Silver SAML: New Attack Bypasses Identity Defenses
Semperis has unveiled a novel attack technique named Silver SAML, capable of circumventing protection in identification systems. Silver SAML enables the utilization of SAML to initiate attacks from the identity provider’s side (such as Entra ID) against applications employing Entra ID for authentication (for instance, Salesforce).
It’s noted that Silver SAML bears similarities to the Golden SAML technique, first documented by CyberArk in 2017. The attack vector involves exploiting a compatible authentication standard to impersonate virtually any individual within an organization.
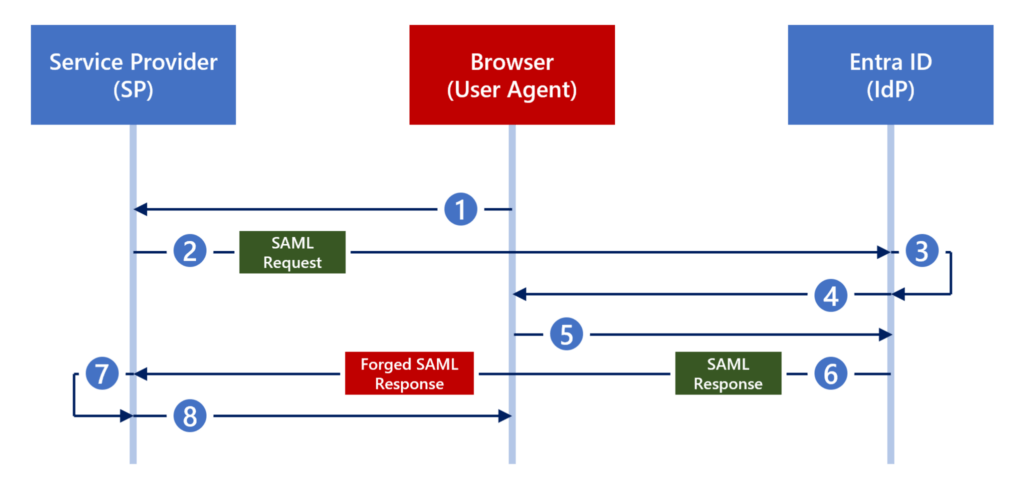
Silver SAML attack in an SP-initiated flow
The Silver SAML attack is a modification of Golden SAML. This technique interfaces with the identity provider Microsoft Entra ID (formerly Azure Active Directory) and does not require access to Active Directory Federation Services (AD FS).
Microsoft, following a responsible disclosure on January 2, 2024, stated that the issue does not meet the criteria for immediate resolution but acknowledged that they would take appropriate actions as necessary to protect their clients.
Although there is no evidence of Silver SAML being exploited in real-world conditions, organizations are advised to use only self-signed Entra ID certificates for SAML signing. Semperis has also provided a Proof-of-Concept (PoC) named SilverSAMLForger for creating customizable SAML responses.
Semperis elucidates that organizations can monitor Entra ID audit logs for changes in PreferredTokenSigningKeyThumbprint within the ApplicationManagement section. It’s crucial to correlate these events with service principal credential events that pertain to the service principal. Certificate rotation is a standard procedure; thus, determining whether audit events are legitimate is essential. Implementing change control processes to document rotation can help minimize confusion during rotation events.





