Sophisticated Phishing Campaign Hits Mexico with TimbreStealer
Since the outset of November 2023, Cisco Talos has reported that Mexican users have been targeted by a sophisticated phishing campaign distributing a novel Windows malware dubbed TimbreStealer.
This phishing initiative employs tax-themed decoy documents and utilizes intricate obfuscation techniques to circumvent detection systems and ensure the persistence of the malware. Additionally, the campaign leverages geofencing to exclusively target users within Mexico. Attempts to access malicious sites from other regions result in the delivery of a harmless, empty PDF document instead of the malware.
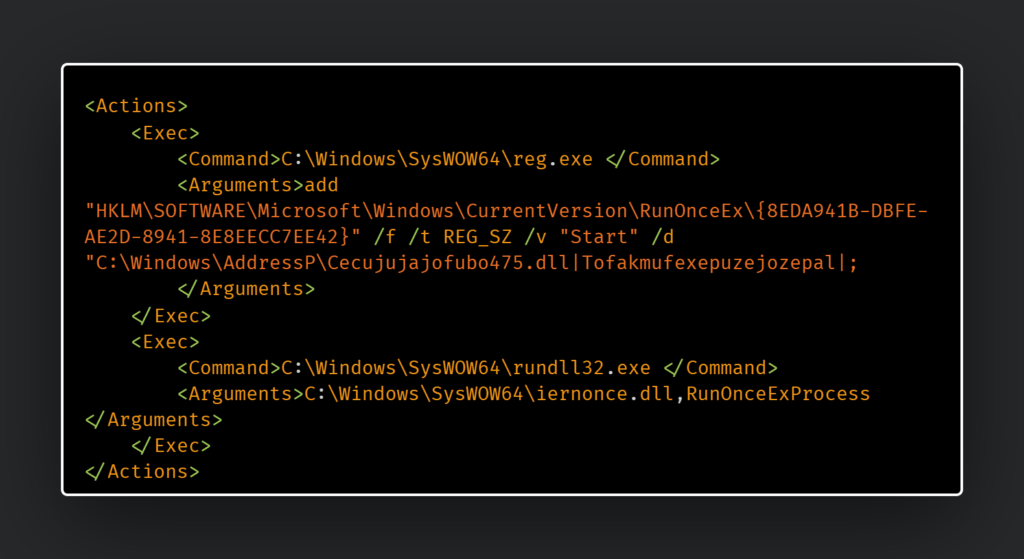
Scheduled Task configuration to run the installed DLL
Notable tactics include the use of custom loaders and direct system calls to evade API monitoring, along with Heaven’s Gate – a technique enabling the malware to bypass endpoint security measures by executing 64-bit code within 32-bit Windows processes, effectively circumventing user hooks. This latter method has also been adopted by other malicious software, such as HijackLoader.
TimbreStealer encompasses several embedded modules for orchestration, decryption, and protection of its core binary. It conducts a series of checks to ensure it is not operating within a virtualized environment and that the system’s timezone aligns with the Latin American region.
The primary objective of this malware is to harvest a broad spectrum of data, including account information from various folders, system metadata, visited URLs, searches for files with specific extensions, and checks for remote access software. Notably, TimbreStealer targets a diverse array of industries, including the manufacturing and transportation sectors.
In a related development, experts from Palo Alto Networks’ Unit 42 recently identified attacks on Mexican users perpetrated using the Mispadu trojan, aimed at pilfering banking data. First identified in 2019, this virus spreads through phishing messages and exploits a vulnerability in Windows SmartScreen, which was rectified in November 2023.





