Tycoon 2FA: The Tool Bypassing Your 2-Factor Authentication
Cybercriminals are increasingly leveraging the new phishing platform Tycoon 2FA to compromise Microsoft 365 and Gmail accounts, circumventing two-factor authentication. This trend was identified by experts at Sekoia.
Tycoon 2FA was discovered in October 2023, but malefactors began utilizing it in August. At that time, the hacking group Saad Tycoon started offering their product in private Telegram channels. Essentially, the service operates on a “phishing-as-a-service” model, meaning it is provided to other criminals for rent.
In 2024, a new, more clandestine version of Tycoon 2FA was released, indicating the developers’ ongoing efforts to refine it. Currently, the service employs 1100 domains and has been implicated in thousands of phishing attacks.
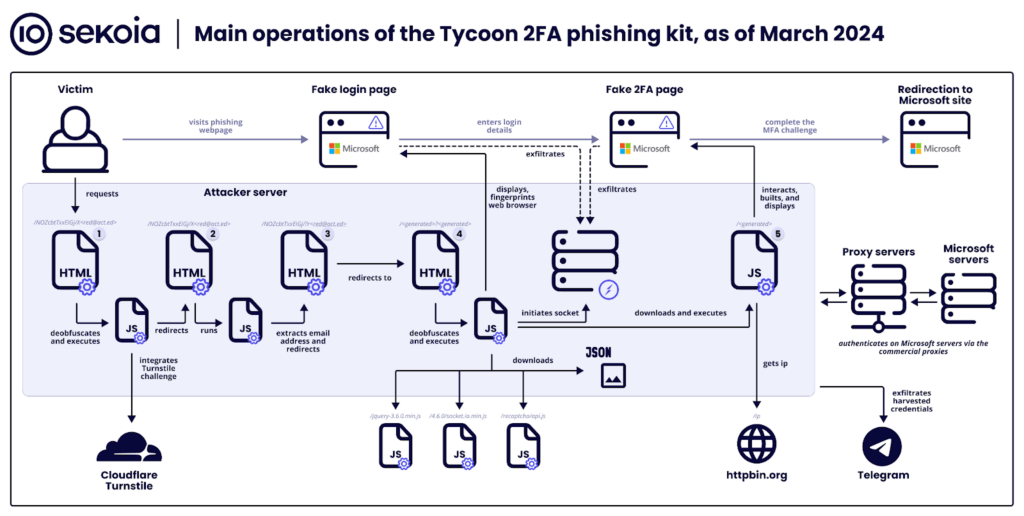
Overview of the main operations specific to the Tycoon 2FA phishing kit, as of March 2024
The attacks using Tycoon 2FA unfold in several stages:
- Criminals distribute malicious links or QR codes via email (thus luring victims to phishing sites).
- The platform filters bots using the Cloudflare Turnstile protective mechanism, allowing only real users.
- The victim’s email is extracted from the URL for attack personalization.
- Users are redirected to another phishing page.
- A counterfeit Microsoft account login page is displayed to steal credentials.
- The platform shows a fake 2FA page to intercept the one-time code and bypass two-factor authentication.
- Individuals are redirected back to the legitimate site to conceal the attack’s traces.
According to Sekoia, the Tycoon 2FA phishing kit bears similarities to other phishing platforms like Dadsec OTT, suggesting code reuse or collaboration among developers.
The proliferation of Tycoon 2FA is significant: since October 2019, over $394,000 in cryptocurrency has flowed into the operators’ crypto wallet, with a substantial influx of funds noted since August 2023—the platform’s launch. In just the first 10 days after its release in August, hackers received more than 530 transactions worth over $120 each.
Analysts assert that the latest version of Tycoon 2FA has been considerably improved by its creators. They modified the code in JavaScript and HTML, revised the resource loading order, and enhanced bot filtering.
For instance, malicious resources are now loaded only after successfully passing the Cloudflare Turnstile check. Additionally, to hide their activity, malefactors use pseudo-random URLs.
In the new version of Tycoon 2FA, mechanisms for recognizing and blocking traffic from the anonymous Tor network and data center IP addresses have been improved. The platform now blocks certain user-agent headers that detection tools could use.





