CVE-2021-3044: Palo Alto Networks Cortex XSOAR improper authorization vulnerability alert
Unauthenticated attackers can access the API provided by Cortex XSOAR through this vulnerability, and create or execute scripts to start the corresponding automated processes to access sensitive data, execute commands, and other related operations.
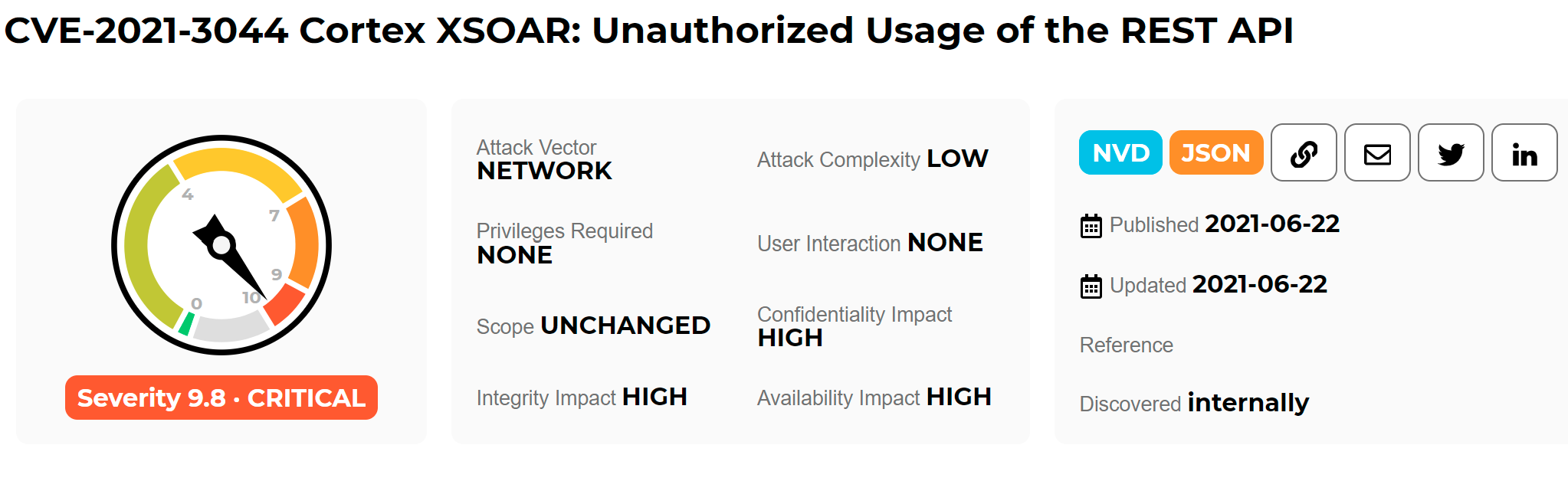
This vulnerability requires no high user permissions, no user interaction, and a low attack complexity. However, its utilization value largely depends on the functions of the REST API itself. At the same time, SOAR’s executors generally run in a sandbox, and other vulnerabilities may be required to complete the sandbox escape and intrusion into a specific physical machine.
Vulnerability Detail
An improper authorization vulnerability in Palo Alto Networks Cortex XSOAR enables a remote unauthenticated attacker with network access to the Cortex XSOAR server to perform unauthorized actions through the REST API.
Affected version
Cortex XSOAR 6.1.0 builds later than 1016923 and earlier than 1271064;
Cortex XSOAR 6.2.0 builds earlier than 1271065.
Solution
In this regard, we recommend that users upgrade Cortex XSOAR to the latest version in time.





