[PoC] CVE-2021-31166: HTTP Protocol Stack Remote Code Execution Vulnerability
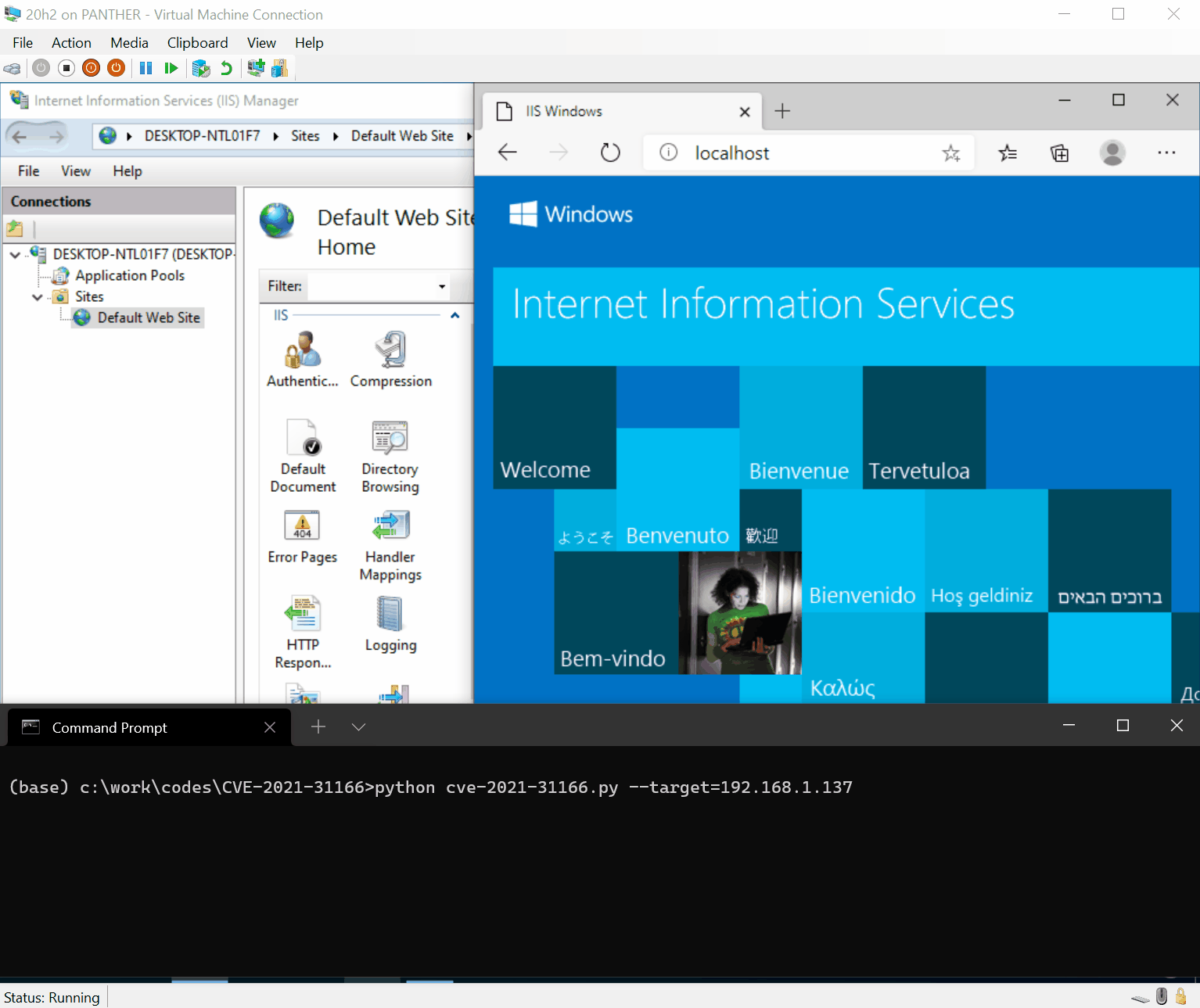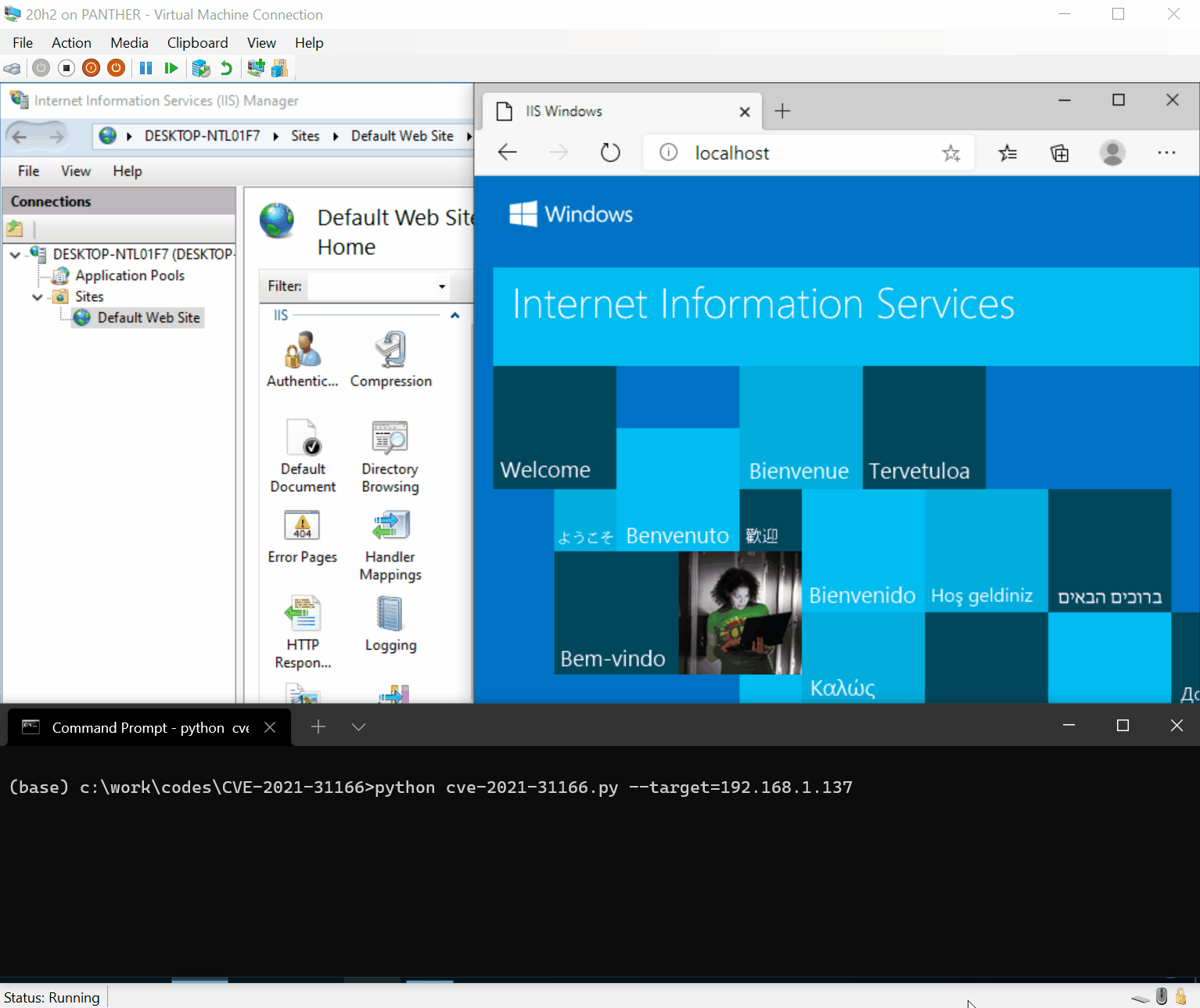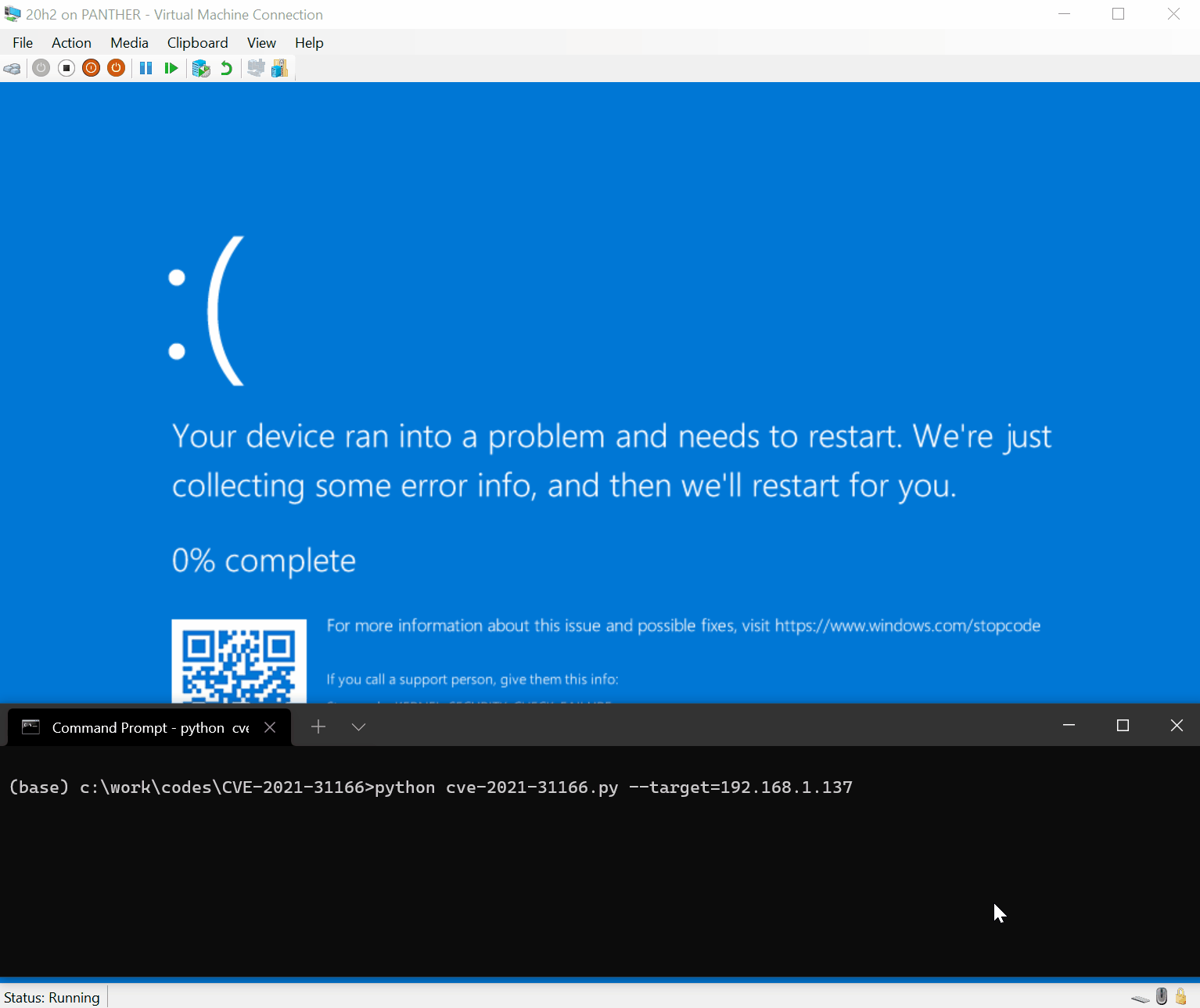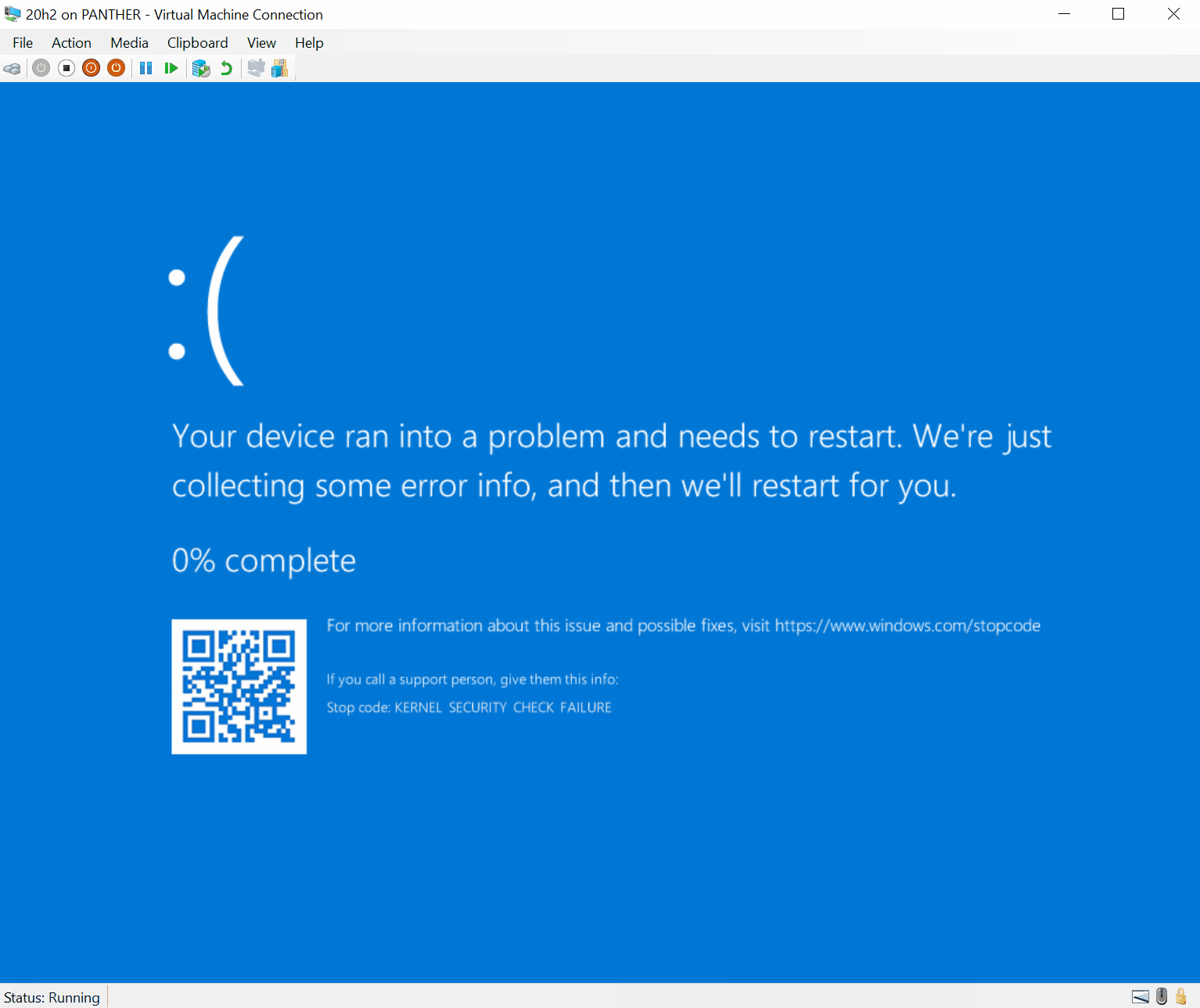
On May 11, Microsoft officially released the May security update patch, which fixes a remote code execution vulnerability in the HTTP protocol stack (CVE-2021-31166), which exists in the HTTP protocol stack (http.sys). In the processing program, an unauthenticated remote attacker can exploit this flaw by sending specially crafted data packets to the target host to execute arbitrary code as the kernel on the target system.

Affected version
- Windows Server, version 20H2 (Server Core Installation)
- Windows 10 Version 20H2 for ARM64-based Systems
- Windows 10 Version 20H2 for 32-bit Systems
- Windows 10 Version 20H2 for x64-based Systems
- Windows Server, version 2004 (Server Core installation)
- Windows 10 Version 2004 for x64-based Systems
- Windows 10 Version 2004 for ARM64-based Systems
- Windows 10 Version 2004 for 32-bit Systems
Solution
At present, Microsoft has officially released a security patch to fix this vulnerability for the supported Windows 10 version. It is strongly recommended that affected users install the patch as soon as possible for protection.
Update:
On May 16, a security researcher publishes the PoC for this vulnerability. Researcher writes:
The bug itself happens in
http!UlpParseContentCodingwhere the function has a localLIST_ENTRYand appends item to it. When it’s done, it moves it into theRequeststructure; but it doesn’t NULL out the local list. The issue with that is that an attacker can trigger a code-path that frees every entries of the local list leaving them dangling in theRequestobject.