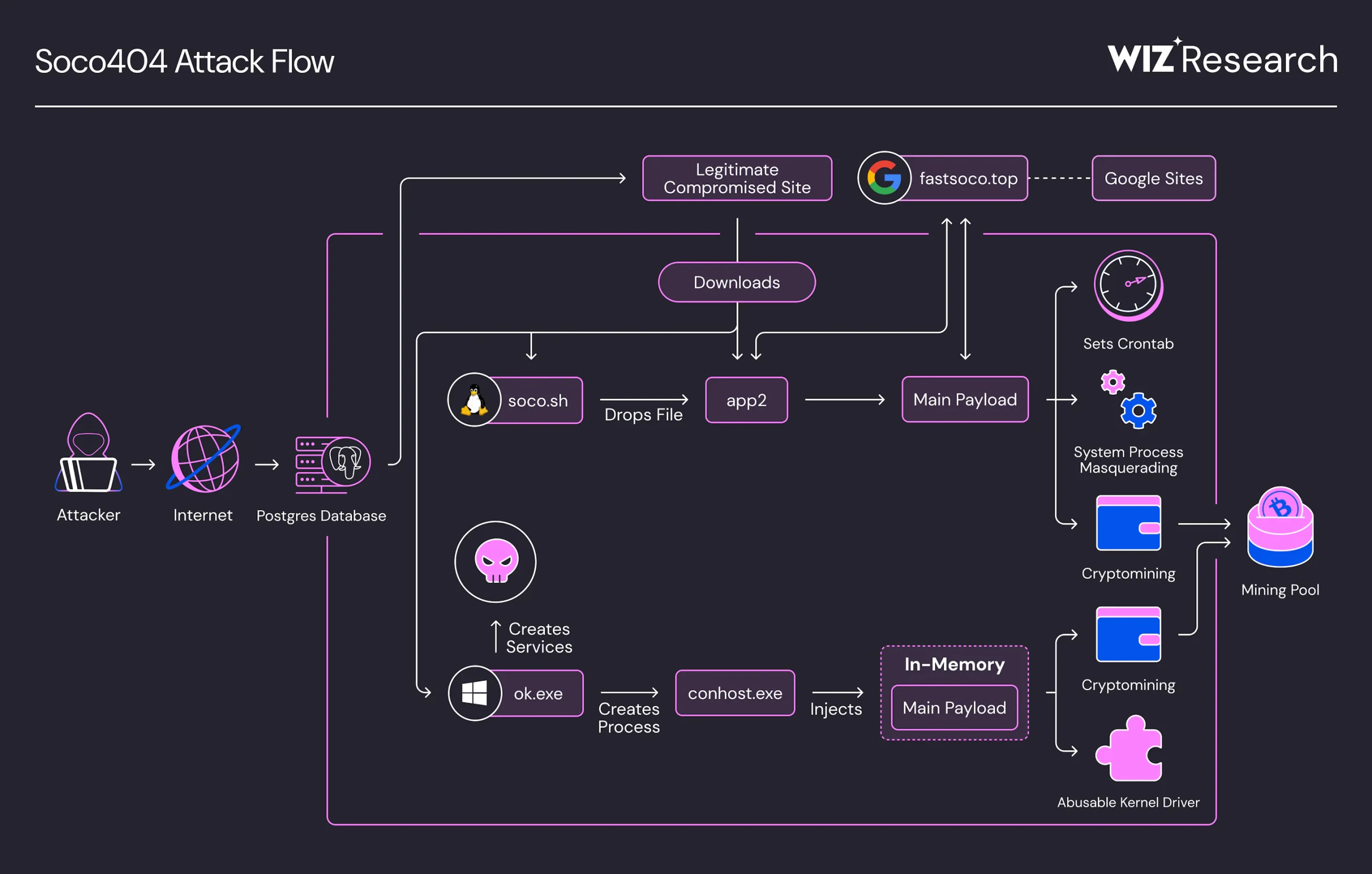
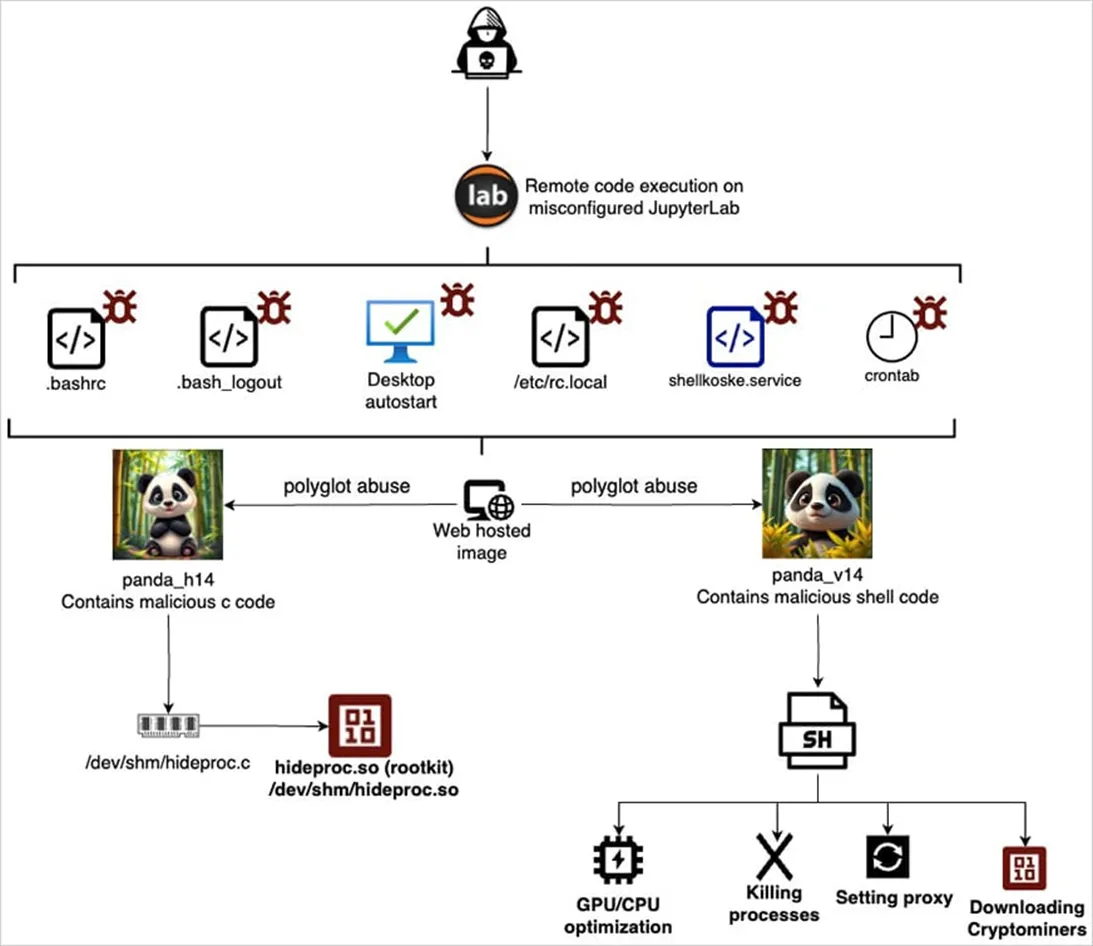
ArmouryLoader: New Sophisticated Malware Evades EDRs by Exploiting ASUS Gaming Software and OpenCL GPU Decryption
ArmouryLoader has once again captured the attention of cybersecurity experts, emerging as one of the most technically sophisticated malware loaders in recent memory. Its architecture reflects a mature approach to evading defenses, employing stealthy...