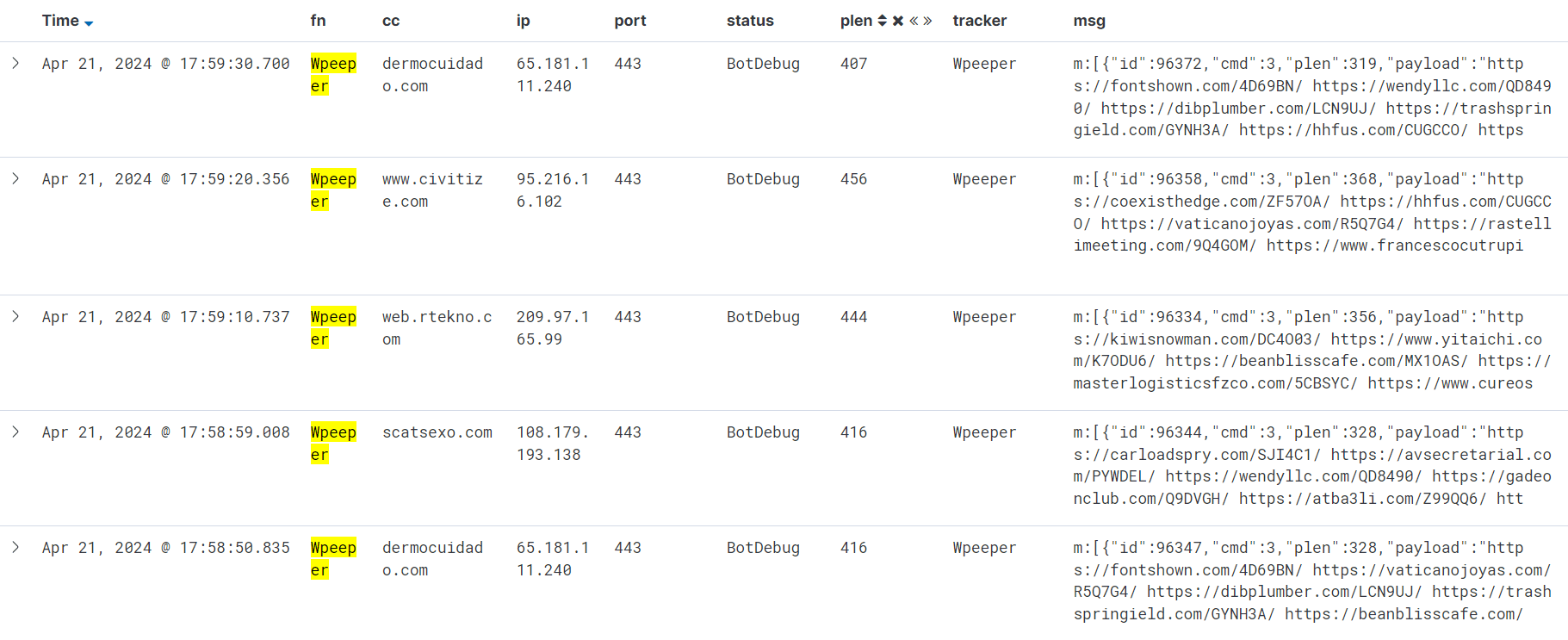
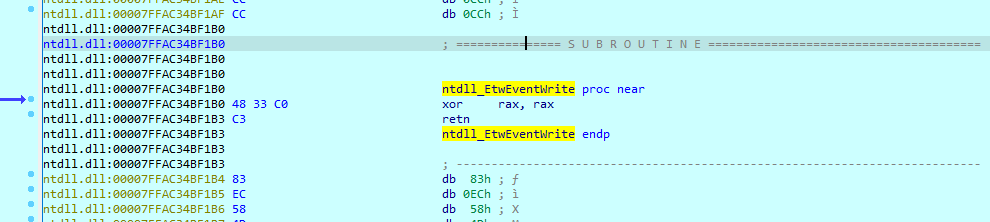
Google Ads Weaponized: FIN7 Targets Users with Malicious Brand Impersonations
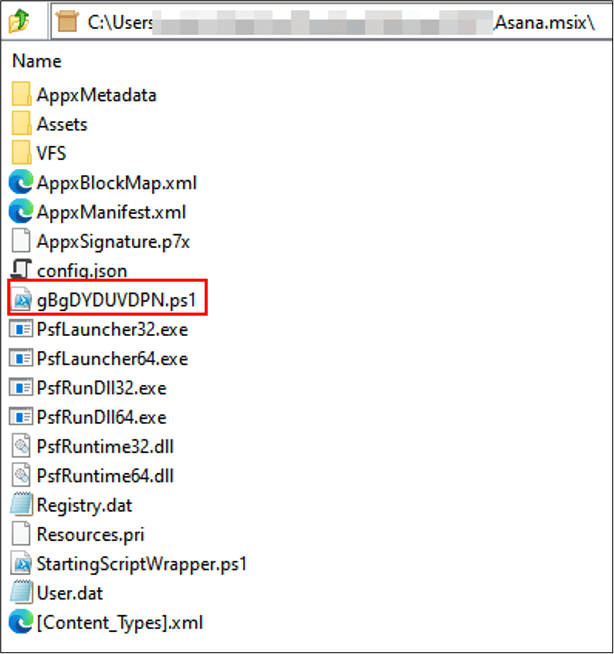
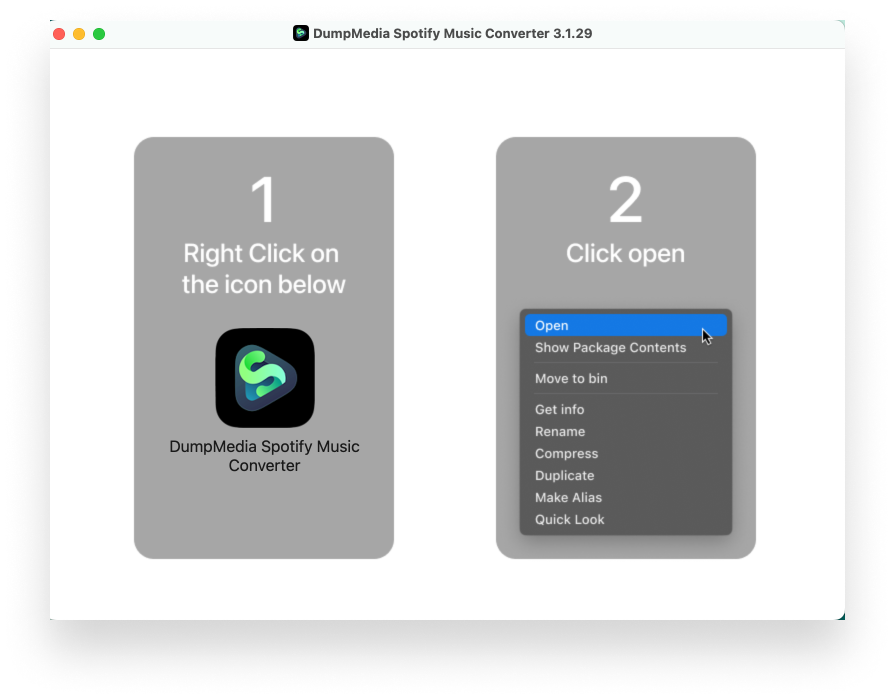
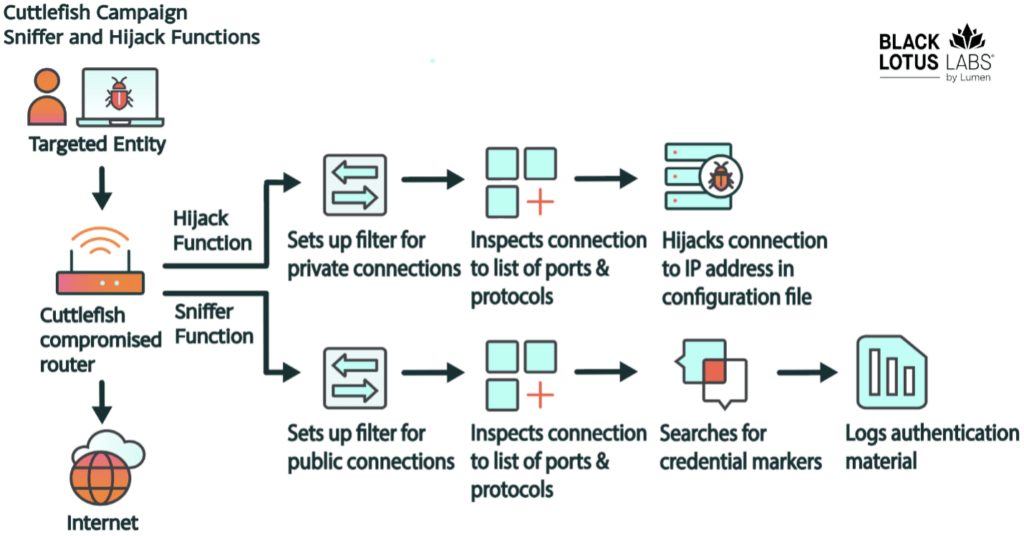
eSentire has reported a new wave of attacks by the FIN7 hacker group, which has disguised itself as well-known brands to distribute malware. The attacks targeted users who clicked on fake ads in Google,...