IT Pros Beware: MadMxShell Backdoor Exploits Fake Utilities
On April 17, researchers at Zscaler exposed a malicious software distribution campaign targeting IT professionals. This operation employs deceptive advertising of popular network utilities to implant a new backdoor named MadMxShell.
The campaign was initiated in March of this year when perpetrators registered domains closely mimicking the official sites of well-known software used for IP scanning and network administration, such as Advanced IP Scanner and Angry IP Scanner. This method, known as “Typosquatting,” significantly increases the likelihood that IT professionals might inadvertently click on a malicious link.
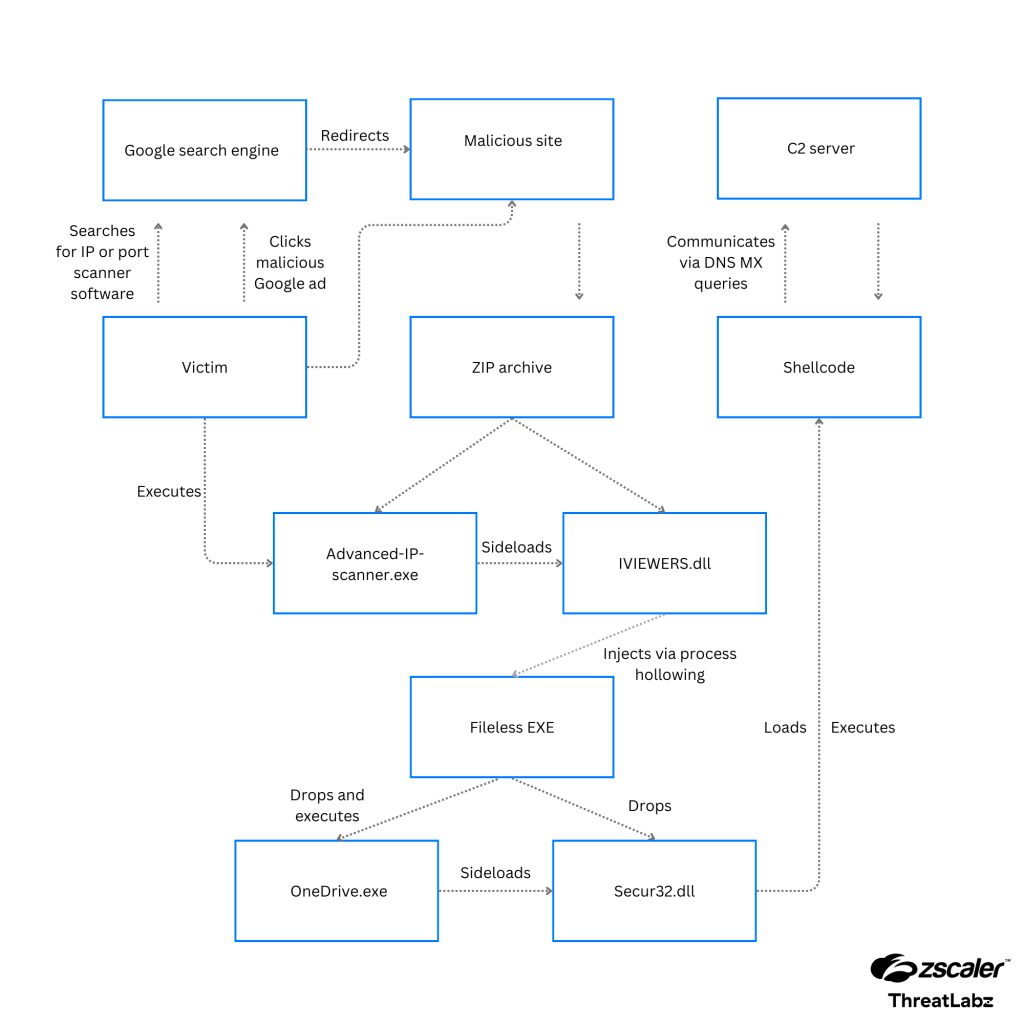
When users click on such advertisements, they are directed to a page that masquerades as the developer’s official site, where they are prompted to download a file containing the MadMxShell backdoor.
MadMxShell employs a complex, multistage deployment process that evades detection by standard security measures. The initial loading occurs through DLL Sideloading, where a legitimate program loads a malicious DLL library. This library, in turn, loads additional components that establish communication with the command server of the attackers.
One of the most concerning aspects of MadMxShell is its use of DNS MX queries for communicating with its command server. This technique exploits the standard DNS protocol unconventionally, complicating the tracking of malicious activity. Additionally, MadMxShell utilizes techniques that counteract memory analysis, making it difficult for security specialists to study its mechanisms.
To minimize risks, it is advisable to be wary of unauthorized advertisements, enable pop-up blockers, maintain robust security software, and educate employees about the dangers associated with malicious advertising and social engineering.





