Category: Information Security
Unknown cybercriminals hacked the official Netgear and Hyundai MEA accounts on X, which boast over 160,000 followers. The objective of the attack was to disseminate fraudulent schemes aimed at infecting victims with malware designed...
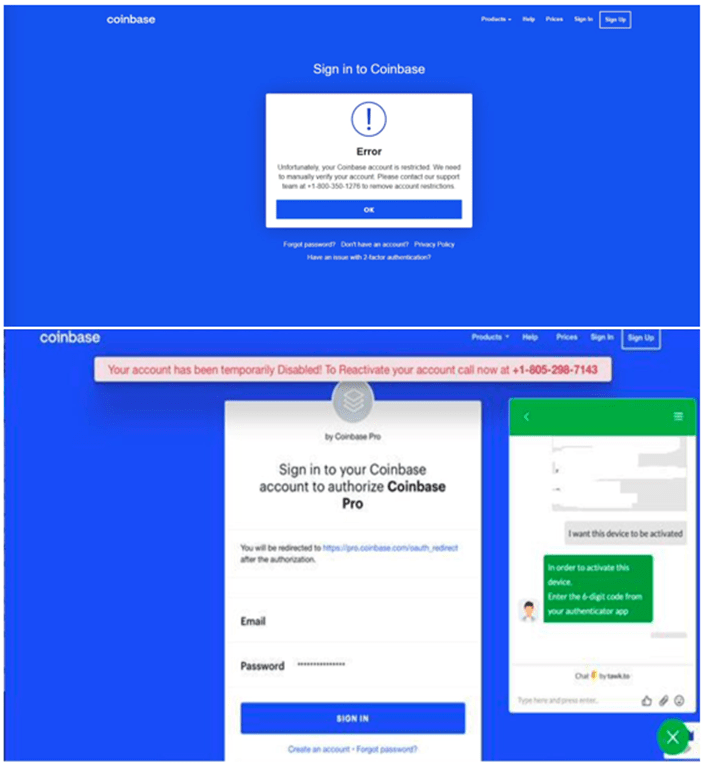
In a collaborative investigation by 404 Media and the independent analytical center Court Watch, a massive cyber-fraud scheme was uncovered, affecting over 500 users of the cryptocurrency exchange Coinbase, with losses exceeding $20 million....
Researchers have calculated that nearly 11 million SSH servers on the internet are vulnerable to Terrapin attacks, which allow data manipulation during the handshake process, ultimately compromising the integrity of the SSH channel when...
Due to restricted access to international financial markets, Iran has actively embraced cryptocurrency. Last year, Iranian cryptocurrency exchanges conducted transactions totaling nearly $3 billion. Almost all incoming cryptocurrency in Iran complies with Know Your...
The ShadowServer platform daily uncovers hundreds of IP addresses scanning or attempting to exploit Apache RocketMQ services vulnerable to Remote Code Execution (RCE), identified as CVE-2023-33246 and CVE-2023-37582. Both vulnerabilities are critical and pertain...
The United States Attorney’s Office heralded the culmination of an extensive international cybercrime investigation, targeting the nefarious activities of the darknet marketplace, xDedic. Judicial documents revealed that xDedic illegally sold access credentials to servers...
The cryptocurrency payment gateway CoinsPaid has encountered its second cyberattack in the last six months. According to the Web3 security firm Cyvers, unauthorized transactions amounting to approximately 7.5 million dollars were detected. On January...
QNAP Systems published security advisories for 15 vulnerabilities, each posing a unique challenge to the integrity of their systems. From OS command injections to SQL injections, each flaw uncovered in their operating systems and...
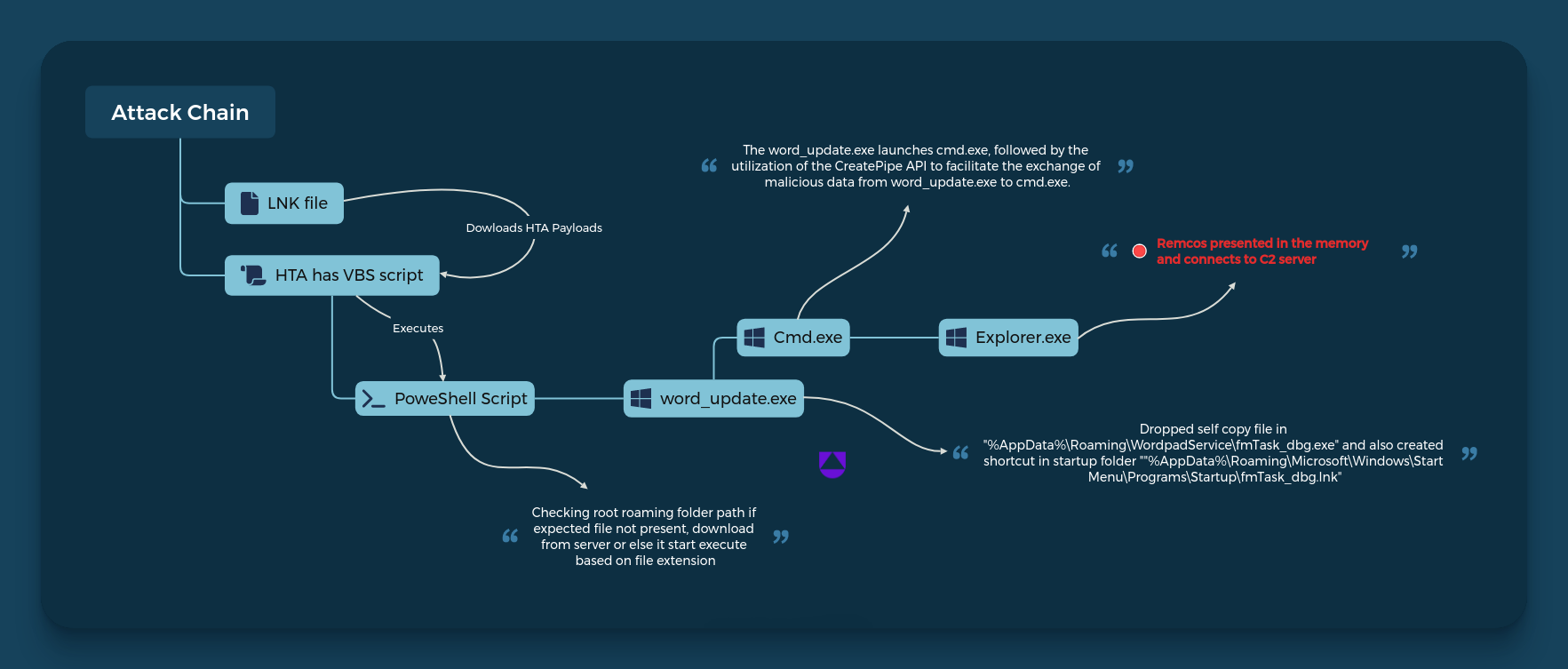
The hacker collective known as UAC-0050 has been actively employing phishing attacks to disseminate the malicious software Remcos RAT. This software is designed for remote surveillance and control and plays a pivotal role in...
A Nigerian citizen was apprehended in Ghana for orchestrating a sophisticated fraud scheme involving Business Email Compromise (BEC), which led to a U.S. charity organization incurring losses exceeding $7.5 million. Olusegun Samson Adejorin was...
In an audacious cyberattack on the Spanish telecommunications operator Orange Spain, a disruption in internet connectivity ensued. The attack was executed by hacking into the company’s account at RIPE (Réseaux IP Européens Network Coordination...
The American cybersecurity firm Mandiant, a subsidiary of Google, suffered a breach of its account, which was utilized for orchestrating a cryptocurrency scam. The malefactor renamed the account to @phantomsolw and disseminated fraudulent claims...
Cybernews specialists identified two BMW subdomains vulnerable to an exploit allowing malicious actors to redirect users to harmful websites. This vulnerability, named SAP Redirect, affected SAP NetWeaver Application Server Java web servers, enabling the...
The British corporation Radioactive Waste Management (RWM), responsible for handling the nation’s radioactive waste, faced an attempted cyberattack through the professional networking platform LinkedIn. Although unsuccessful, this attempt has stirred concerns in the nuclear...
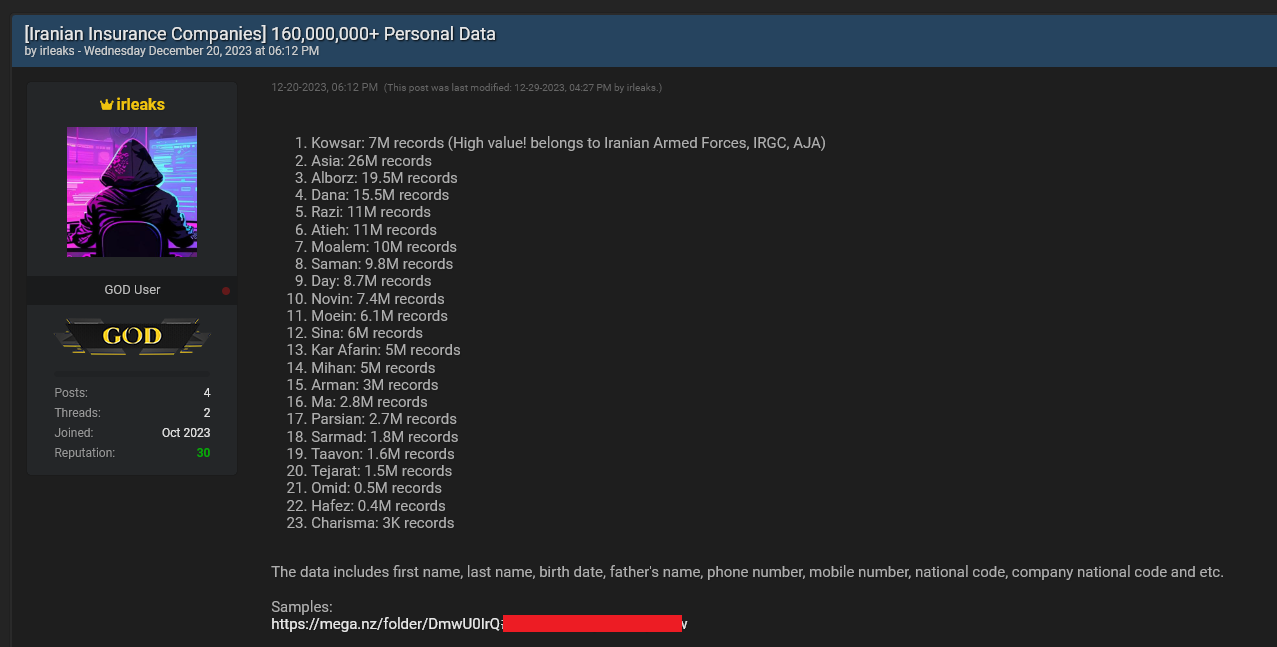
The Israeli cybersecurity firm Hudson Rock has unveiled a series of expansive cyberattacks targeting major Iranian insurance services and online food ordering platforms, significantly impacting a substantial portion of Iran’s 88-million-strong population. According to...
Xerox Corporation has disclosed a cyberattack on its subsidiary XBS, which potentially compromised the personal information of employees and clients. Official confirmation followed shortly after the hacker group INC claimed responsibility for the cyber...