The Stealthy Strategy of UAC-0050: Remcos RAT in the World of Cyber Surveillance
The hacker collective known as UAC-0050 has been actively employing phishing attacks to disseminate the malicious software Remcos RAT. This software is designed for remote surveillance and control and plays a pivotal role in the group’s espionage arsenal, as noted by security researchers from Uptycs.
Since 2020, UAC-0050 has been aggressively targeting Ukrainian and Polish organizations, utilizing social engineering and masquerading as legitimate entities. In February, cybersecurity experts from the targeted countries linked this group to a phishing campaign delivering Remcos RAT.
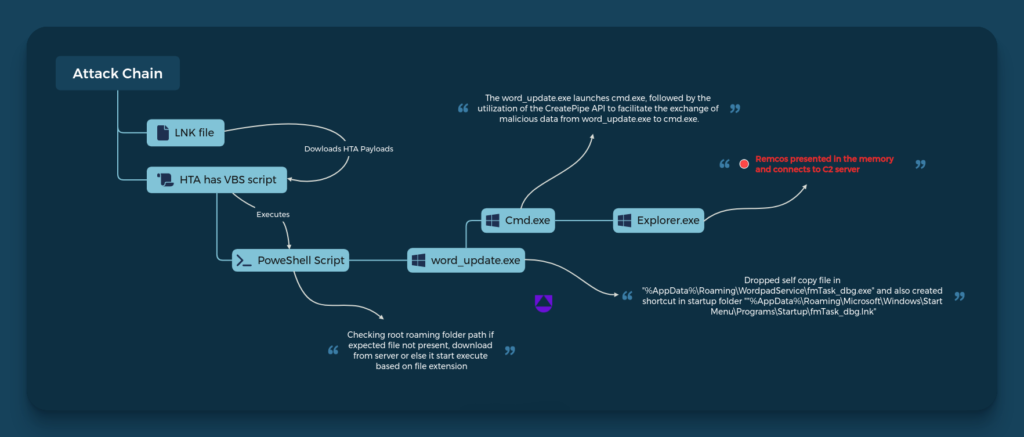
RemcosRAT workflow | Image: Uptycs
The analysis by Uptycs is based on an LNK file discovered at the end of December. This file gathers information about the presence of antivirus software on the infected computer. It activates a PowerShell script to download and launch Remcos RAT, capable of collecting system data and login information from web browsers like Internet Explorer, Mozilla Firefox, and Google Chrome.
Over the past few months, this same Trojan has been used in at least three different phishing waves, with one attack also leading to the deployment of an information-stealing program named Meduza Stealer.
A novel tactic of the UAC-0050 group involves the use of so-called “Unnamed Pipes” in the Windows operating system for data transmission. This allows for surreptitious circumvention of incident detection and response systems, as well as antivirus software.
Researchers note that while the technique used by the group is not new, it demonstrates a significant escalation in the complexity of UAC-0050’s hacking strategies.





