Daily Discovery: Hundreds of IPs Targeting Apache RocketMQ’s RCE Vulnerabilities
The ShadowServer platform daily uncovers hundreds of IP addresses scanning or attempting to exploit Apache RocketMQ services vulnerable to Remote Code Execution (RCE), identified as CVE-2023-33246 and CVE-2023-37582. Both vulnerabilities are critical and pertain to an issue that remained active following the initial fix released by the provider in May 2023.
The security issue was originally tracked as CVE-2023-33246 (CVSS score: 9.8) and affected multiple components, including NameServer, Broker, and Controller. Apache issued a patch, but it was incomplete for the NameServer component in RocketMQ, and the flaw continued to impact versions 5.1 and earlier.
The Apache RocketMQ NameServer, Broker, and Controller components, accessible from external networks, lack permission checks. A cybercriminal could exploit the vulnerability to execute arbitrary commands as the system user operating RocketMQ. A hacker might trigger the flaw using the configuration update function or forging RocketMQ protocol content.
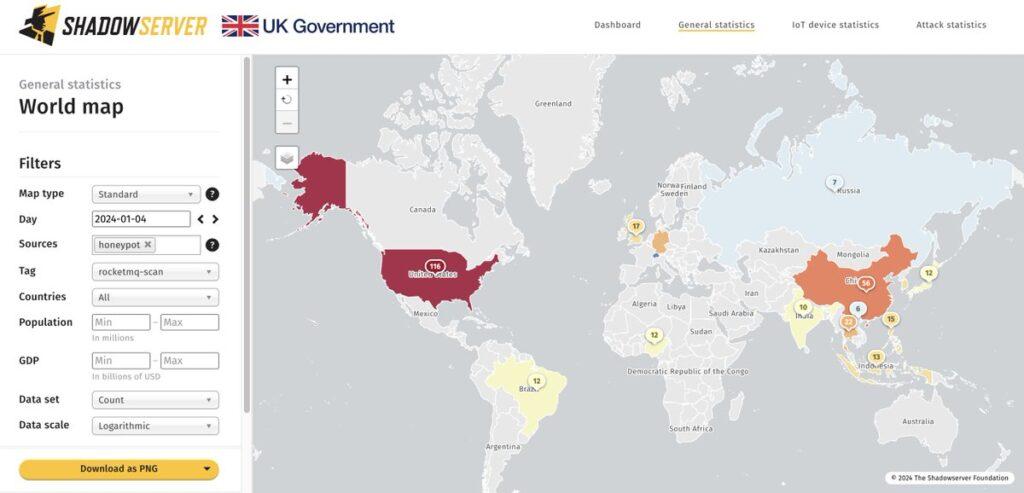
Image: Shadowserver
The issue now bears the identifier CVE-2023-37582 (CVSS score: 9.8). Users are advised to update NameServer to version 5.1.2/4.9.7 or later for RocketMQ 5.x/4.x to avoid attacks exploiting this vulnerability.
The ShadowServer Foundation has recorded over 500 hosts scanning internet-accessible RocketMQ systems, some attempting to exploit both vulnerabilities. Most detected hosts are in the USA, China, Thailand, and the UK. ShadowServer states that the observed activity could be part of reconnaissance efforts, exploitation, or research activities scanning open endpoints.
Hackers began targeting vulnerable Apache RocketMQ systems at least since August 2023, when a new version of the DreamBus botnet was noticed using the CVE-2023-33246 exploit to deploy XMRig miners on susceptible servers. In September 2023, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) urged federal agencies to patch the vulnerability by month’s end, alerting them to its active exploitation status.





