Telephone-based fraud schemes masquerading as customer support from well-known brands are rapidly gaining traction among cybercriminals. According to researchers at Cisco Talos, attackers are increasingly employing a method known as TOAD (Telephone-Oriented Attack Delivery), a reverse phishing technique conducted over the phone. These campaigns coerce victims into initiating contact with scammers posing as representatives of reputable companies.
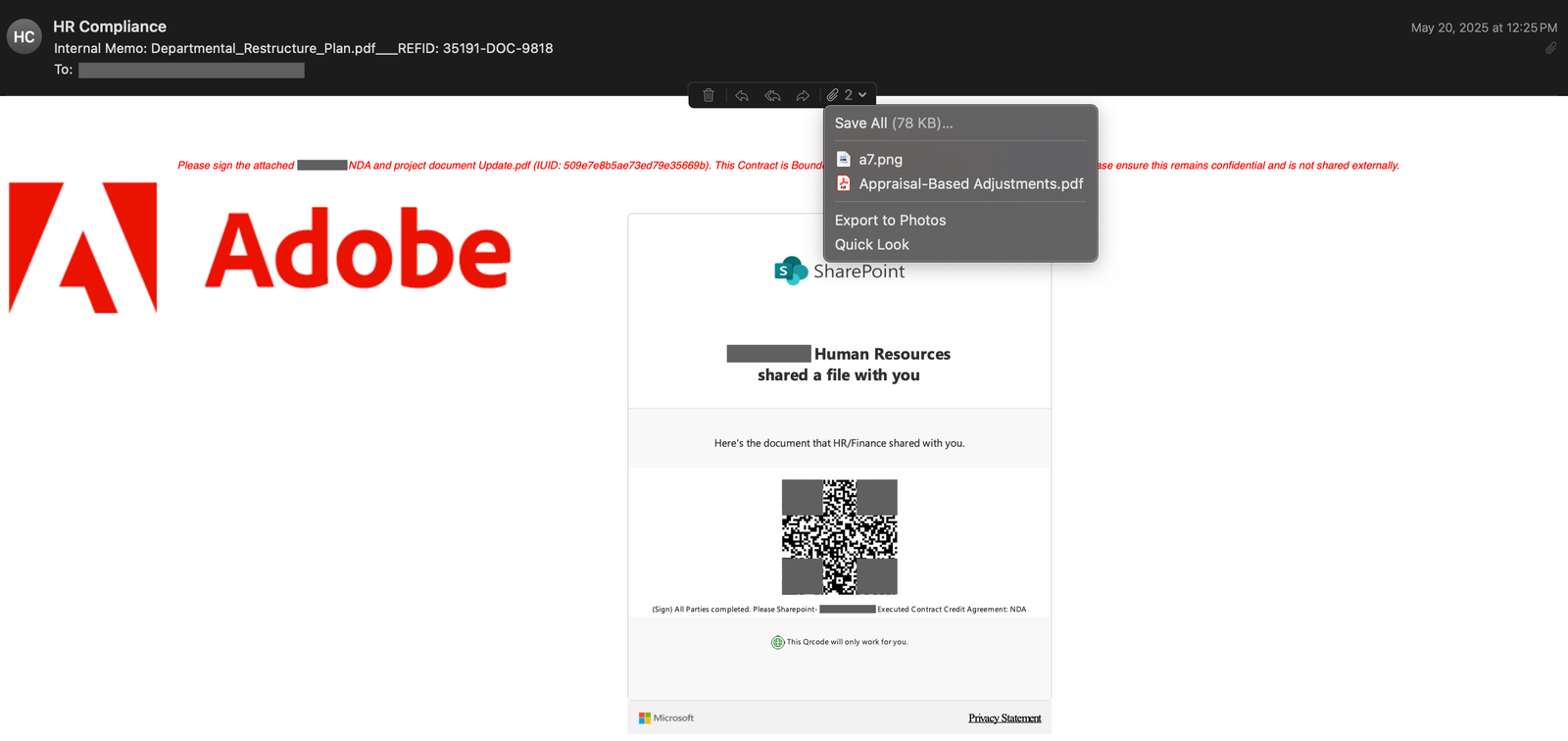
An analysis of malicious email campaigns containing PDF attachments, conducted between May 5 and June 5, 2025, revealed that the impersonation of Microsoft and DocuSign was most prevalent. Other frequently exploited brands included NortonLifeLock, PayPal, and Geek Squad. The attackers capitalize on users’ inherent trust in these names to prompt further engagement.
These phishing emails often contain PDF documents adorned with the logos of trusted companies such as Adobe or Microsoft, embedding QR codes that redirect users to counterfeit Microsoft login portals or fraudulent platforms mimicking services like Dropbox. In some instances, malicious links are concealed within annotations—such as sticky notes or comments—embedded in the PDF, a tactic that evades conventional security filters and enhances the perceived legitimacy of the message.
The defining characteristic of TOAD attacks lies in their reliance on social engineering to compel the recipient to call a phone number provided in the email, ostensibly to verify a transaction or resolve a technical issue. During the call, the scammer, posing as a support agent, persuades the victim to divulge sensitive information or install malware on their device.
The effectiveness of these schemes hinges on the level of sophistication: attackers deploy scripted dialogues, simulate authentic call center operations, use background hold music, and spoof caller IDs to enhance credibility. Typically, anonymous VoIP services are employed, with the fraudulent numbers remaining active for several days, enabling the execution of multi-layered deception strategies.
Cisco Talos experts note that these tactics are commonly used to install banking trojans on Android devices and to gain remote access to victims’ computers. Attackers often urge targets to install software such as AnyDesk or TeamViewer, granting them full control over the system.
In May 2025, the FBI issued an official alert regarding such campaigns orchestrated by the Luna Moth group, known for financial extortion schemes. Members of the group impersonate IT department staff to infiltrate corporate networks.
An emerging threat involves the abuse of the Direct Send feature in Microsoft 365. This technique allows attackers to dispatch phishing emails that appear to originate from within an organization, without compromising legitimate accounts. Exploiting the predictable format of internal email addresses, attackers circumvent standard authentication and security protocols. Since May 2025, more than 70 organizations have been targeted using this method.
These operations resemble traditional phone scams, tech support fraud, and business email compromise, but differ in their use of alternative communication channels and their intent to maintain persistent access. Beyond stealing credentials, attackers redirect victims to counterfeit payment portals or impersonate finance department personnel to harvest banking details.
In one notable incident on June 17, 2025, victims received an email styled as a voicemail notification, containing a PDF with a QR code. Scanning the code led to a fake Microsoft 365 login page. Experts explain that attacks leveraging Direct Send are less likely to be detected by conventional security systems, making them especially appealing to threat actors.
Cisco underscores that brand impersonation detection is a critical pillar in defending against these evolving threats, given the persistent popularity of social engineering tactics among cybercriminals.




