Tesla Modem Compromised: Researchers Win $722,500 at Pwn2Own Automotive 2024
Security researchers hacked a Tesla car modem and received a total reward of $722,500 on the first day of the Pwn2Own Automotive 2024 competition, currently taking place in Tokyo. Today, white-hat hackers discovered no fewer than 24 zero-day vulnerabilities.
The Synacktiv team earned $100,000 by successfully combining three zero-day vulnerabilities to gain root access to the Tesla car modem. This allowed the white-hat hackers to gain full control over the device and demonstrate the potential for system compromise.
Furthermore, Synacktiv utilized two unique chains of two vulnerabilities each to hack the Ubiquiti Connect EV charging station and the JuiceBox 40 Smart EV charger, earning an additional $120,000. These attacks also highlighted serious security flaws in popular models of electric vehicle charging devices.
Another exploit chain targeting the ChargePoint Home Flex EV charger, already known, still brought the team $16,000 in cash. In total, on the first day of the contest, hackers from Synacktiv garnered $295,000 in prizes.
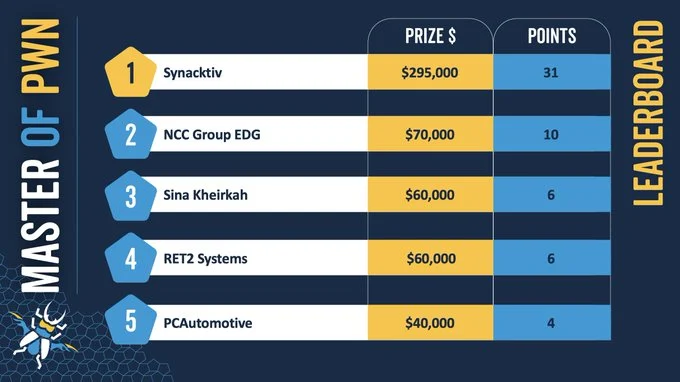
Leaderboard for the first day of Pwn2Own Automotive 2024
Security researchers also successfully hacked several fully updated electric vehicle charging stations and multimedia systems from other manufacturers. The NCC Group EDG team came in second on the leaderboard, receiving $70,000 for exploiting zero-day vulnerabilities to hack the Pioneer DMH-WT7600NEX multimedia system and the Phoenix Contact CHARX SEC-3100 EV charger.
The results from the first day of Pwn2Own demonstrate that even modern software and equipment in the electric vehicle sector contain serious vulnerabilities that could be exploited by malicious actors. However, the timely discovery of such vulnerabilities is not impossible; it only requires gathering dozens of hackers in one place and setting a specific task.
After demonstrating exploits as part of the Pwn2Own contest, manufacturers have 90 days to develop and release security patches before the details of the discovered vulnerabilities are publicly disclosed through Trend Micro’s Zero Day Initiative.
This approach gives manufacturers sufficient time to address vulnerabilities in their products before they can be exploited by malicious actors, while also ensuring they do not delay the release of fixes for an extended period.
Pwn2Own Automotive 2024 is taking place this week in Tokyo as part of the Automotive World conference. During the competition, cybersecurity researchers will attack various automotive technologies, including multimedia systems, car operating systems, charging stations, etc.
The grand prize — $200,000 and a Tesla Model 3 — will be awarded for demonstrating zero-day vulnerabilities in VCSEC systems, the gateway, or autopilot.
Last year, during the Pwn2Own Vancouver 2023 contest, cybersecurity researchers collectively earned $1,035,000 and a Tesla Model 3 after demonstrating 27 zero-day vulnerabilities and several additional exploit chains.
Via: bleepingcomputer





