The pentester's Swiss knife
KubeHound KubeHound creates a graph of attack paths in a Kubernetes cluster, allowing you to identify direct and multi-hop routes an attacker can take, visually or through complex graph queries. KubeHound can identify more...
dahn – Deceptively Adaptive Honey Net Traditional honey nets offer static infrastructure and static responses. In DAHN, the infrastructure is abstracted, with lambda/gpt API (prompts stipulated) returning seemingly native responses to the threat actor,...
Entraspray Entraspray is a rewrite of MSOLSpray in Python. The main purpose of this tool remains the same: to perform password spraying against Microsoft Azure accounts while also providing detailed information about account status...
Concealment Layer – Reverse Proxy for Concealing and Deceiving Website Information CLay offers a unique and powerful feature that goes beyond traditional security measures. CLay takes deception to a new level by mimicking the...
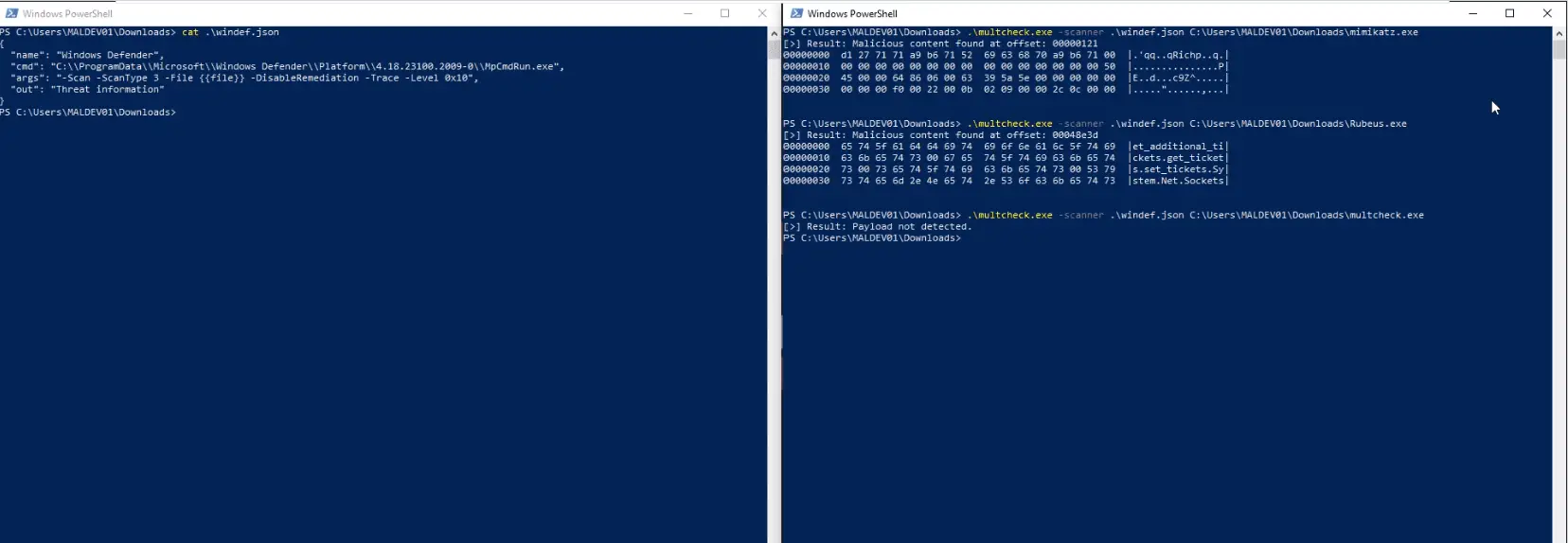
MultCheck MultCheck is a malware-analysis tool that can be used to test the detection of a file by multiple AV engines. It is designed to be easy to use and to be able to...
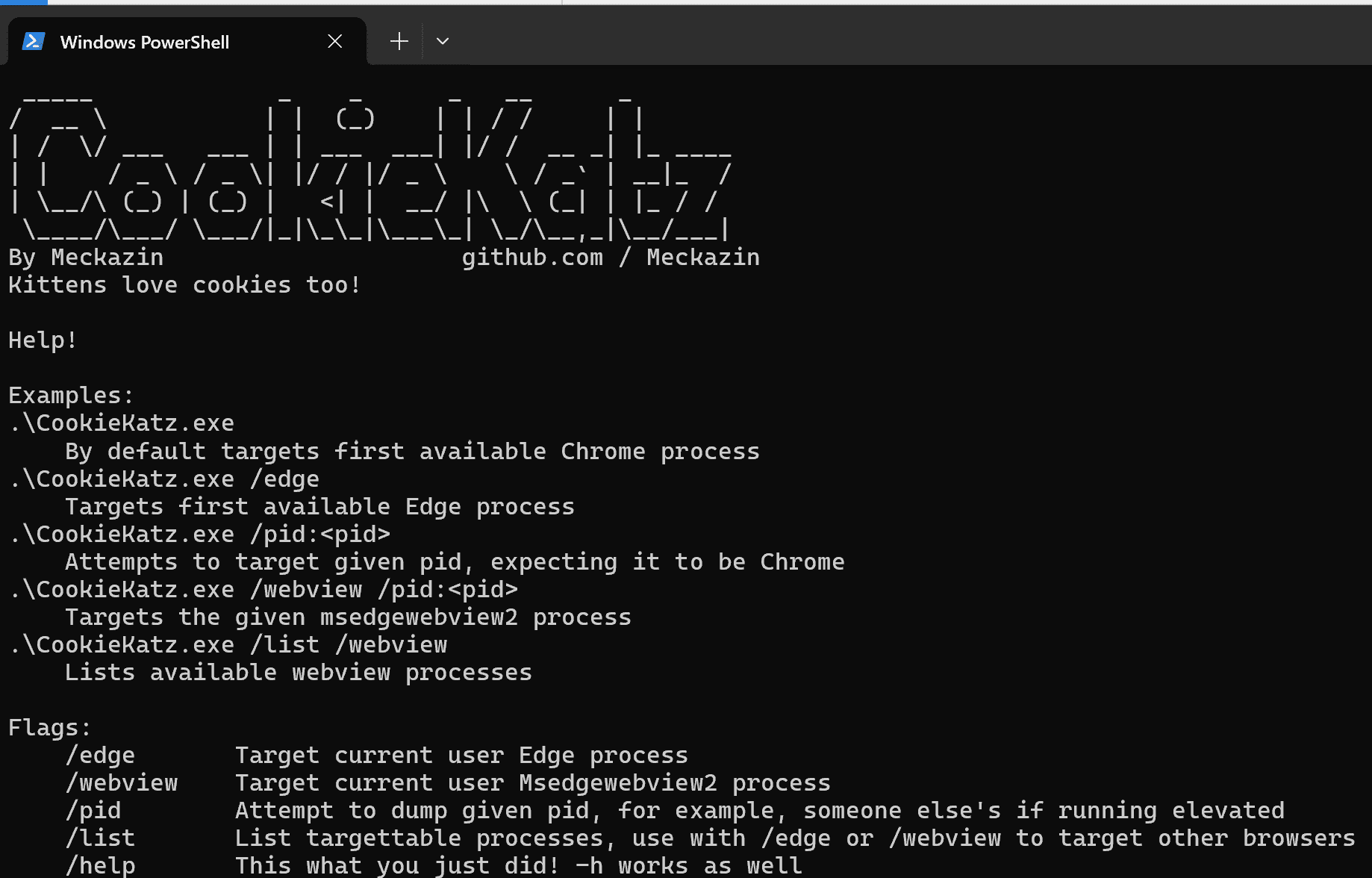
Cookie dumper for Chrome and Edge CookieKatz is a project that allows operators to dump cookies from Chrome, Edge, or Msedgewebview2 directly from the process memory. Chromium-based browsers load all their cookies from the...
SploitScan SploitScan is a powerful and user-friendly tool designed to streamline the process of identifying exploits for known vulnerabilities and their respective exploitation probability. Empowering cybersecurity professionals with the capability to swiftly identify and...
FormThief FormThief is a project designed for spoofing Windows desktop login applications using WinForms and WPF. Windows Forms (WinForms) and Windows Presentation Foundation (WPF) are two powerful UI frameworks provided by Microsoft for building...
Hiado Cross-projects Repository permissions enumeration Tool for Azure DevOps What does Hiado do? Hiado is a Python script that helps you enumerate information about the repositories your organization manages within Azure DevOps. Particular focus...
The HTTP Garden The HTTP Garden is a collection of HTTP servers and proxies configured to be composable, along with scripts to interact with them in a way that makes finding vulnerabilities much easier....
Reconic | All-in-One Reconnaissance Tool Reconic is a network scanning and discovery tool designed to empower cybersecurity professionals and bug hunters in mapping, analyzing, and securing digital infrastructures. Features WHOIS Lookup: Automates the retrieval...
Brazilian banking institutions have become the target of a new campaign disseminating a specialized variant of the AllaKore remote access trojan (RAT) for Windows, named AllaSenha. This RAT is designed to steal credentials necessary...
Check Point has reported that since late April, cybercriminals have been actively exploiting a critical vulnerability in the Check Point VPN remote access system, allowing them to steal Active Directory data for further infiltration...
Recently, Netflix reported that since the launch of its Bug Bounty program in 2016, the streaming giant has paid researchers over one million dollars in rewards for identifying bugs and vulnerabilities in the company’s...
A relatively new North Korean cyber group known as Moonstone Sleet has recently been identified as responsible for attacks on the software, information technology, education, and defense industries, utilizing ransomware and other types of...
Specialists at Zscaler have identified over 90 malicious applications on Google Play, designed to distribute malware and adware, including the banking trojan Anatsa. These applications have been downloaded more than 5.5 million times. Description...