Fileless Attack: AgentTesla Strikes with .NET Injection
In a recent campaign involving the dissemination of the AgentTesla malware, as meticulously analyzed by experts at SonicWall, perpetrators employed VBA macros in Word documents to conduct a fileless injection attack, where the malicious payload is directly loaded into the computer’s memory.
The malware is managed via the CLR hosting mechanism, which allows native Windows processes to execute .NET code using dynamically loaded .NET libraries, enabling the malware to operate without leaving any files on the disk.
A distinctive feature of the malware is the deactivation of the Event Tracing for Windows (ETW) system by modifying the “EtwEventWrite” API. Subsequently, the shellcode containing the AgentTesla payload is downloaded and executed using the “EnumSystemLocalesA” API.
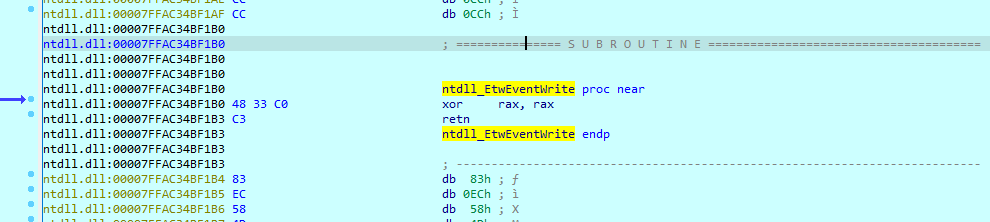
After the malware patches the “EtwEventWrite” API
This shellcode employs hashing to dynamically resolve APIs such as VirtualAlloc and VirtualFree, which helps to evade detection. It then allocates memory and writes the decoded AgentTesla payload for execution.
Should any required DLLs be missing, the malware loads them via the LoadLibraryA function. The shellcode also disables the AMSI scanning by modifying the “AmsiScanBuffer” and “AmsiScanString” functions.
To execute the malicious .NET code, the malware utilizes CLR hosting to create an instance of the CLR runtime, subsequently identifying a suitable version of .NET, loading the malicious code into the AppDomain, and initiating it. Once the malicious process is in the memory, the shellcode destroys the loaded data, preventing detection.
Thus, hackers are finding increasingly sophisticated ways to infect systems with malware, circumventing traditional detection methods. Such complex hacking techniques necessitate continual enhancement of protective mechanisms at all levels to ensure adequate cybersecurity.





