CVE-2021-21998: VMware Carbon Black App Control authentication bypass vulnerability alert
VMware Carbon Black Cloud Workload (AppC) is a software-as-a-service (SaaS) solution that provides services such as next-generation anti-virus (NGAV), endpoint detection and response (EDR), advanced threat search, and vulnerability management, widely used in cloud hosting.
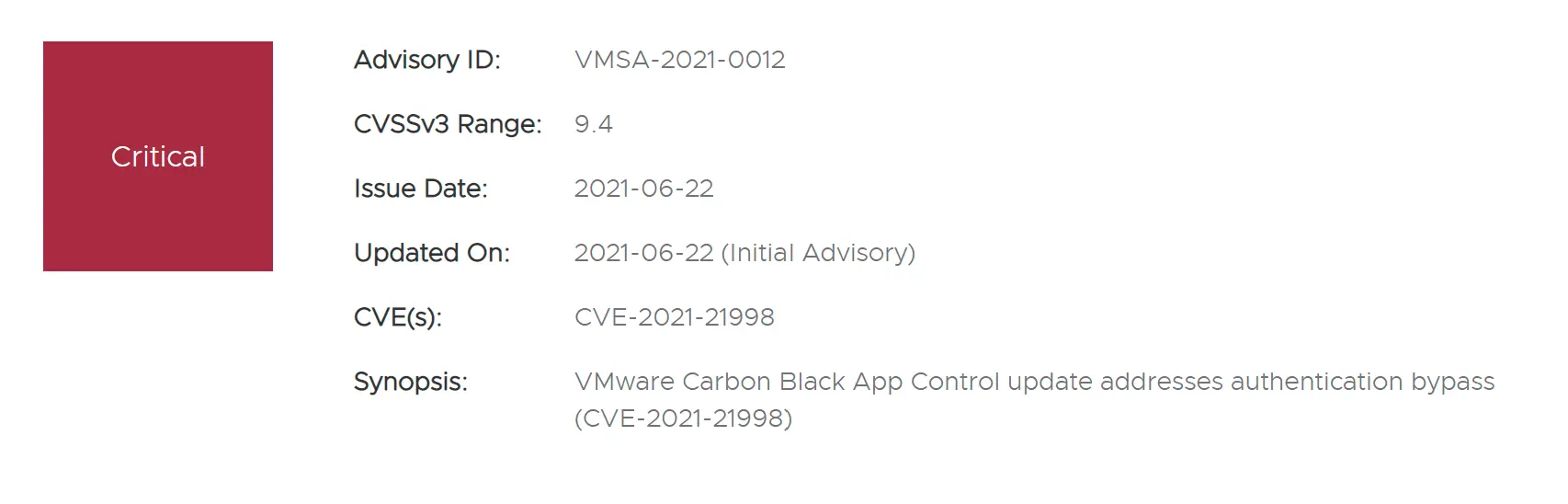
On June 22, 2021, VMware released a risk notice for Carbon Black App Control authentication bypass vulnerability, the vulnerability number is CVE-2021-21998 with a CVSSv3 score of 9.4. Attackers can use this vulnerability to gain administrative access to the product without authentication.
The vulnerability does not require any pre-authorization requirements, and the attack can be completed without user interaction, and the special permissions of the vulnerability can be used to access other cloud hosts and obtain permissions. The attack complexity is low and the use-value is high.
Vulnerability Detail
A malicious actor with network access to the VMware Carbon Black App Control management server might be able to obtain administrative access to the product without the need to authenticate.
Affected version
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
|
AppC
|
8.6.x
|
Windows
|
CVE-2021-21998
|
Critical
|
None
|
None
|
||
|
AppC
|
8.5.x
|
Windows
|
CVE-2021-21998
|
Critical
|
None
|
None
|
||
|
AppC
|
8.1.x, 8.0.x
|
Windows
|
CVE-2021-21998
|
Critical
|
None
|
None
|
Solution
In this regard, we recommend that users upgrade VMware Carbon Black App Control to the latest version in time.