Unmasking the New DLL Hijacking Variant Targeting Windows Users
The cybersecurity firm Security Joes has identified a new variant of the DLL search order hijacking method, which could be exploited by malevolent actors to circumvent protective mechanisms and execute malicious code on systems operating under Windows 10 and Windows 11.
According to Security Joes’ report, this novel approach involves utilizing executable files from the trusted WinSxS folder and exploiting them through the classical technique of DLL search order substitution. This method allows a cybercriminal to bypass the need for privilege escalation when attempting to launch malicious code on a compromised computer, and to inject potentially vulnerable binary files into the attack chain.
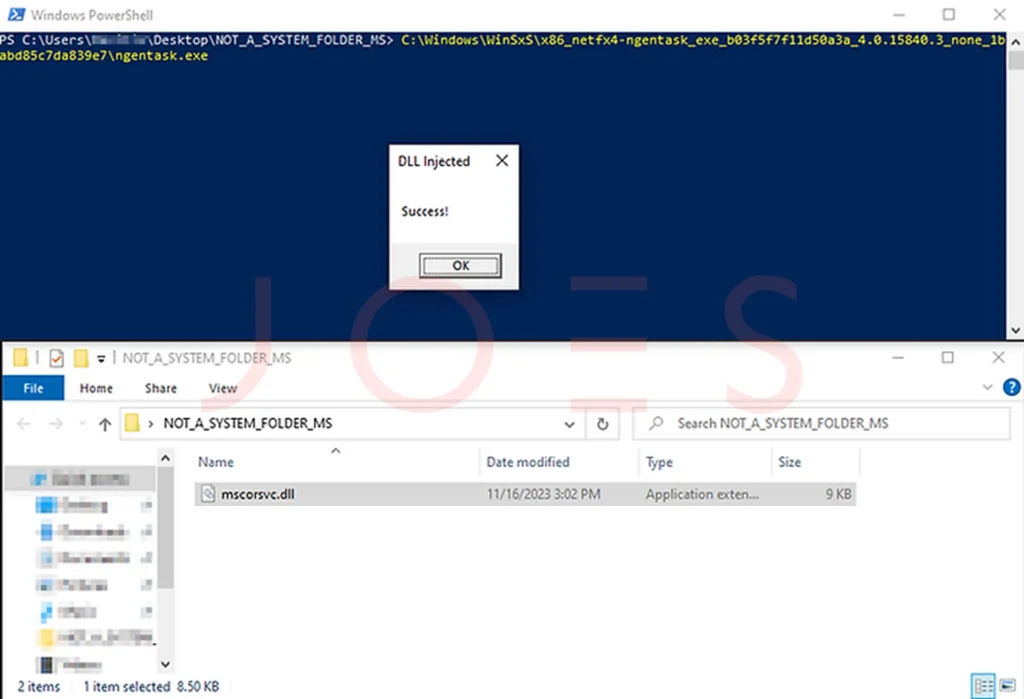
Example of a successful DLL Search Order Hijacking abusing a binary in the WinSxS folder
The DLL search order hijacking technique entails manipulating the search order used for loading DLLs, to execute malicious payloads to circumvent security, maintain persistence, and escalate privileges. Such attacks target applications that do not specify the complete path to their required libraries, instead relying on a predefined search order to locate necessary DLLs on the disk.
Malefactors exploit this behavior by relocating legitimate system binary files to non-standard directories, which contain malicious DLLs with names matching those of legitimate ones, thus leading to the selection of the malicious library instead of the real DLL.
Security Joes warns that there may be more binary files in the WinSxS folder susceptible to such DLL search order hijacking, necessitating organizations to take appropriate precautionary measures to prevent the exploitation of this method in their environments.
The company advises close monitoring of all activities carried out by binary files located in the WinSxS folder, focusing on both network communications and file operations.





