Cloudflare Accuses Perplexity AI of Evading Blocks and Impersonating Browsers to Scrape Websites
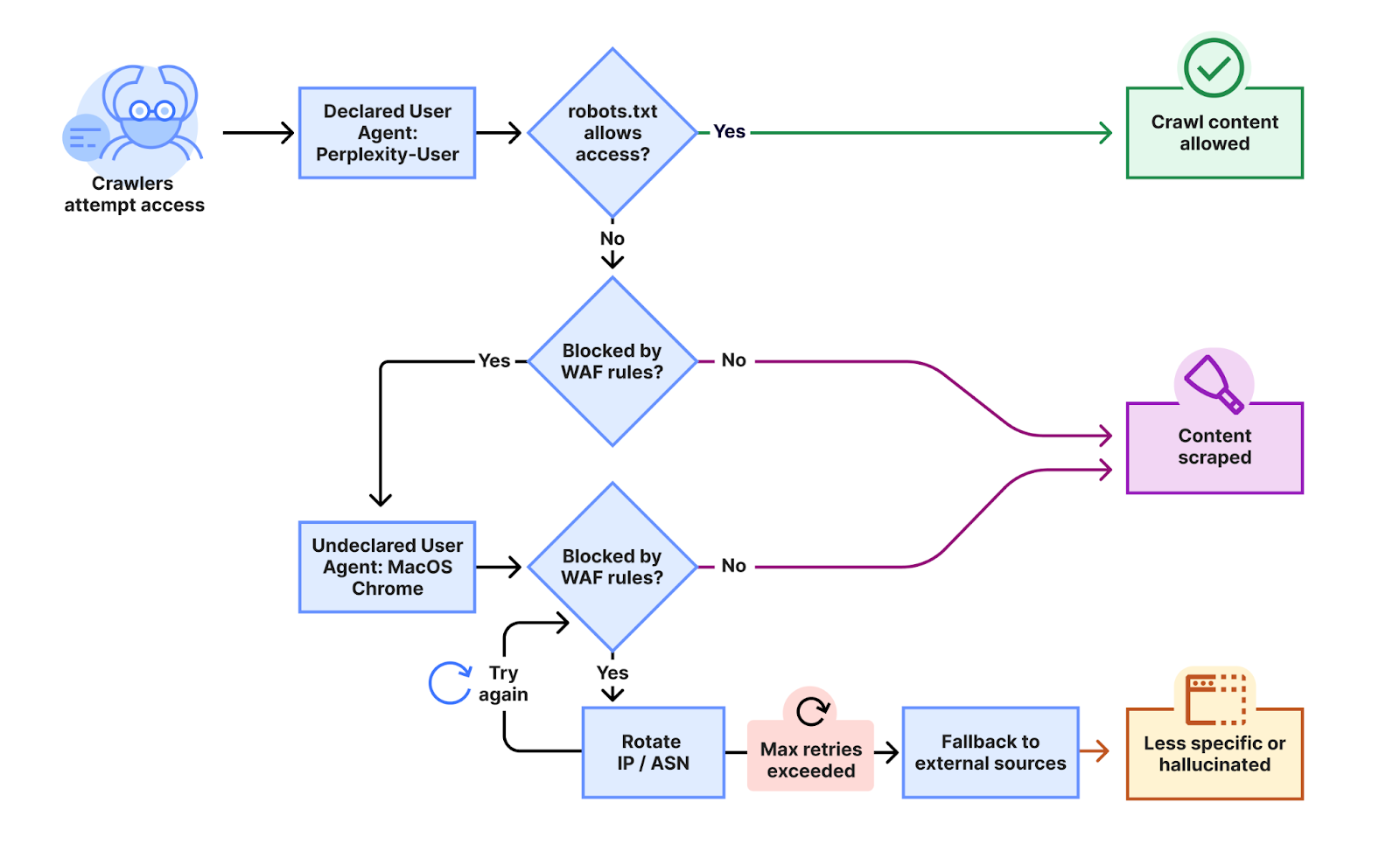
Cloudflare, the company safeguarding millions of websites from digital threats, has issued grave accusations against the AI search engine Perplexity AI. According to their investigation, this popular AI assistant employs covert methods to extract...