Warning: Infected Documents Target Ukraine
Since 2015, certain Ukrainian government networks have remained infected with a malicious program known as OfflRouter. Researchers from Cisco Talos have analyzed over 100 infected documents, which enabled them to identify the virus’s ongoing activity within Ukraine.
A unique characteristic of OfflRouter is its inability to spread via email; instead, the virus is transmitted solely locally through document exchanges on removable media such as USB drives. This mode of transmission limits its impact to Ukraine alone, though it significantly reduces the number of affected organizations.
“The virus is still active in Ukraine and is causing potentially confidential documents to be uploaded to publicly accessible document repositories,” stated Vanya Swaiser, a security researcher from Cisco Talos.
Currently, it is unknown who is responsible for this malware. Researchers have not found any indications of whether it was developed within Ukraine or externally. Whoever the creator, they are described as quite inventive, albeit inexperienced due to several errors in the source code and imperfect coverage of the attack.
The OfflRouter malware has been detected by various security organizations. In 2018, it was first reported by MalwareHunterTeam, and in 2021, experts from CSIRT.SK provided information about infected files directly to the website of Ukrainian cyber specialists.
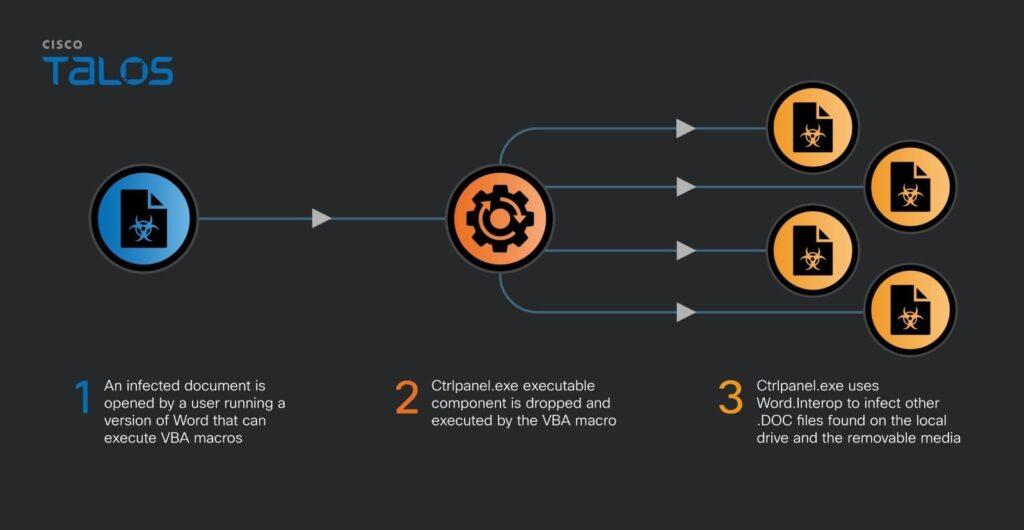
Yet, three years later, the malware continues to function successfully within the government networks of the country, and its malicious code and operation principle have remained unchanged: VBA macros embedded in Microsoft Word documents, when an infected document is opened, drop an executable .NET file named “ctrlpanel.exe,” which then infects all “.doc” files found on the computer and connected removable media, sparing “.docx” and any other file formats.
It is peculiar that the focus is solely on “.doc” files, significantly reducing the number of potentially useful documents that could be exfiltrated by the attackers. This is probably what Talos experts were referring to when they mentioned the imperfect attack coverage.
One of the features of OfflRouter is its ability to make changes in the Windows system registry to automatically launch the malicious module at every system start. This, along with external modules waiting on removable media, allows the virus to spread effectively and remain undetected.
Additionally, when infecting documents, the virus uses complex methods to check already infected files, which eliminates the likelihood of reinfection.
It is noteworthy that in relatively recent editions of Microsoft Office, distributed in recent years, Microsoft has started to block macros by default, requiring the victim to manually activate them to infect their computer.
Nevertheless, in many Ukrainian organizations, including government ones, older versions of Microsoft Office may still be used, which could mean continued activity of OfflRouter until cyber experts address this issue thoroughly.
Moreover, attackers have long employed cunning social engineering tricks, such as displaying fake notifications that the file content cannot be viewed until macros are enabled. All this is done merely to circumvent Microsoft’s restrictions and successfully infect the target computer.
The situation with OfflRouter demonstrates the necessity for continuous modernization of protective measures, closer cooperation among cybersecurity experts, and software updates in governmental structures to counter evolving threats.





