Cybercriminals are mastering increasingly sophisticated methods of delivering malicious code, leveraging unconventional file formats to evade security defenses. A recent case documented by researchers illustrates how a seemingly innocuous audio message in WAV format can serve as a covert weapon, targeting users who place trust in corporate-branded communications.
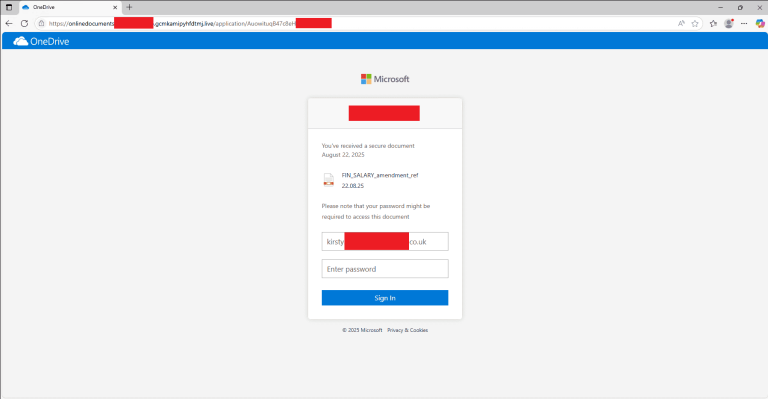
Attackers distribute emails disguised as voicemail notifications from VoIP systems, each bearing an attached WAV file. At first glance, it appears to be nothing more than a recorded call. When played, the audio features a voice allegedly from a Veeam Software employee, informing the recipient of an expired license and urging a callback. The entire setup is crafted to evoke urgency and credibility—deliberately engineered to provoke action. Yet the real threat lies not in the spoken message, but within the audio file itself.
Cybersecurity expert Xavier Mertens warns that WAV files can harbor malicious code embedded through techniques such as steganography. This allows commands to be executed upon opening the file without raising suspicion. The potential consequences are severe—ranging from remote code execution and ransomware installation to the theft of sensitive data and system persistence via registry modifications.
The example email contained no personalized greeting and was sent to a recipient with no affiliation to IT or Veeam, suggesting a broad-scale campaign aimed at a wide audience. Such a strategy reduces the complexity of execution while maximizing reach—bots can disseminate thousands of these messages through compromised mail servers.
The choice of the Veeam brand is deliberate—renowned for its expertise in backup and data protection, the company inspires inherent trust, particularly in corporate settings. Users are far more likely to lower their guard when interacting with names they associate with reliability and security.
Particularly concerning is the chosen vector of attack. WAV files are generally perceived as harmless and thus bypass most email filters, which are typically configured to flag executable files such as EXE or DLL. This renders audio files potentially more dangerous than traditional attachments. Analysts are noting an uptick in the use of multimedia formats—WAV, MP3, MP4—as attack vectors due to their compact size and cross-platform compatibility.
Technical analysis reveals that malicious attachments may trigger PowerShell scripts or contain macros capable of infiltrating local networks, exfiltrating data, or maintaining persistence even after a system reboot.
Given this emerging threat landscape, enterprises are urged to reevaluate their defensive posture. This includes deploying advanced email filtering systems powered by behavioral analysis and machine learning, enforcing multi-factor authentication, and training employees to identify suspicious messages. Above all, caution should be exercised with unexpected attachments—even when they appear benign or originate from seemingly trustworthy sources.
While no widespread infections linked to this particular campaign have been reported thus far, its emergence signals a new wave of phishing attacks—blending social engineering with technical subterfuge. Such tactics, if proven effective, could quickly escalate into large-scale threats.