Category: Open Source Tool
Kereva LLM Code Scanner is a static analysis tool designed to identify potential security risks, performance issues, and vulnerabilities in Python codebases that use Large Language Models (LLMs). It analyzes your code without execution...
Docker for Pentesters Docker containerization is the most powerful technology in the current market so I came up with the idea to develop Docker images for Pentesters. Nightingale contains all the required well-known tools...
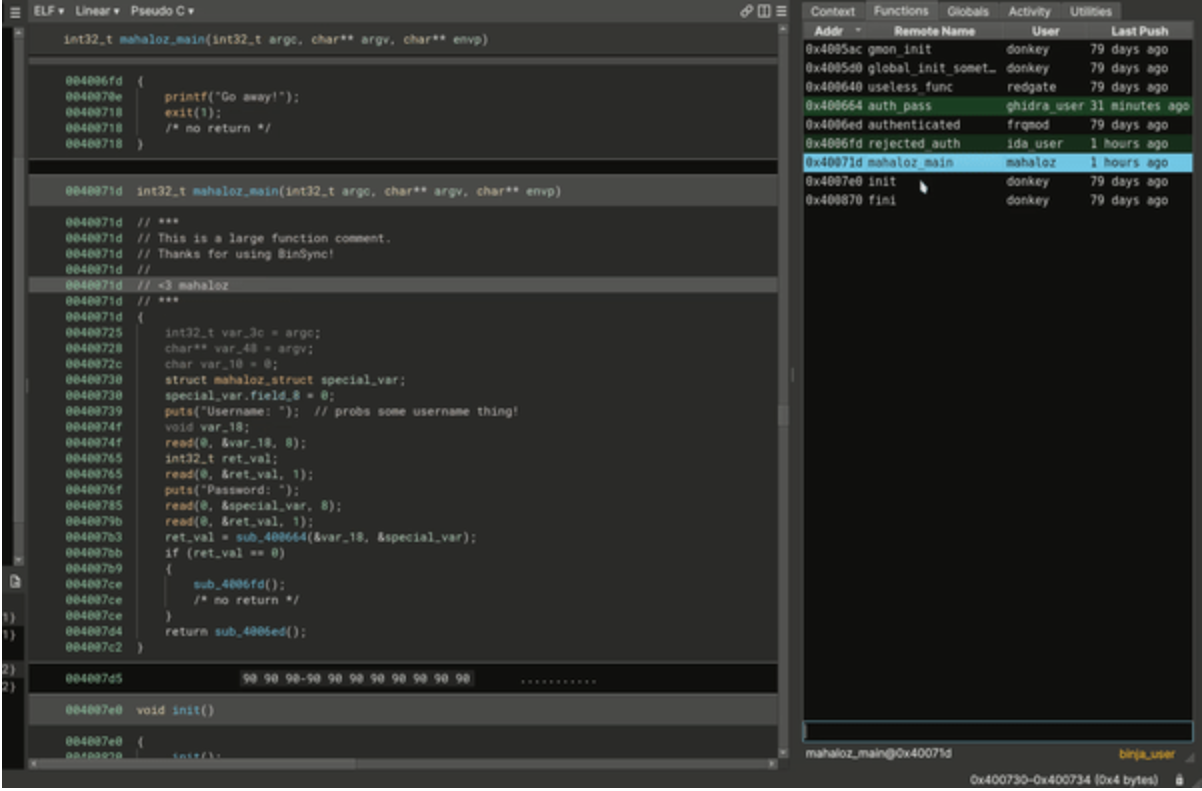
BinSync is a decompiler collaboration tool built on the Git versioning system to enable fined-grained reverse engineering collaboration regardless of decompiler. BinSync is built by mahaloz, the angr team, and the SEFCOM research lab. It’s also due in large...
gowitness gowitness is a website screenshot utility written in Golang, that uses Chrome Headless to generate screenshots of web interfaces using the command line, with a handy report viewer to process results. Both Linux and...
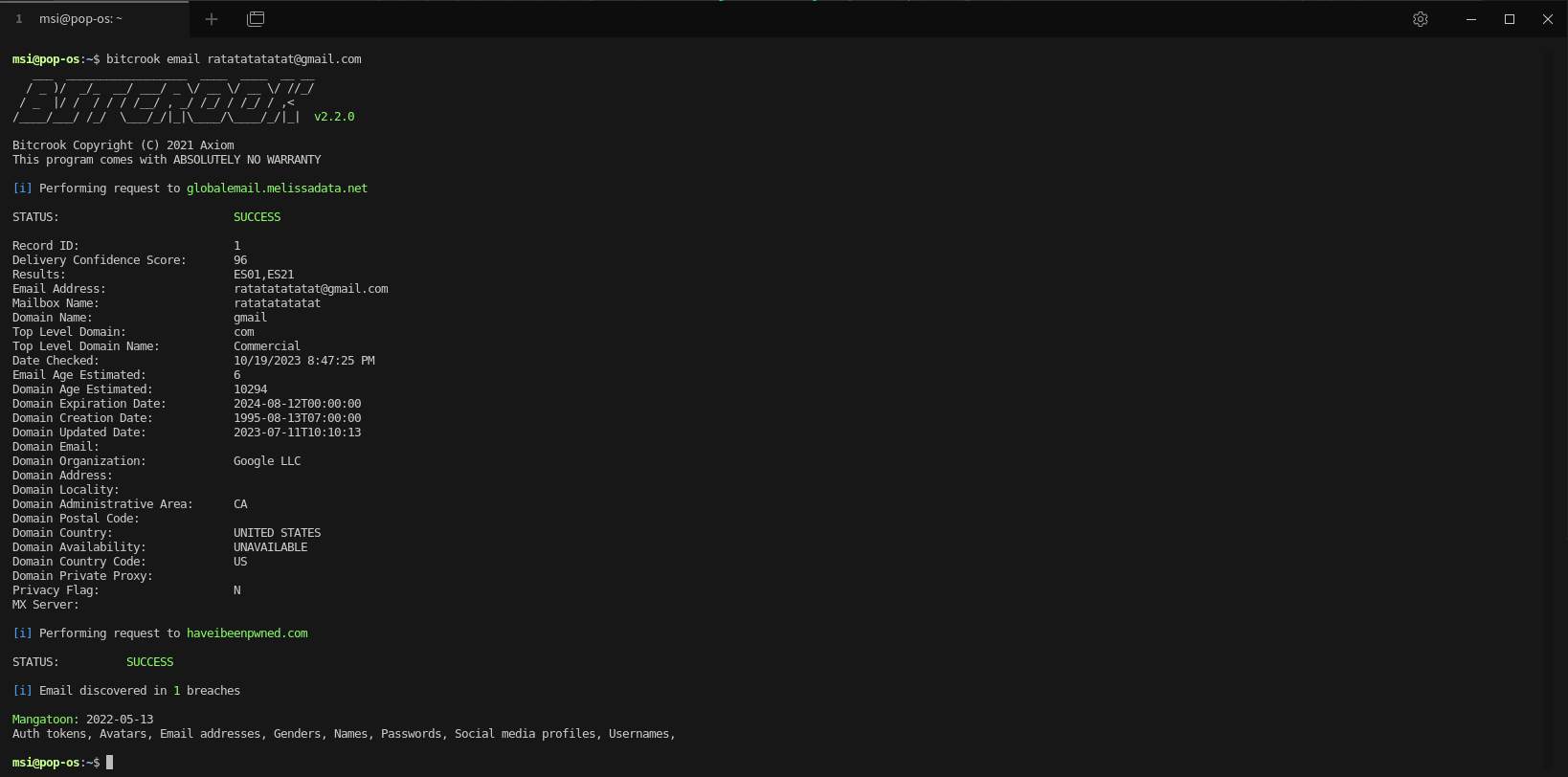
bitcrook Bitcrook is an open-source intelligence apparatus that aims to centralize all of the tools necessary to carry out an investigation. Although investigations will still require human interaction to connect the dots, the interface...
BFScan – Tool for initial processing of APK / XAPK / DEX / JAR / WAR applications. Search for strings in source code and resources that look like URIs, paths, or secrets Generate raw...
VAmPI The Vulnerable API (Based on OpenAPI 3) VAmPI is a vulnerable API made with Flask and it includes vulnerabilities from the OWASP top 10 vulnerabilities for APIs. It was created as I wanted a...
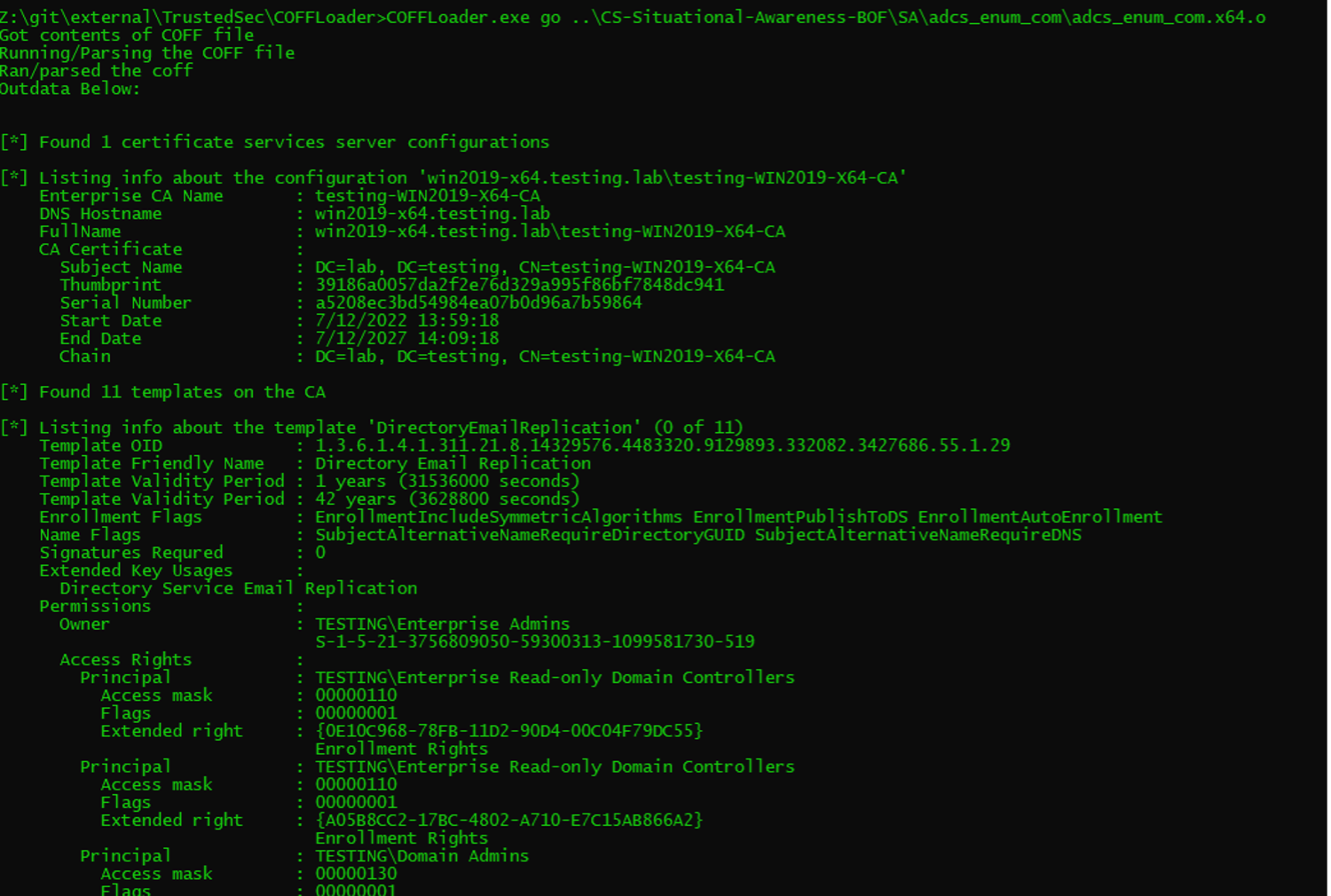
Beacon Object File (BOF) support has been at the cornerstone of capability for any modern C2 platform since its inception by Cobalt Strike 4.1 back in 2020. It was a major step forward towards...
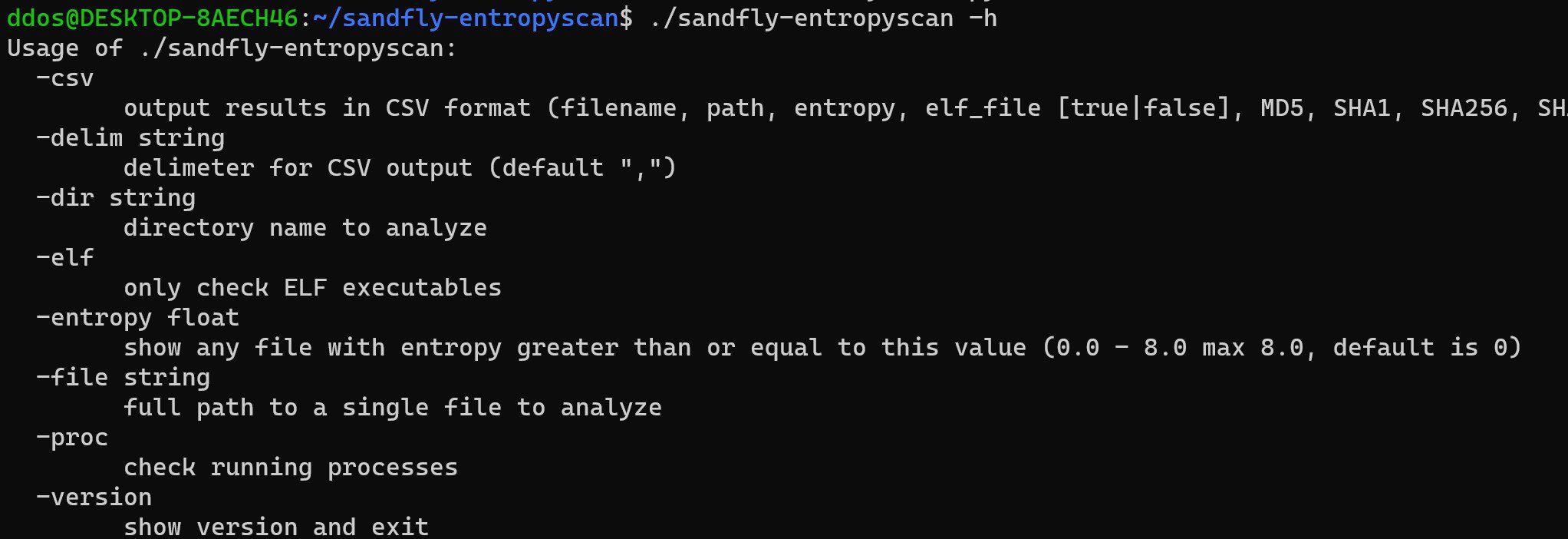
What is sandfly-entropyscan? sandfly-entropyscan is a utility to quickly scan files or running processes and report on their entropy (a measure of randomness) and if they are a Linux/Unix ELF type executable. Some malware for...
This repository contains a suite of Burp Suite extensions developed in Jython, designed to enhance the capabilities of penetration testers and security researchers when interacting with AI applications and performing prompt-based security testing. The...
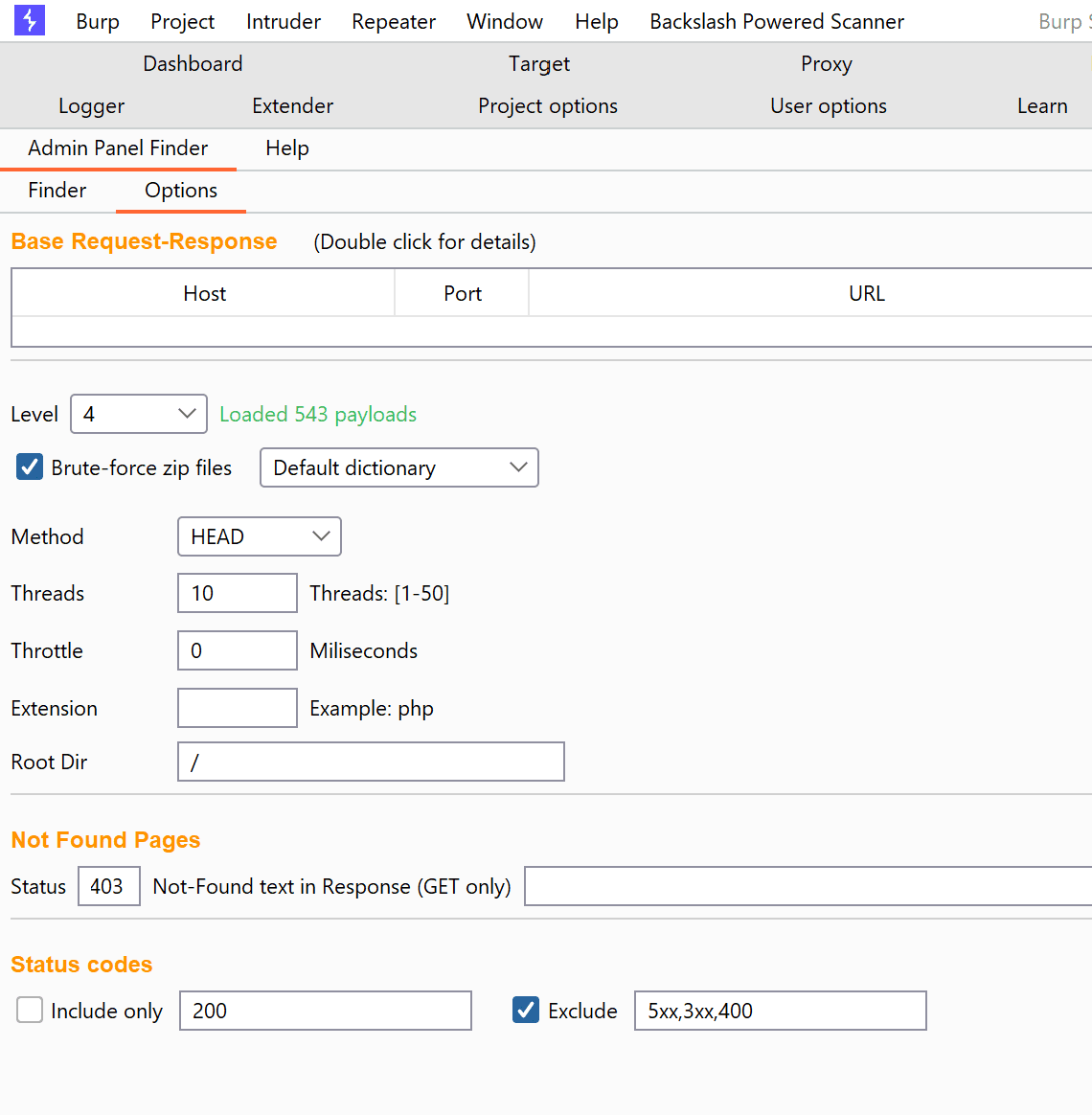
Admin Panel Finder A Burp Suite extension that enumerates infrastructure and application Admin Interfaces. OWASP References: Classification: Web Application Security Testing > 02-Configuration and Deployment Management Testing OTG v4: OWASP OTG-CONFIG-005 WSTG: WSTG-CONF-05 Why should...
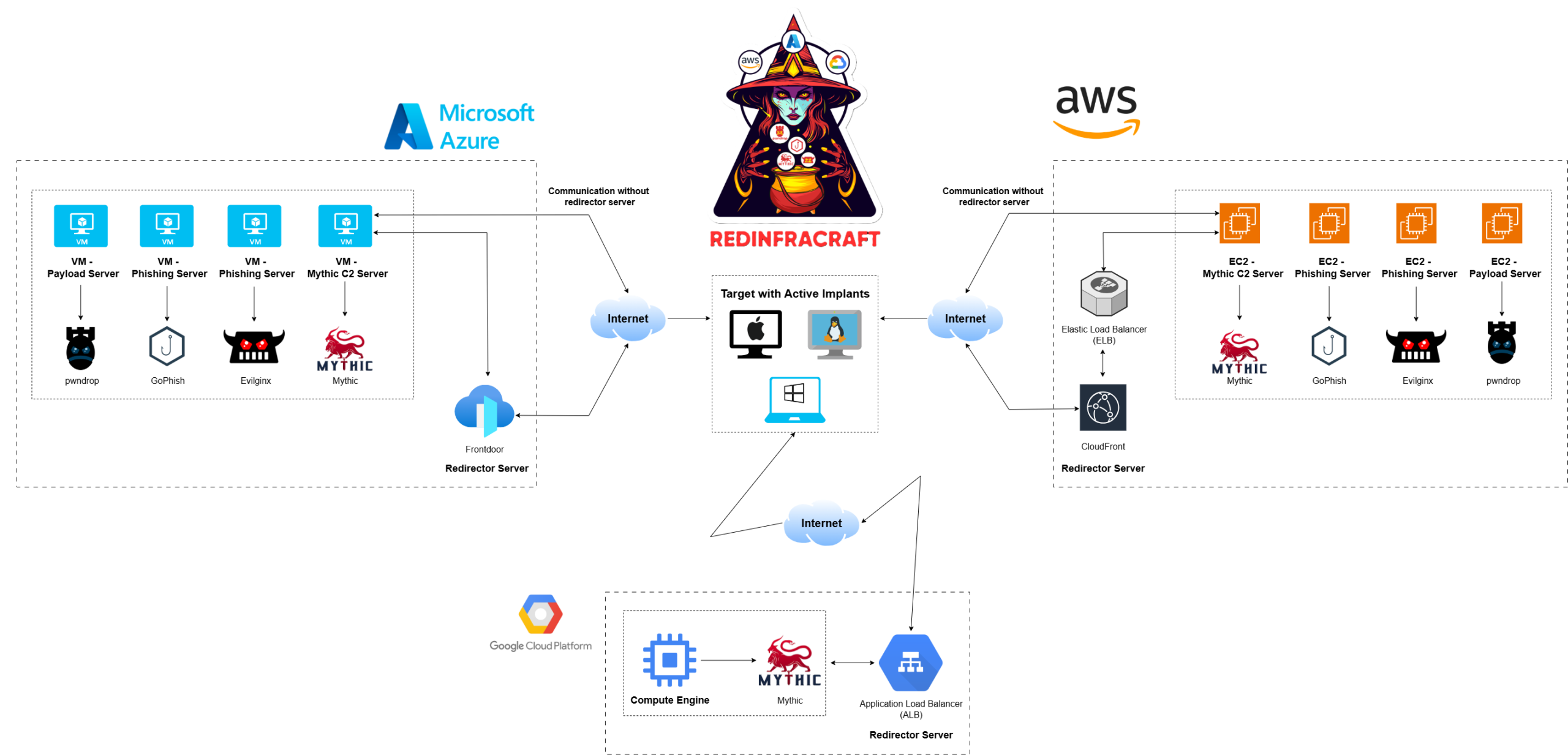
Welcome to the RedInfraCraft (V2) Tool – your gateway to automating the deployment of robust red team infrastructures! RedInfraCraft is your trusted companion in effortlessly setting up and managing red team infrastructures, streamlining the process so...
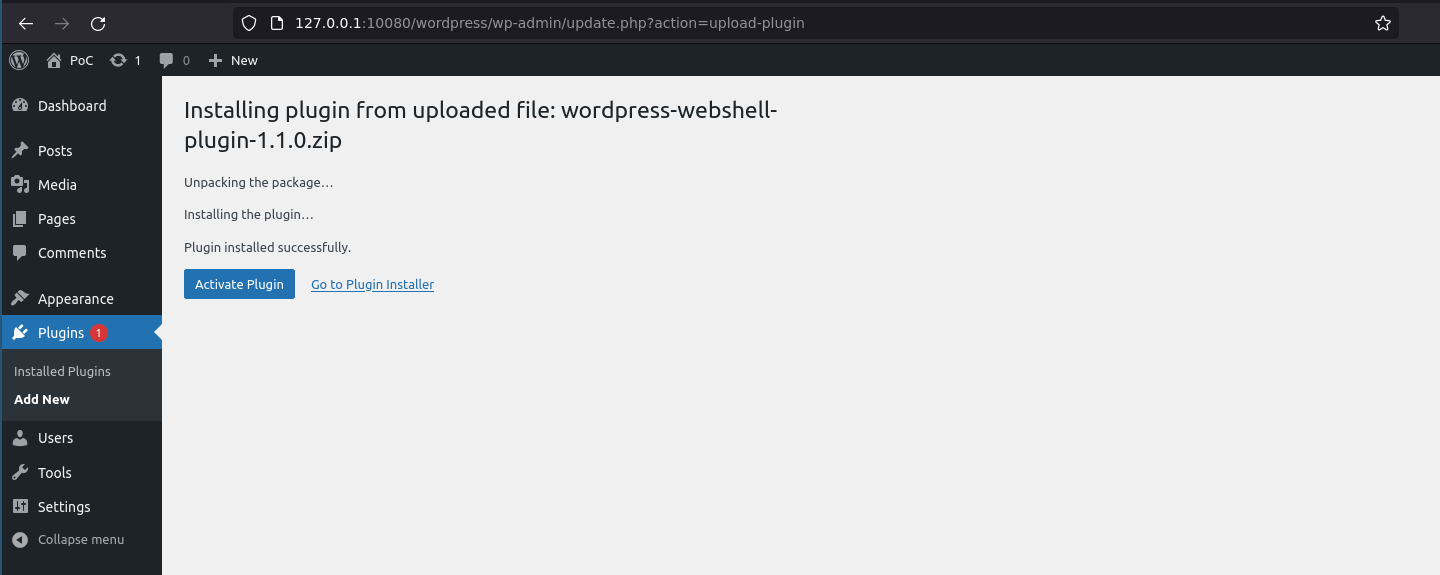
WordPress webshell plugin for RCE A webshell plugin and interactive shell for pentesting a WordPress website. Features Webshell plugin for WordPress. Execute system commands via an API with ?action=exec. Download files from the remote system...
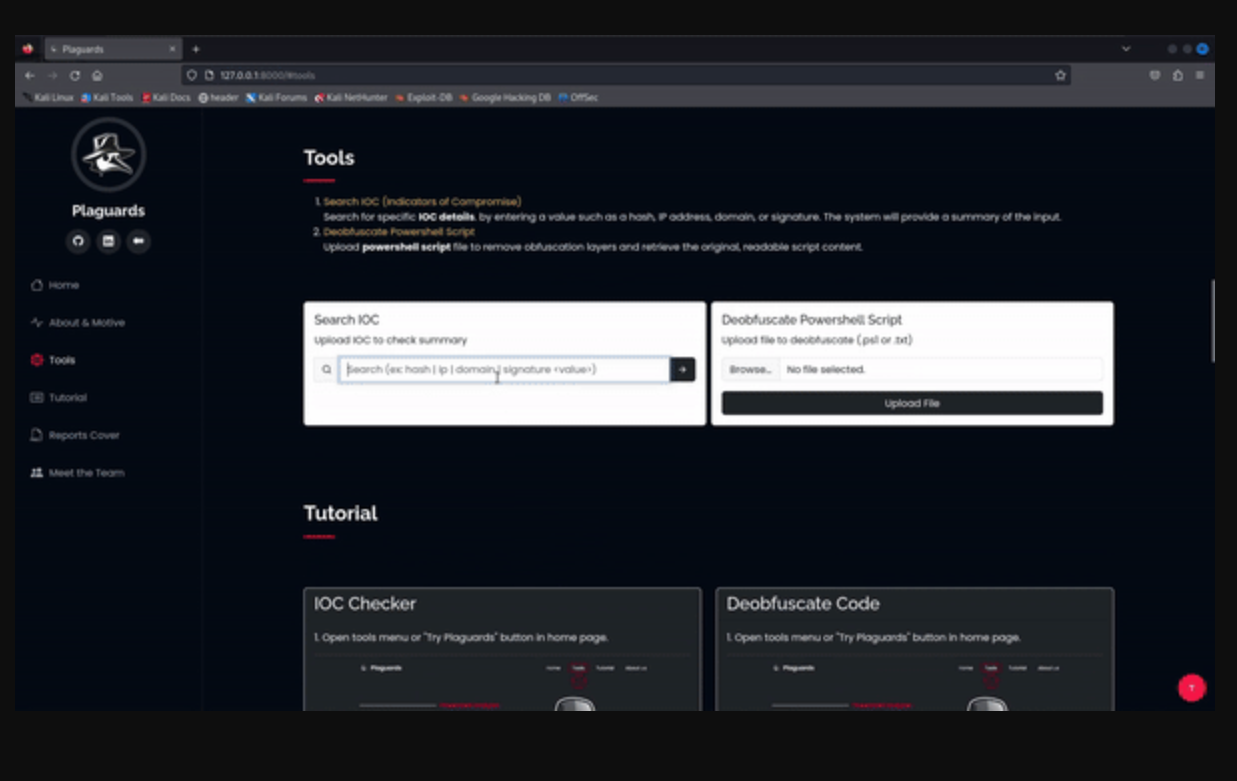
Plaguards is a cutting-edge security tool built to streamline and automate the deobfuscation of obfuscated PowerShell scripts, empowering security teams to rapidly identify Indicators of Compromise (IOCs) and determine whether they represent valid threats...
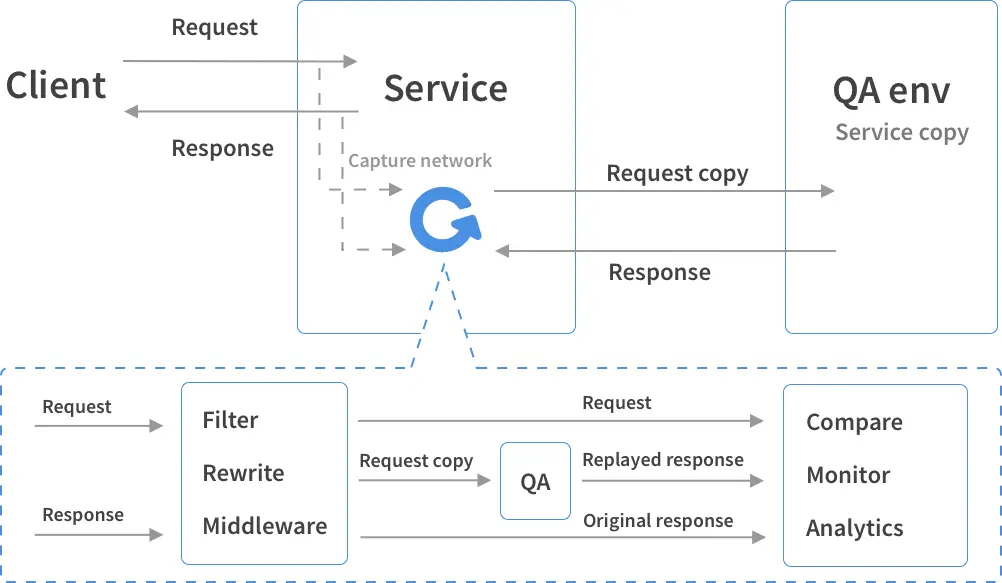
goreplay GoReplay is an open-source network monitoring tool which can record your live traffic and use it for shadowing, load testing, monitoring, and detailed analysis. As your application grows, the effort required to test...
BOAZ (Bypass, Obfuscate, Adapt, Zero-trace) evasion was inspired by the concept of multi-layered approach which is the evasive version of defence-in-depth first mentioned in “One packer to rule them all” at BH USA14 (Swinnen...