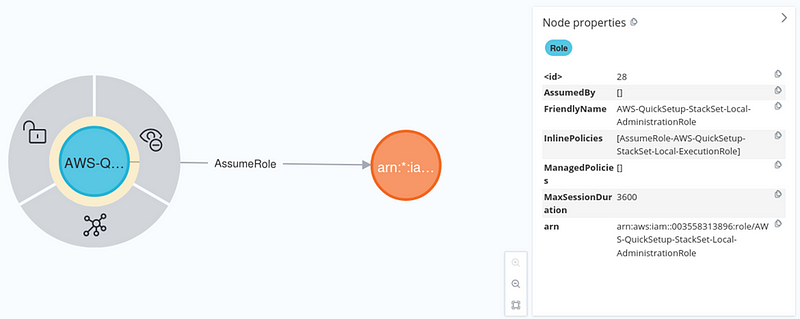
Cloud Chaos: New ‘ECScape’ Attack Threatens Amazon’s Container Service
At the Black Hat USA conference in Las Vegas, Naor Haziz, a researcher at Sweet Security, unveiled an attack dubbed ECScape, capable of completely undermining the trust-based security model of Amazon ECS. The vulnerability...